Offline - 70-743: Upgrading Your Skills to MCSA: Windows Server 2016
Sample Questions
Question: 637
Measured Skill: Implement identity federation and access solutions
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2016.
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You deploy Active Directory Federation Services (AD FS) and a Web Application Proxy to the Active Directory domain.
You need to configure the AD FS deployment to support Azure Multi-Factor Authentication (MFA) as the primary authentication method.
Which three actions should you perform in sequence on the AD FS server?
(To answer move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)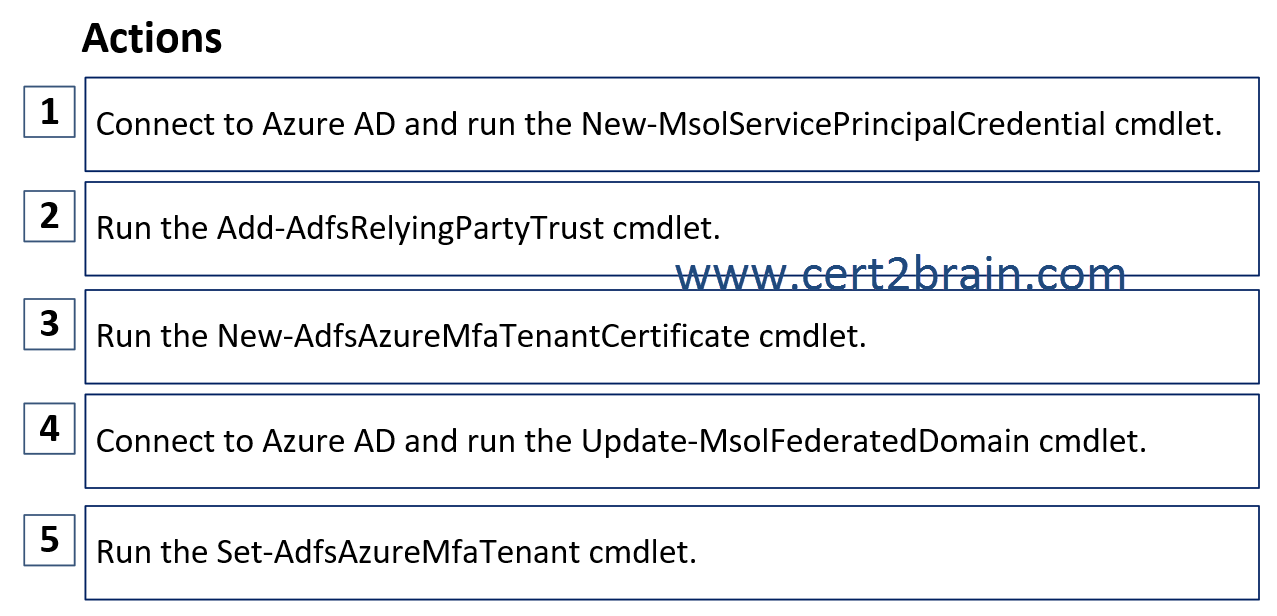
| A | Sequence: 2, 3, 5 |
| B | Sequence: 3, 1, 2 |
| C | Sequence: 3, 1, 5 |
| D | Sequence: 4, 3, 5 |
Correct answer: CExplanation:
If your organization is federated with Azure AD, you can use Azure Multi-Factor Authentication to secure AD FS resources, both on-premises and in the cloud. Azure MFA enables you to eliminate passwords and provide a more secure way to authenticate. Starting with Windows Server 2016, you can now configure Azure MFA for primary authentication.
Unlike with AD FS in Windows Server 2012 R2, the AD FS 2016 Azure MFA adapter integrates directly with Azure AD and does not require an on premises Azure MFA server. The Azure MFA adapter is built in to Windows Server 2016, and there is no need for additional installation.
For a step-by-step configuration guide see:
Configure AD FS 2016 and Azure MFA
Question: 638
Measured Skill: Install and configure Active Directory Domain Services (AD DS)
You plan to deploy a Software Defined Networking (SDN) infrastructure.
Which service provides name resolution for the virtual machines on a tenant network?| A | iSNS |
| B | Network Controller |
| C | A smart host |
| D | iDNS |
Correct answer: DExplanation:
If you work for a Cloud Service Provider (CSP) or Enterprise that is planning to deploy Software Defined Networking (SDN) in Windows Server 2016, you can provide DNS services to your hosted tenant workloads by using Internal DNS (iDNS), which is integrated with SDN.
Hosted virtual machines (VMs) and applications require DNS to communicate within their own networks and with external resources on the Internet. With iDNS, you can provide tenants with DNS name resolution services for their isolated, local name space and for Internet resources.
Because the iDNS service is not accessible from tenant Virtual Networks, other than through the iDNS proxy, the server is not vulnerable to malicious activities on tenant networks.
Following are the key features for iDNS.
- Provides shared DNS name resolution services for tenant workloads
- Authoritative DNS service for name resolution and DNS registration within the tenant name space
- Recursive DNS service for resolution of Internet names from tenant VMs.
- If desired, you can configure simultaneous hosting of fabric and tenant names
- A cost-effective DNS solution - tenants do not need to deploy their own DNS infrastructure
- High availability with Active Directory integration, which is required.
Reference: Internal DNS Service (iDNS) for SDN
Question: 639
Measured Skill: Implement identity federation and access solutions
You have servers that run Windows Server 2016 and devices that run Windows 10 Enterprise. You have a certification authority (CA) that Issued computer certificates to all the servers and devices.
You plan to allow the Windows 10 devices to connect to the network remotely by using VPN device tunnels.
You install the Remote Access server role on a server. From the Routing and Remote Access console, you configure the server for the VPN role.
You need to ensure that the Windows 10 devices can establish the VPN tunnel before users sign in to the devices.
What should you do on the VPN server?| A | Modify the ports properties and add additional SSTP ports. |
| B | Modify the ports properties and add additional IKEv2 ports. |
| C | From Authentication Methods, select Extensible authentication protocol (EAP). |
| D | From Authentication Methods, select Allow machine certificate authentication for IKEv2. |
Correct answer: DExplanation:
Always On VPN gives you the ability to create a dedicated VPN profile for device or machine. Always On VPN connections include two types of tunnels:
Device tunnel connects to specified VPN servers before users log on to the device. Pre-login connectivity scenarios and device management purposes use device tunnel.
User tunnel connects only after a user logs on to the device. User tunnel allows users to access organization resources through VPN servers.
Unlike user tunnel, which only connects after a user logs on to the device or machine, device tunnel allows the VPN to establish connectivity before the user logs on. Both device tunnel and user tunnel operate independently with their VPN profiles, can be connected at the same time, and can use different authentication methods and other VPN configuration settings as appropriate. User tunnel supports SSTP and IKEv2, and device tunnel supports IKEv2 only with no support for SSTP fallback.
User tunnel is supported on domain-joined, nondomain-joined (workgroup), or Azure AD–joined devices to allow for both enterprise and BYOD scenarios. It is available in all Windows editions, and the platform features are available to third parties by way of UWP VPN plug-in support.
Device tunnel can only be configured on domain-joined devices running Windows 10 Enterprise or Education version 1709 or later. There is no support for third-party control of the device tunnel. Device tunnel does not support using the Name Resolution Policy table (NRPT). Device tunnel does not support Force tunnel. You must configure it as Split tunnel.
Device Tunnel Requirements and Features
You must enable machine certificate authentication for VPN connections and define a root certification authority for authenticating incoming VPN connections.
Reference: Configure VPN device tunnels in Windows 10
Question: 640
Measured Skill: Install and configure Active Directory Domain Services (AD DS)
You have a server named Server1 that runs Windows Server 2016. Server1 is a Hyper-V host that hosts a virtual machine named VM1.
Server1 has three network adapter cards that are connected to virtual switches named vSwhitch1, vSwitch2, and vSwitch3.
You configure NIC Teaming on VM1 as shown in the following exhibit.
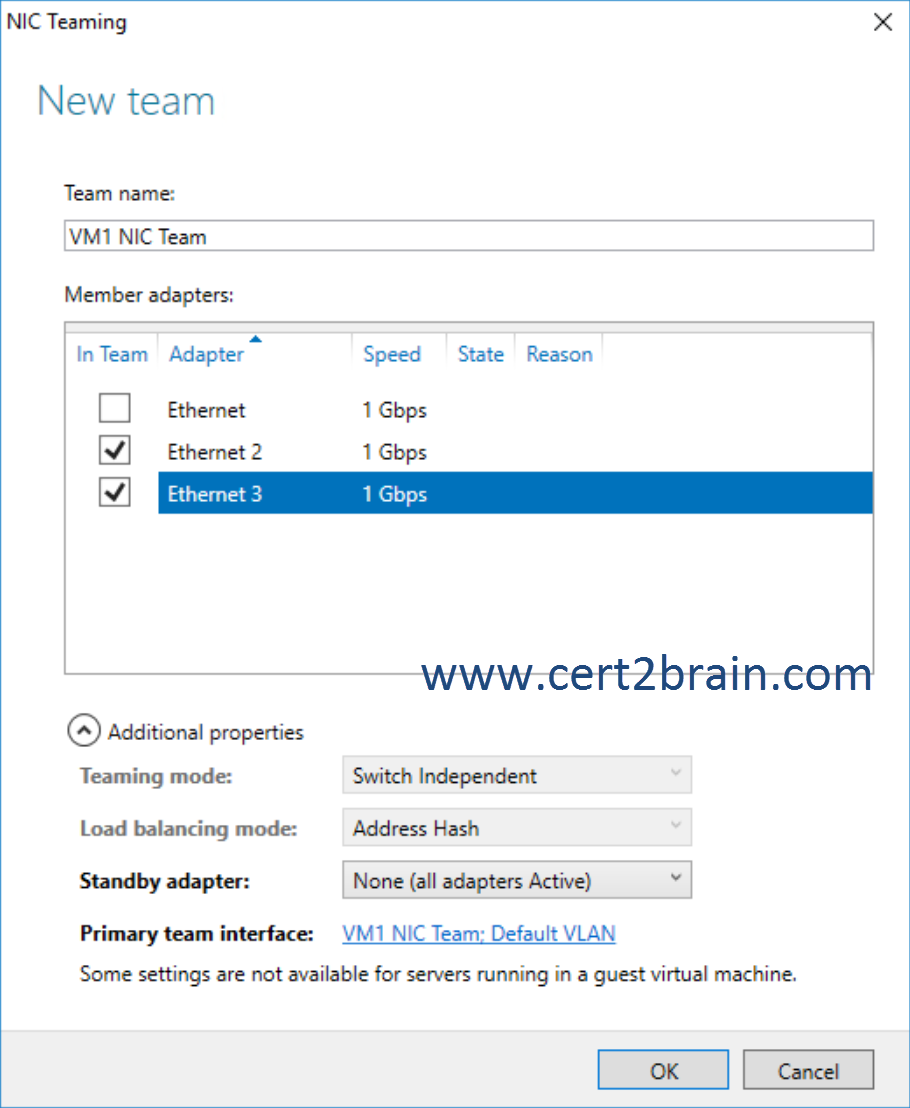
You need to ensure that vm1 will retain access to the network if a physical network adapter card fails on Server1.
What should you do?| A | From the properties of the NIC team on VM1, change the load balancing of the NIC team. |
| B | From Hyper-V Manager on Server1, modify the settings of VM1. |
| C | From Windows PowerShell on Server1, run the Set-VmNetworkAdapterFailoverConfiguration cmdlet. |
| D | From the properties of the NIC team on VM1, add the adapter named Ethernet to the NIC team. |
Correct answer: BExplanation:
The physical switch, Hyper-V Virtual Switch, local area network (LAN), and NIC Teaming requirements for creating a NIC Team in a VM are:
-
The computer running Hyper-V must have two or more network adapters.
-
If connecting the network adapters to multiple physical switches, the physical switches must be on the same Layer 2 subnet.
-
You must use Hyper-V Manager or Windows PowerShell to create two external Hyper-V Virtual Switches, each connected to a different physical network adapter.
-
The VM must connect to both external virtual switches you create.
-
NIC Teaming, in Windows Server 2016, supports teams with two members in VMs. You can create larger teams, but there is no support.
-
If you are configuring a NIC Team in a VM, you must select a Teaming mode of Switch Independent and a Load balancing mode of Address Hash.
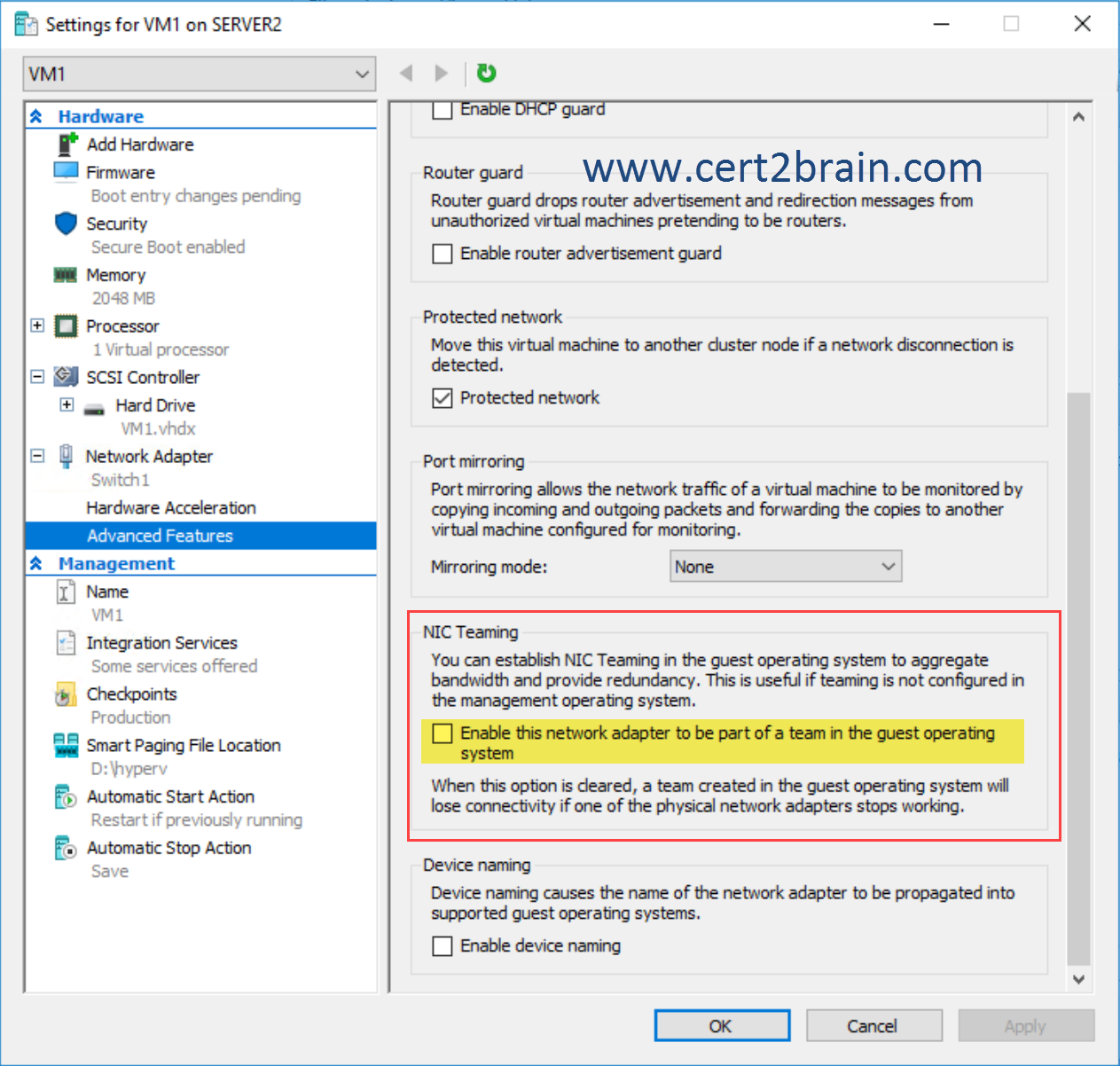
We must enable the Enable this network adapter to be part of a team in the guest operating system option to prevent loss of connectivity if one physical network adapter on the host fails.
Reference: Create a new NIC Team on a host computer or VM
Question: 641
Measured Skill: Implement identity federation and access solutions
Your network contains an Active Directory domain. The domain contains an Active Directory Rights Management Services (AD RMS) cluster.
All client computers run Windows 10 Enterprise.
You need to control from which versions of Windows users can access rights-protected content.
What should you create?| A | A security policy |
| B | A trust policy |
| C | An exclusion policy |
| D | Rights Policy Template |
Correct answer: CExplanation:
You can implement exclusion policies to deny certain entities the ability to acquire certificate and license requests.
There are three ways to exclude these entities:
- by user
- by application
- by lockbox version
The Lockbox property retrieves the minimum lockbox version that must be installed before an end-user license, certificate, or client licensor certificate (CLC) can be granted. The lockbox version depends on the Windows version.