Archive - AZ-303: Microsoft Azure Architect Technologies
Sample Questions
Question: 285
Measured Skill: Implement solutions for apps (10-15%)
Note: This questions is based on a case study. The case study is not shown in this demo.
You migrate WebApp1 to Azure.
You need to configure the AKS cluster to enable WebApp1 to access KV1. The solution must meet the authentication and authorization requirements.
What should you do?| A | Implement the Secrets Store CSI Driver. |
| B | Implement pod security policies. |
| C | Configure a pod-managed identity. |
| D | Configure Azure role-based access control (Azure RBAC) for Kubernetes Authorization. |
Correct answer: CExplanation:
The Authentication and Authorization Requirements section contains the following:
WebApp1 running on the AKS cluster must be able to retrieve secrets from KV1.
Managed identities provide an identity for applications to use when connecting to resources that support Azure Active Directory (Azure AD) authentication. Applications may use the managed identity to obtain Azure AD tokens.
Here are some of the benefits of using managed identities:
- You don't need to manage credentials. Credentials aren’t even accessible to you.
- You can use managed identities to authenticate to any resource that supports Azure AD authentication, including your own applications.
- Managed identities can be used without any additional cost.
Azure Active Directory (Azure AD) pod-managed identities use Kubernetes primitives to associate managed identities for Azure resources and identities in Azure AD with pods. Administrators create identities and bindings as Kubernetes primitives that allow pods to access Azure resources that rely on Azure AD as an identity provider.
References:
What are managed identities for Azure resources?
Use Azure Active Directory pod-managed identities in Azure Kubernetes Service (Preview)
Question: 286
Measured Skill: Implement and monitor an Azure infrastructure (50-55%)
Note: This questions is based on a case study. The case study is not shown in this demo.
You need to deploy resources to RG1 by using the existing ARM templates. The solution must meet the deployment requirements.
What should you modify in the templates, and which cmdlet should you run to deploy the resources?
(Use the drop-down menus to complete each statement based on the information presented in the graphic. Note: Each correct selection is worth one point.)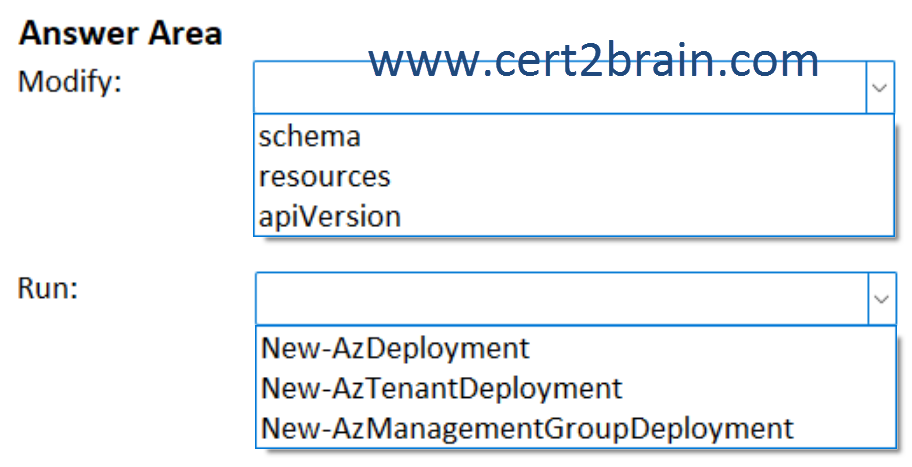
| A | Modify: schema
Run: New-AzDeployment |
| B | Modify: schema
Run: New-AzTenantDeployment |
| C | Modify: resources
Run: New-AzManagementGroupDeployment |
| D | Modify: resources
Run: New-AzDeployment |
| E | Modify: apiVersion
Run: New-AzTenantDeployment |
| F | Modify: apiVersion
Run: New-AzManagementGroupDeployment |
Correct answer: DExplanation:
The Deployment Requirements section contains the following:
The existing ARM templates must be used for deployments to Sub1.
In the ARM template's resources section, you define the resources that are deployed or updated. The resources will change, the schema and the API version will remain the same for all deployments.
The New-AzDeployment cmdlet adds a deployment at the current subscription scope. This includes the resources that the deployment requires.
References:
Understand the structure and syntax of ARM templates
New-AzDeployment
Question: 287
Measured Skill: Implement solutions for apps (10-15%)
You have an Azure subscription that contains the web apps shown in the following table.
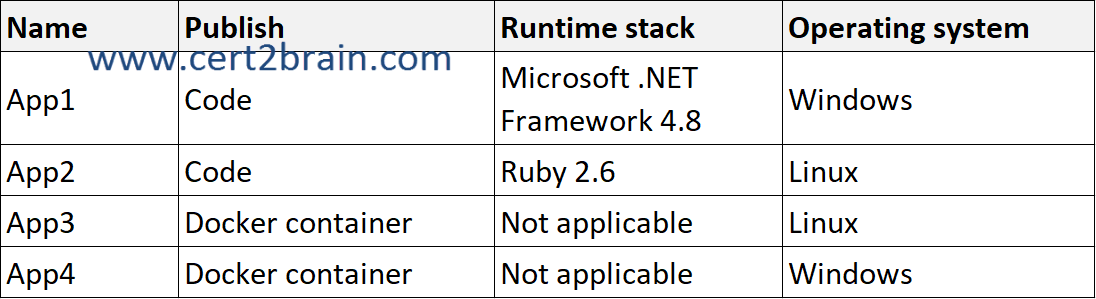
App Service plans use the premium service tier.
Which web apps support WebJobs, and which web apps support deployment slots?
(To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.)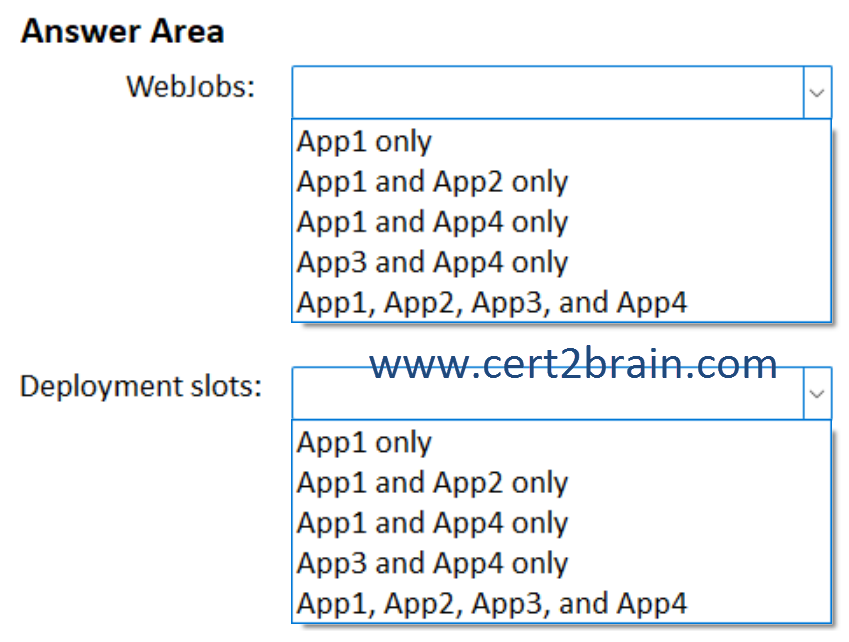
| A | WebJobs: App1 only
Deployment slots: App1, App2, App3, and App4 |
| B | WebJobs: App1 and App2 only
Deployment slots: App1 and App2 only |
| C | WebJobs: App1 and App2 only
Deployment slots: App3 and App4 only |
| D | WebJobs: App1 and App4 only
Deployment slots: App1 and App4 only |
| E | WebJobs: App3 and App4 only
Deployment slots: App1 only |
| F | WebJobs: App1, App2, App3, and App4
Deployment slots: App1, App2, App3, and App4 |
Correct answer: AExplanation:
WebJobs is a feature of Azure App Service that enables you to run a program or script in the same instance as a web app, API app, or mobile app. There is no additional cost to use WebJobs. You can use the Azure WebJobs SDK with WebJobs to simplify many programming tasks. WebJobs is not yet supported for App Service on Linux. Web apps for Containers do not support WebJobs, regardless of the operating system used.
When you deploy your web app, web app on Linux, mobile back end, or API app to Azure App Service, you can use a separate deployment slot instead of the default production slot when you're running in the Standard, Premium, or Isolated App Service plan tier. Deployment slots are live apps with their own host names. App content and configurations elements can be swapped between two deployment slots, including the production slot.
All four apps support deployment slots. But auto swap isn't supported in web apps on Linux and Web App for Containers.
References:
Run background tasks with WebJobs in Azure App Service
Set up staging environments in Azure App Service
Question: 288
Measured Skill: Implement and manage data platforms (10-15%)
You plan to configure an Azure Cosmos DB account as shown in the following table.
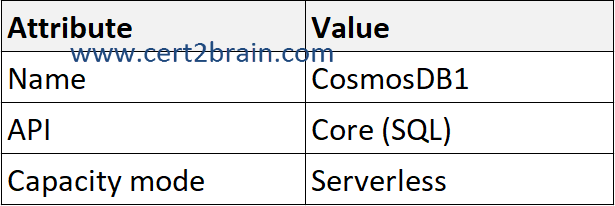
You need to ensure the highest level of resiliency for CosmosDB1.
What should you use?| A | Availability zones |
| B | Multiple write regions |
| C | Geo-redundant storage (GRS) |
| D | An availability set |
Correct answer: CExplanation:
If your solution requires continuous availability during region outages, Cosmos DB can be configured to replicate your data across multiple regions and to transparently fail over to available regions when required.
Single-region accounts may lose availability following a regional outage. To ensure high availability at all times it's recommended to set up your Azure Cosmos DB account with a single write region and at least a second (read) region and enable Service-Managed failover.
Service-managed failover allows Cosmos DB to fail over the write region of multi-region account, in order to preserve availability at the cost of data loss as per durability section. Regional failovers are detected and handled in the Azure Cosmos DB client. They don't require any changes from the application.
Important: It is strongly recommended that you configure the Azure Cosmos accounts used for production workloads to enable automatic failover. This enables Cosmos DB to failover the account databases to available regions automatically. In the absence of this configuration, the account will experience loss of write availability for all the duration of the write region outage, as manual failover will not succeed due to lack of region connectivity.
The best configuration to achieve high availability during a region outage is single write region with service-managed failover.
Reference: Achieve high availability with Cosmos DB
Question: 289
Measured Skill: Implement solutions for apps (10-15%)
You have an Azure Kubernetes Service (AKS) cluster named cluster1.
You plan to create a Helm chart that will deploy a custom containerized application named App1. App1 has a dependency on another chart.
You need to recommend a solution that meets the following requirements:
- Creates the Helm chart directory structure.
- Updates the contents of the directory structure to include the chart dependency.
Which three actions should you recommend be performed in sequence?
(To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)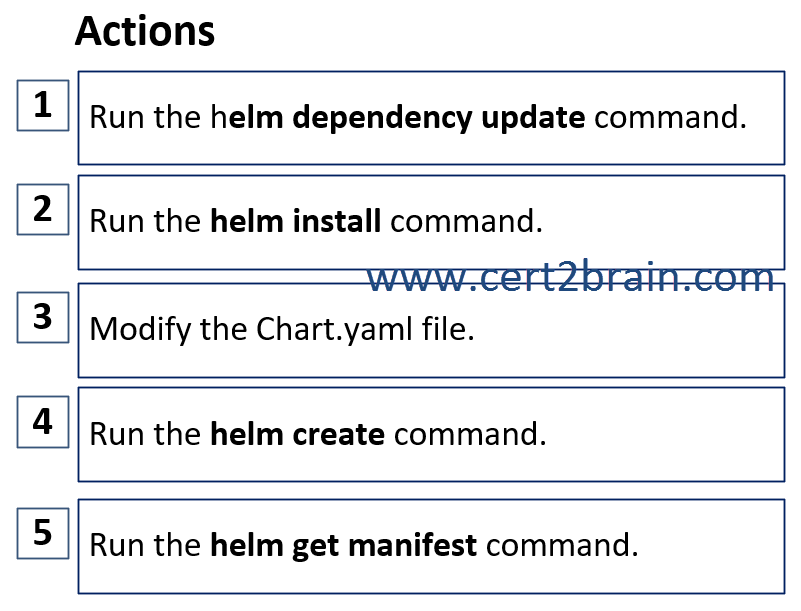
| A | Sequence: 2, 5, 1 |
| B | Sequence: 4, 3, 1 |
| C | Sequence: 5, 3, 2 |
| D | Sequence: 2, 3, 1 |
Correct answer: BExplanation:
Helm is an open-source packaging tool that helps you install and manage the lifecycle of Kubernetes applications. Similar to Linux package managers like APT and Yum, Helm manages Kubernetes charts, which are packages of pre-configured Kubernetes resources.
We need to generate the Helm chart using the helm create command and to update the helm chart dependencies using the helm dependency update command.
Reference: Quickstart: Develop on Azure Kubernetes Service (AKS) with Helm