|

|
|
|
Archive - 70-744: Securing Windows Server 2016Sample QuestionsQuestion: 237
Measured Skill: Secure a virtualization infrastructure (5–10%)
You have a Hyper-V host named Server1 that runs Windows Server 2016. Server1 has a generation 2 virtual machine named VM1 that runs Windows 10.
You need to ensure that you can turn on BitLocker Drive Encryption (BitLocker) for drive C on VM1.
What should you do?| A | From VM1, configure the Require additional authentication at startup Group Policy setting. | | B | From the settings of VM1, enable Secure Boot. | | C | From Server1, install the BitLocker feature. | | D | From VM1, configure the "Enforce drive encryption type on operating system drives" Group Policy setting. |
Correct answer: AExplanation:
By default, a TPM is required to turn on BitLocker and no additional unlock methods are required. If you want to use BitLocker without a TPM or to require an additional authentication method with the TPM, use the steps in this scenario to configure the settings to support those unlock methods.
To specify how to unlock BitLocker-protected operating system drives
-
Click Start, type gpedit.msc in the Search programs and files box, and then press ENTER.
-
If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Yes.
-
In the console tree under Local Computer Policy\Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption, click Operating System Drives.
-
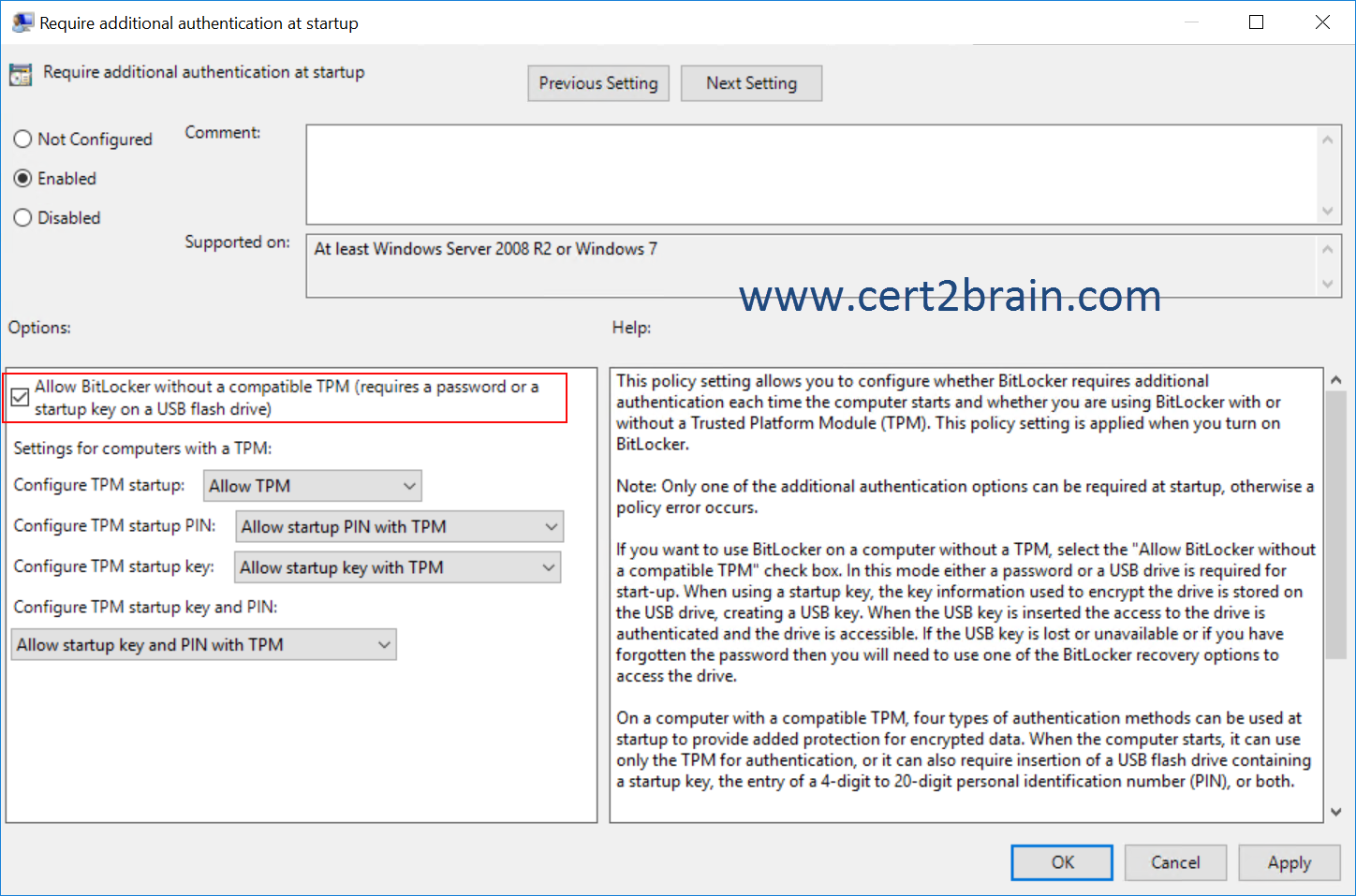
To configure authentication methods in addition to the TPM, in the details pane, double-click Require additional authentication at startup to open the policy setting, and then click Enabled.
-
To support BitLocker on computers running Windows 7 that do not have a TPM, select the Allow BitLocker without a compatible TPM check box.
-
To configure operating system drive startup options for computers with a TPM, the following options are available:
- Configure TPM startup. You can choose to allow, require, or not allow the use of the TPM with BitLocker.
- Configure TPM startup PIN. You can choose to allow, require, or not allow the use of the TPM in combination with a PIN with BitLocker.
- Configure TPM startup key. You can choose to allow, require, or not allow the use of the TPM in combination a key stored on a removable device, such as a USB flash drive with BitLocker.
- Configure TPM startup key and PIN. You can choose to allow, require, or not allow the use of the TPM in combination with both a key stored on a removable device, such as a USB flash drive with BitLocker, and a PIN.
-
After you have made your choices, click Apply to apply the settings, and then close the dialog box.
-
If you are using PINs for authentication along with the TPM, you may want to enable the use of enhanced PINs to allow for increased complexity of PINs. Enhanced PINs support the use of characters, including uppercase and lowercase letters, symbols, numbers, and spaces. Not all computers support these characters before the operating system starts, so we recommend that users perform a system check during BitLocker setup to verify that their computer will support the BitLocker settings they have selected before encrypting the drive. Double-click the Allow enhanced PINs for startup policy setting, and click Enabled to provide the option of using enhanced PINs with BitLocker-protected operating system drives. If this policy setting is disabled or not configured, enhanced PINs cannot be used.
-
After you have made your choices, click Apply to apply the settings, and then close the dialog box.
-
Close the Local Group Policy Editor.
-
To force Group Policy to apply the changes immediately, you can click Start, type gpupdate.exe /force in the Search programs and files box, and then press ENTER. Wait for the process to finish.
 Question: 238
Question: 238
Measured Skill: Implement server hardening solutions (25–30%)
Your network contains an internal network and a perimeter network. The internal network contains an Active Directory forest named contoso.com.
You deploy five servers to the perimeter network. All of the servers run Windows Server 2016 and are the members of a workgroup.
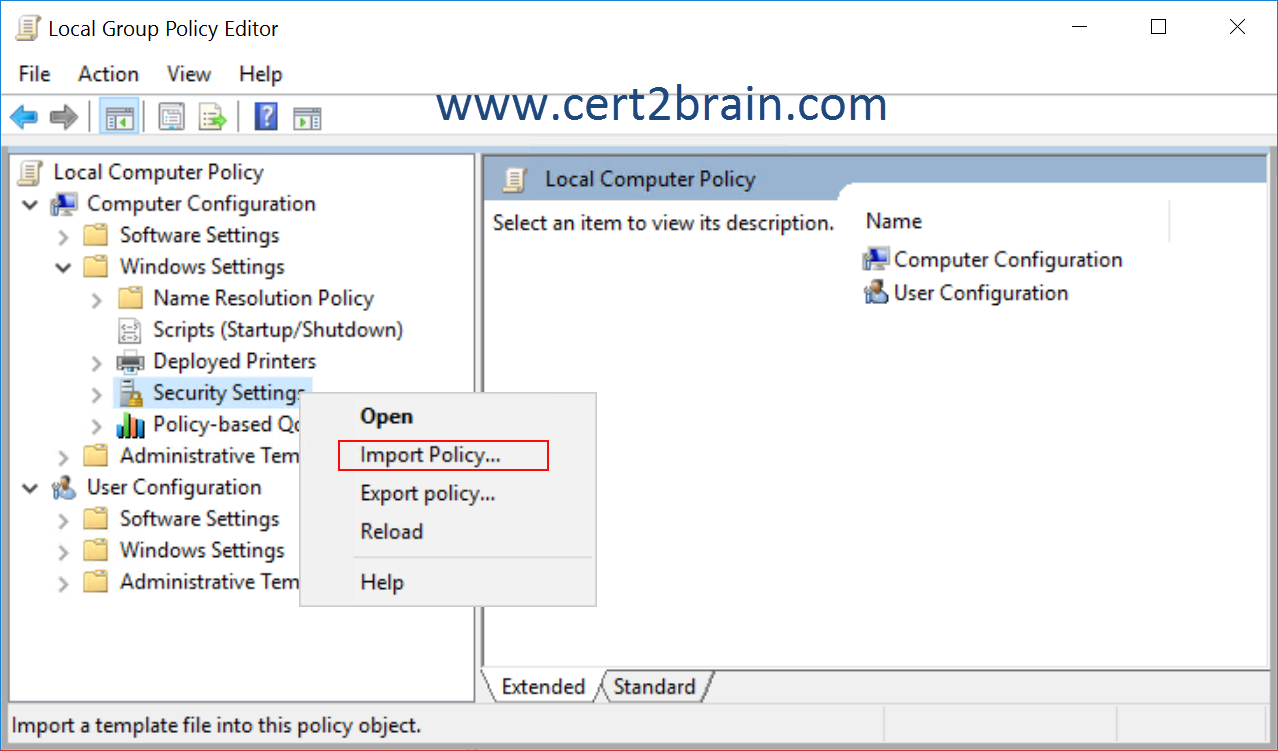
You need to apply a security baseline named Perimeter.inf to the servers in the perimeter network.
What should you use to apply Perimeter.inf?| A | System Configuration | | B | Microsoft Security Compliance manager (SCM) 4.0 | | C | Security Templates | | D | Local Computer Policy |
Correct answer: DExplanation:
Since the servers in the perimeter network are not domain members, we should use the Local Computer Policy to import the security template.
 Question: 239
Question: 239
Measured Skill: Implement workload-specific security (5–10%)
You are an administrator for a company. You have a server named Server1.
You need to configure PowerShell logging to capture dynamic code generation. The solution must minimize the number of events that are logged.
What should you configure?| A | Protected Event Logging | | B | Script Block Logging | | C | Module Logging | | D | System-Wide Transcription |
Correct answer: BExplanation:
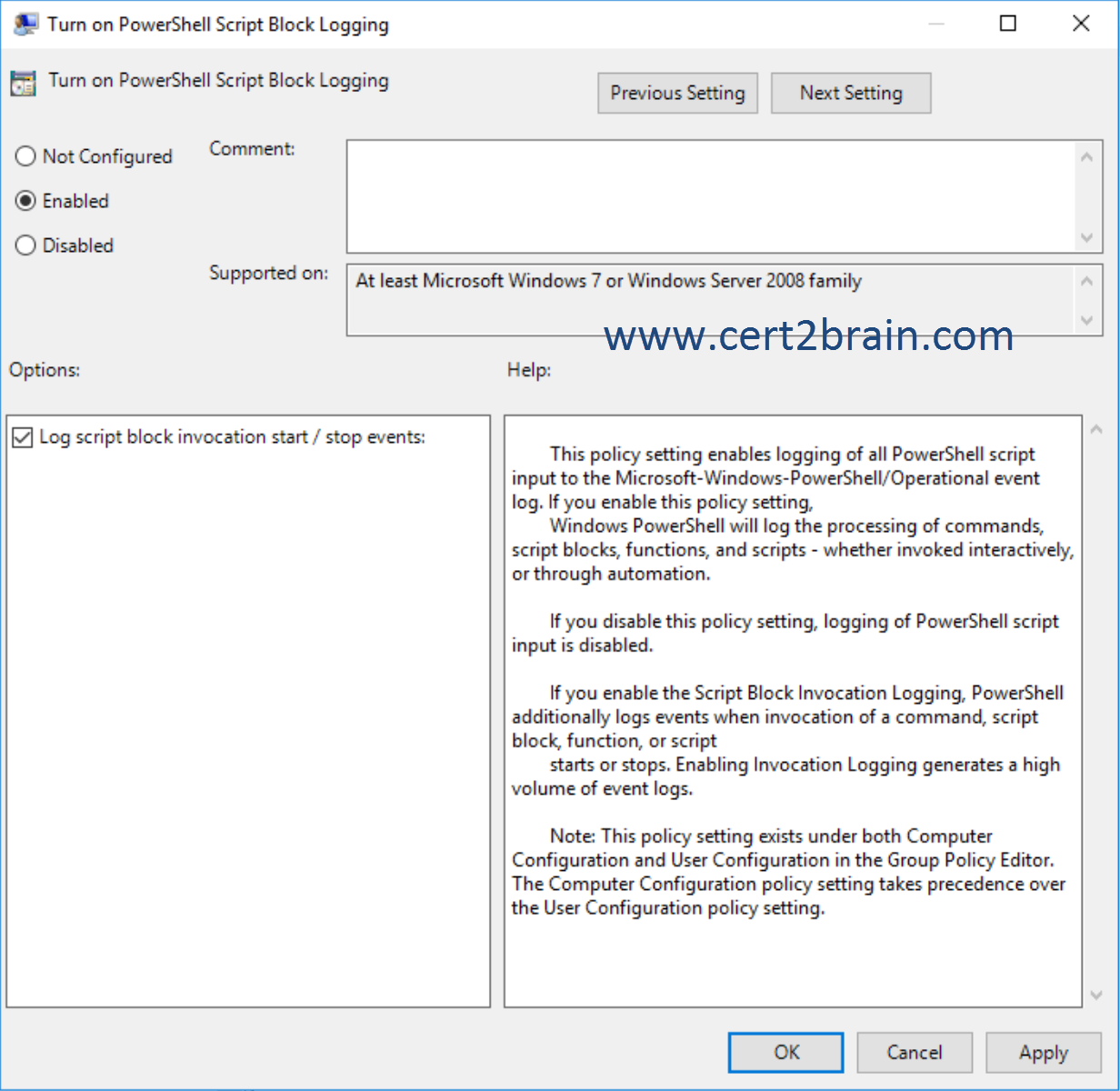
While PowerShell already has the LogPipelineExecutionDetails Group Policy setting to log the invocation of cmdlets, PowerShell's scripting language has several features that you might want to log and audit. The new Detailed Script Tracing feature provides detailed tracking and analysis of PowerShell script activity on a system. After enabling detailed script tracing, PowerShell logs all script blocks to the ETW event log, Microsoft-Windows-PowerShell/Operational. If a script block creates another script block, for example, by calling Invoke-Expression, the invoked script block also logged.
Logging is enabled through the Turn on PowerShell Script Block Logging Group Policy setting in Administrative Templates -> Windows Components -> Windows PowerShell.
Note:
- Protected event logging can prevent scripted passwords from being written to event logs.
- System-wide transcription enables a PowerShell session to be logged in a file.
- Module logging enables PowerShell logging for individual administrator-defined PowerShell modules.
Reference: Script Tracing and Logging
Question: 240
Measured Skill: Implement workload-specific security (5–10%)
Your network contains an Active Directory domain named adatum.com. The domain contains a server named Server1 that runs Windows Server 2016 and a group named Group1. A user named user1 is the only member of Group1.
You plan to implement Just Enough Administration (JEA) on Server1.
You create a role capability file named JEARole that contains the following content.
@{
GUID = '1862f423-6784-471a-a846-7927d6c7dd65'
VisibleCmdlets = 'Restart-Computer', 'Get-NetIPAdress'
}
You create a session configuration that contains the following content.
@{
SchemaVersion = '2.0.0.0'
GUID = '44988465-5c15-4872-93e2-6c892858a2f4'
SessionType = 'RestrictedRemoteServer'
RunAsVirtualAccount = $true
RoleDefinitions = @{
'Adatum\Group1' = @{RoleCapabilities = 'JEARole'}
}
}
You register a JEA endpoint by using the -Name Role1 parameter.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
(NOTE: Each correct selection is worth one point.) | A | Adatum\Administrator can connect to Server1 by running Enter-PSSession Server1 -ConfigurationName Role1: Yes
User1 can connect to Server1 by running Enter-PSSession Server1 -ConfigurationName Role1: Yes
A user who establishes a JEA session to Server1 can run Get-Command on Server1: Yes | | B | Adatum\Administrator can connect to Server1 by running Enter-PSSession Server1 -ConfigurationName Role1: Yes
User1 can connect to Server1 by running Enter-PSSession Server1 -ConfigurationName Role1: Yes
A user who establishes a JEA session to Server1 can run Get-Command on Server1: No | | C | Adatum\Administrator can connect to Server1 by running Enter-PSSession Server1 -ConfigurationName Role1: Yes
User1 can connect to Server1 by running Enter-PSSession Server1 -ConfigurationName Role1: No
A user who establishes a JEA session to Server1 can run Get-Command on Server1: No | | D | Adatum\Administrator can connect to Server1 by running Enter-PSSession Server1 -ConfigurationName Role1: No
User1 can connect to Server1 by running Enter-PSSession Server1 -ConfigurationName Role1: Yes
A user who establishes a JEA session to Server1 can run Get-Command on Server1: No | | E | Adatum\Administrator can connect to Server1 by running Enter-PSSession Server1 -ConfigurationName Role1: No
User1 can connect to Server1 by running Enter-PSSession Server1 -ConfigurationName Role1: Yes
A user who establishes a JEA session to Server1 can run Get-Command on Server1: Yes | | F | Adatum\Administrator can connect to Server1 by running Enter-PSSession Server1 -ConfigurationName Role1: No
User1 can connect to Server1 by running Enter-PSSession Server1 -ConfigurationName Role1: No
A user who establishes a JEA session to Server1 can run Get-Command on Server1: No |
Correct answer: EExplanation:
The role capability file allows the execution of the Restart-Computer and the Get-NetIPAddress cmdlets including all parameters.
The Role definitions section in the session configuration file maps the JEARole to the Group1 group. All users and groups included in the RoleDefinitions field are automatically granted access to JEA endpoints.
The -SessionType RestrictedRemoteServer field indicates that the session configuration is used by JEA for secure management. Sessions of this type operate in NoLanguage mode and only have access to the following default commands (and aliases):
- Clear-Host (cls, clear)
- Exit-PSSession (exsn, exit)
- Get-Command (gcm)
- Get-FormatData
- Get-Help
- Measure-Object (measure)
- Out-Default
- Select-Object (select)
No PowerShell providers are available, nor are any external programs (executables or scripts).
References:
JEA Role Capabilities
JEA Session Configurations
Question: 241
Measured Skill: Secure a virtualization infrastructure (5–10%)
You have several virtual machines that run in a hosted data center on Hyper-V hosts.
The hosting provider recently updated the service offering in its Hyper-V environment to include a new Host Guardian Service (HGS).
You plan to use the Shielding Data File Wizard to create a data file that will include password information and an RDP file. The file will be used to create new shielded virtual machines in the fabric of the hosting provider.
What do you require from the hosting provider to complete the wizard?| A | An XML file that contains the names of all the Hyper-V hosts in the fabric. | | B | An XML file that contains virtual machine configuration data from the Hyper-V hosts. | | C | A CER file that contains a certificate from the provider. | | D | An XML file that contains guardian metadata. |
Correct answer: DExplanation:
A shielding data file (also called a provisioning data file or PDK file) is an encrypted file that a tenant or VM owner creates to protect important VM configuration information, such as the administrator password, RDP and other identity-related certificates, domain-join credentials, and so on.
You can run the Shielding Data File wizard or use PowerShell to create a shielding data (PDK) file. Here, you'll add the RDP certificate, unattend file, volume signature catalogs, owner guardian and the downloaded guardian metadata.
Reference: Create a shielding data file and add guardians using the Shielding Data File wizard
|
|
|
Tags: exam, examcollection, exam simulation, exam questions, questions & answers, training course, study guide, vce, braindumps, practice test
|
|
|
|
|
|
|
|
|