Archive - MD-100: Windows Client
Sample Questions
Question: 403
Measured Skill: Protect devices and data (25-30%)
You have a computer that runs Windows 10.
You need to identify the following information:
- The name, username, and SID of the user who is currently logged on
- The user groups to which the user account belongs
Which command should you run?| A | whoami |
| B | query |
| C | msinfo32 |
| D | userinit |
Correct answer: AExplanation:
code>Whoami displays user, group and privileges information for the user who is currently logged on to the local system. If used without parameters, whoami displays the current domain and user name.
Whoami /all displays all information in the current access token, including the current user name, security identifiers (SID), privileges, and groups that the current user belongs to.
Reference: whoami
Question: 404
Measured Skill: Install and configure Windows (20-25%)
You have a computer named Client1 that runs Windows 10 and has Windows Sandbox enabled.
You create a script named Script1.cmd. On Client1, you save Script1.cmd to a folder named C:\Scripts.
You need to ensure that when you sign in to Windows Sandbox, Script1.cmd runs automatically.
How should you complete the configuration file?
(To answer, select the appropriate options in the answer area. Note: Each correct selection is worth one point.)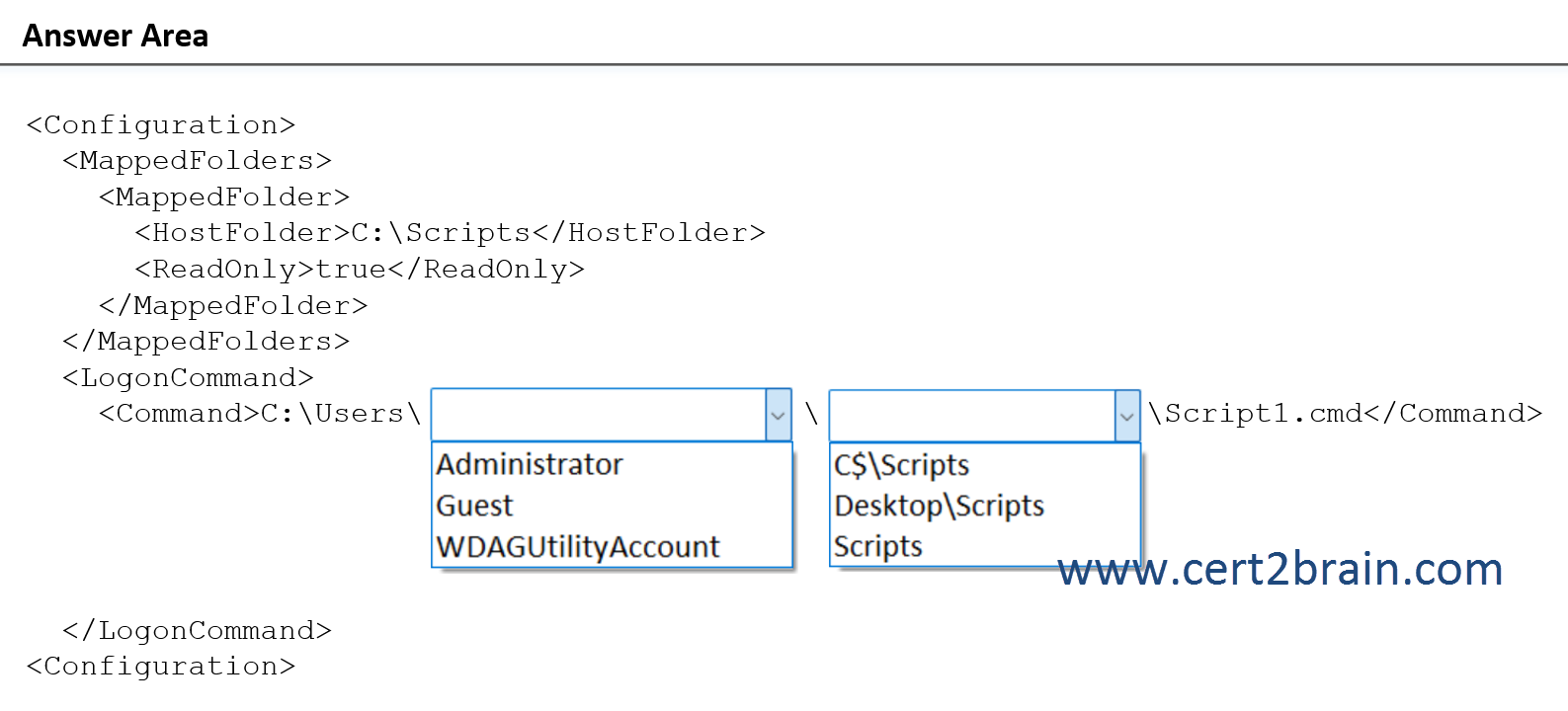
| A | P1: Administrator
P2: C$\Scripts |
| B | P1: Administrator
P2: Desktop\Scripts |
| C | P1: Guest
P2: Scripts |
| D | P1: Guest
P2: C$\Scripts |
| E | P1: WDAGUtilityAccount
P2: Desktop\Scripts |
| F | P1: WDAGUtilityAccount
P2: Scripts |
Correct answer: BExplanation:
Windows Sandbox supports simple configuration files, which provide a minimal set of customization parameters for Sandbox. This feature can be used with Windows 10 build 18342 or Windows 11. Windows Sandbox configuration files are formatted as XML and are associated with Sandbox via the .wsb file extension.
The C:\Scripts folder from the host is mapped to the Sandbox using the MappedFolder element. Because no sandbox folder is specified, the folder will be mapped to the container desktop.
The LogonCommand element specifies a single command that will be invoked automatically after the sandbox logs on. Apps in the sandbox are run under the container user account. The container user account should be an administrator account.
Reference: Windows Sandbox configuration
Question: 405
Measured Skill: Protect devices and data (25-30%)
Your network contains an Active Directory domain. The domain contains the computers shown in the following table.
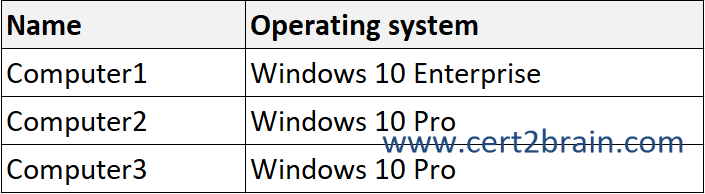
Microsoft Defender Application Guard is installed on the computers.
Application Guard Group Policy settings are applied to the computers as shown in the following table.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
(NOTE: Each correct selection is worth one point.)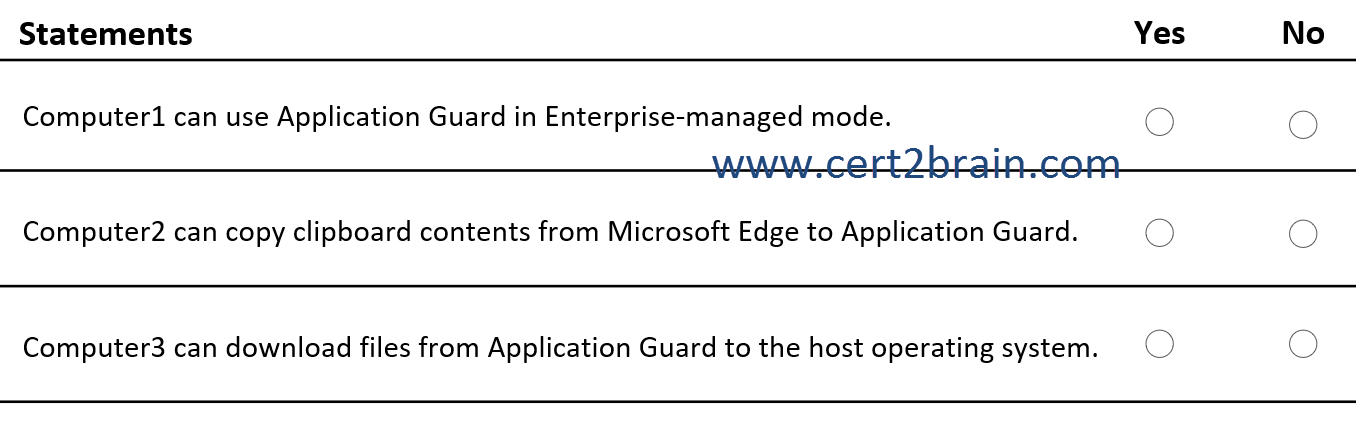
| A | Computer1 can use Application Guard in Enterprise-managed mode: Yes
Computer2 can copy clipboard contents from Microsoft Edge to Application Guard: Yes
Computer3 can download files from Application Guard to the host operating system: Yes |
| B | Computer1 can use Application Guard in Enterprise-managed mode: Yes
Computer2 can copy clipboard contents from Microsoft Edge to Application Guard: Yes
Computer3 can download files from Application Guard to the host operating system: No |
| C | Computer1 can use Application Guard in Enterprise-managed mode: Yes
Computer2 can copy clipboard contents from Microsoft Edge to Application Guard: No
Computer3 can download files from Application Guard to the host operating system: Yes |
| D | Computer1 can use Application Guard in Enterprise-managed mode: No
Computer2 can copy clipboard contents from Microsoft Edge to Application Guard: Yes
Computer3 can download files from Application Guard to the host operating system: Yes |
| E | Computer1 can use Application Guard in Enterprise-managed mode: No
Computer2 can copy clipboard contents from Microsoft Edge to Application Guard: No
Computer3 can download files from Application Guard to the host operating system: Yes |
| F | Computer1 can use Application Guard in Enterprise-managed mode: No
Computer2 can copy clipboard contents from Microsoft Edge to Application Guard: No
Computer3 can download files from Application Guard to the host operating system: No |
Correct answer: CExplanation:
Microsoft Defender Application Guard (Application Guard) is supported on the following operating systems.
- Windows 10 Education, Enterprise, and Professional
- Windows 11 Education, Enterprise, and Professional
For Microsoft Edge, Application Guard helps to isolate enterprise-defined untrusted sites, protecting your company while your employees browse the Internet. As an enterprise administrator, you define what is among trusted web sites, cloud resources, and internal networks. Everything not on your list is considered untrusted. If an employee goes to an untrusted site through either Microsoft Edge or Internet Explorer, Microsoft Edge opens the site in an isolated Hyper-V-enabled container.
For Microsoft Office, Application Guard helps prevents untrusted Word, PowerPoint and Excel files from accessing trusted resources. Application Guard opens untrusted files in an isolated Hyper-V-enabled container. The isolated Hyper-V container is separate from the host operating system. This container isolation means that if the untrusted site or file turns out to be malicious, the host device is protected, and the attacker can't get to your enterprise data. For example, this approach makes the isolated container anonymous, so an attacker can't get to your employee's enterprise credentials.
Allow files to download to host operating system determines whether to save downloaded files to the host operating system from the Microsoft Defender Application Guard container. Enabling this setting allows users to save downloaded files from the Microsoft Defender Application Guard container to the host operating system. This action creates a share between the host and container that also allows for uploads from the host to the Application Guard container.
Configure Microsoft Defender Application Guard clipboard settings determines whether Application Guard can use the clipboard functionality. The default value when enabling this setting ist Block clipboard operations (default).
References:
Microsoft Defender Application Guard overview
System requirements for Microsoft Defender Application Guard
Configure Microsoft Defender Application Guard policy settings
Question: 406
Measured Skill: Protect devices and data (25-30%)
You have 10 computers that run Windows 8.1 and have the following configurations:
- A single MBR disk
- A disabled TPM chip
- Disabled hardware virtualization
- UEFI firmware running in BIOS mode
- Enabled Data Execution Prevention (DEP)
You plan to upgrade the computers to Windows 10.
You need to ensure that the computers can use Secure Boot.
Which two actions should you perform?
(Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.)| A | Enable hardware virtualization. |
| B | Disable DEP. |
| C | Convert the MBR disk to a GPT disk. |
| D | Enable the TPM chip. |
| E | Convert the firmware from BIOS to UEFI. |
Correct answer: C, EExplanation:
When the devices starts, the firmware interface controls the booting process of the PC, and then passes control to Windows or another operating system. UEFI is a replacement for the older BIOS firmware interface and the Extensible Firmware Interface (EFI) 1.
Secure boot is a security standard developed by members of the PC industry to help make sure that a device boots using only software that is trusted by the Original Equipment Manufacturer (OEM).
Secure boot requires an UEFI firmware. Using an UEFI firmware requires the use of the GPT drive format.
References:
Secure boot
United Extensible Firmware Interface (UEFI) firmware requirements
Question: 407
Measured Skill: Install and configure Windows (20-25%)
You have a Windows 10 device.
You need to ensure that only priority notifications are displayed during business hours.
Which settings in the Settings app should you configure, and where will standard notifications be sent during business hours?
(To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.)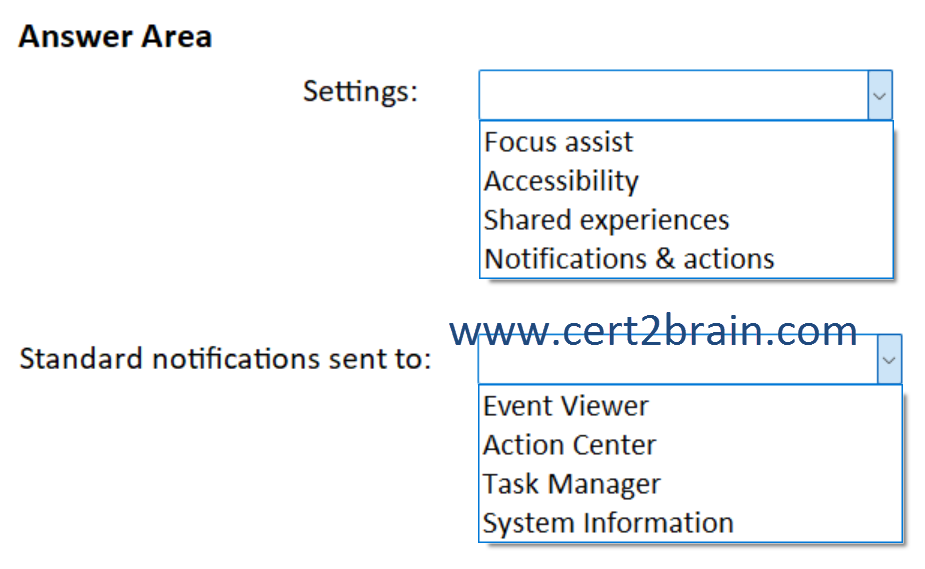
| A | Settings: Focus assist
Standard notifications sent to: Action Center |
| B | Settings: Accessibility
Standard notifications sent to: System Information |
| C | Settings: Shared experiences
Standard notifications sent to: Event Viewer |
| D | Settings: Shared experiences
Standard notifications sent to: Task Manager |
| E | Settings: Notifications & actions
Standard notifications sent to: Event Viewer |
| F | Settings: Notifications & actions
Standard notifications sent to: Action Center |
Correct answer: AExplanation:
We need to configure the Focus assist setting as shown below. Non-priority notifications will go to the action center.
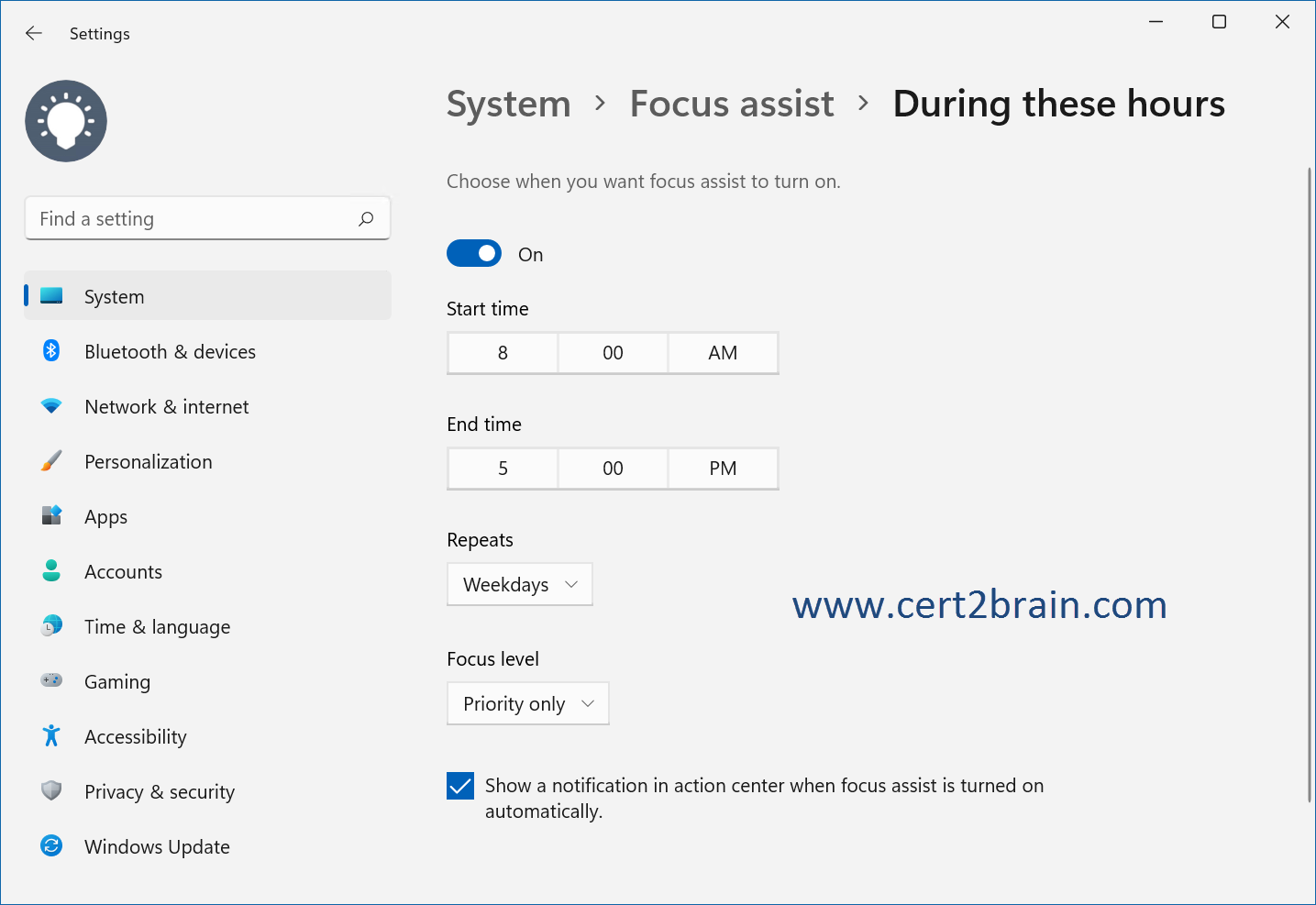
Reference: Make it easier to focus on tasks