Microsoft - AZ-900: Microsoft Azure Fundamentals
Sample Questions
Question: 559
Measured Skill: Describe cloud concepts (20-25%)
You need to identify a customer’s level of shared responsibility based on the cloud service model.
In which order should you list each model from most customer responsibility to least customer responsibility?
(To answer, move all models from the list of models to the answer area and
arrange them in the correct order.) 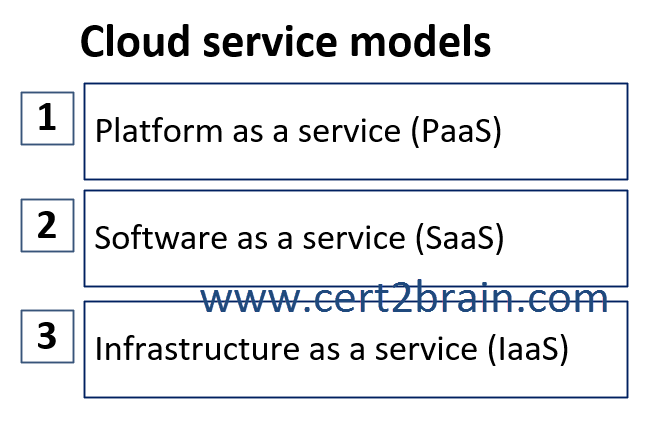
| A | Sequence: 2, 1, 3 |
| B | Sequence: 3, 1, 2 |
| C | Sequence: 1, 3, 2 |
| D | Sequence: 1, 2, 3 |
Correct answer: BExplanation:
As you consider and evaluate public cloud services, it's critical to understand the shared responsibility model and which security tasks the cloud provider handles and which tasks you handle. The workload responsibilities vary depending on whether the workload is hosted on Software as a Service (SaaS), Platform as a Service (PaaS), Infrastructure as a Service (IaaS), or in an on-premises datacenter.
Division of responsibility
In an on-premises datacenter, you own the whole stack. As you move to the cloud some responsibilities transfer to Microsoft. The following diagram illustrates the areas of responsibility between you and Microsoft, according to the type of deployment of your stack.
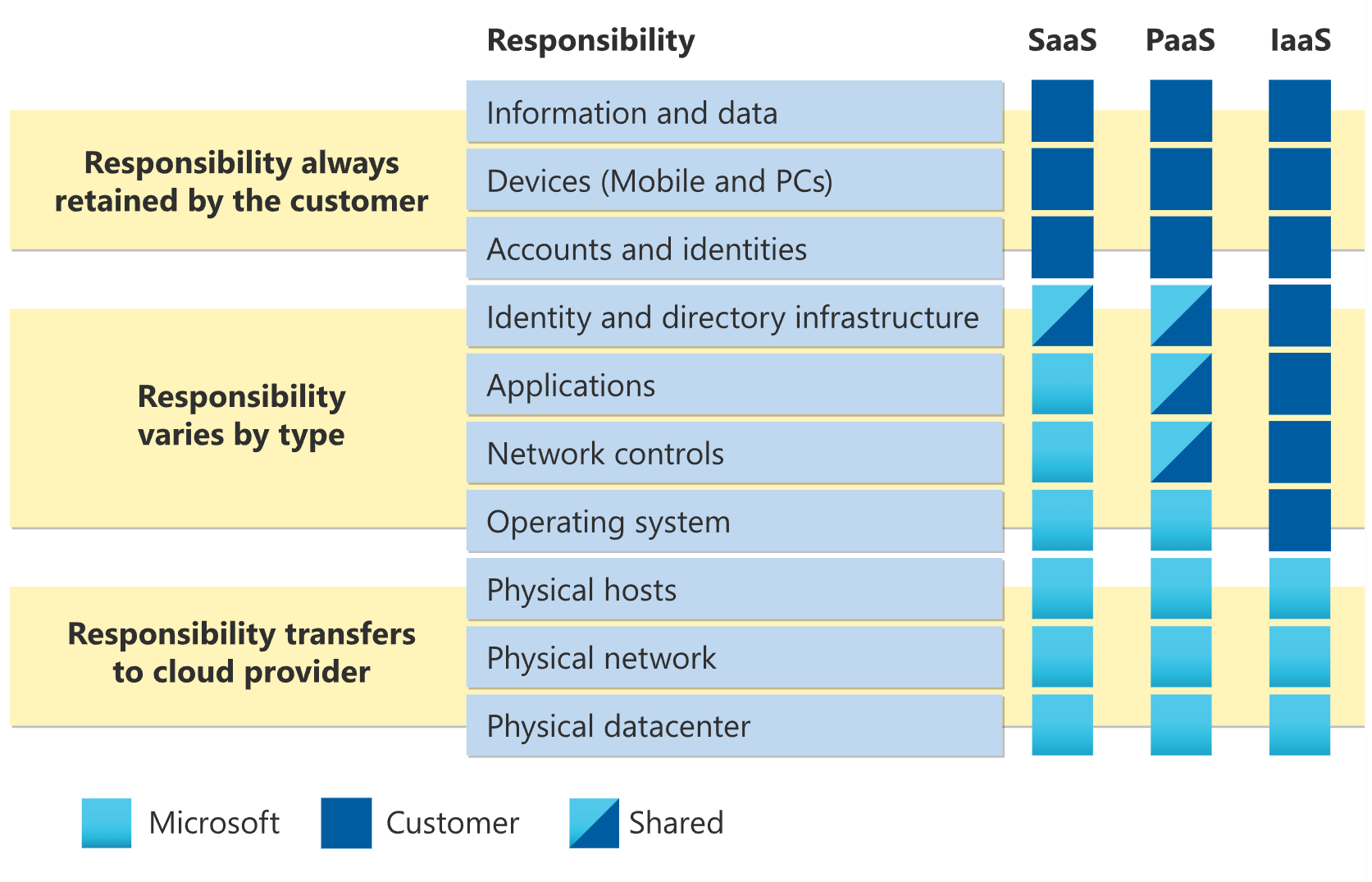
For all cloud deployment types, you own your data and identities. You're responsible for protecting the security of your data and identities, on-premises resources, and the cloud components you control. Cloud components you control vary by service type.
Regardless of the type of deployment, you always retain the following responsibilities:
- Data
- Endpoints
- Account
- Access management
Reference: Shared responsibility in the cloud
Question: 560
Measured Skill: Describe cloud concepts (20-25%)
In the software as a service (SaaS) cloud service, which responsibility is shared between Microsoft and the customer?| A | Identity and directory infrastructure management |
| B | Application management |
| C | Information and data management |
| D | Operating system updates |
Correct answer: AExplanation:
As you consider and evaluate public cloud services, it's critical to understand the shared responsibility model and which security tasks the cloud provider handles and which tasks you handle. The workload responsibilities vary depending on whether the workload is hosted on Software as a Service (SaaS), Platform as a Service (PaaS), Infrastructure as a Service (IaaS), or in an on-premises datacenter.
Division of responsibility
In an on-premises datacenter, you own the whole stack. As you move to the cloud some responsibilities transfer to Microsoft. The following diagram illustrates the areas of responsibility between you and Microsoft, according to the type of deployment of your stack.

For all cloud deployment types, you own your data and identities. You're responsible for protecting the security of your data and identities, on-premises resources, and the cloud components you control. Cloud components you control vary by service type.
Regardless of the type of deployment, you always retain the following responsibilities:
- Data
- Endpoints
- Account
- Access management
Reference: Shared responsibility in the cloud
Question: 561
Measured Skill: Describe Azure architecture and services (35–40%)
You have an Azure subscription.
You plan to create a virtual machine.
Where will the virtual machine be placed in Azure?| A | In a storage account |
| B | In a resource group |
| C | In an administrative unit |
| D | In an application group |
Correct answer: BExplanation:
An Azure resource group is a container that logically organizes related resources for an Azure solution. These resources, such as virtual machines, storage accounts, and virtual networks, can be managed collectively as a unit. Resource groups simplify deployment, management, and deletion of resources by grouping those that share a common lifecycle.
Reference: Use the Azure portal and Azure Resource Manager to manage resource groups
Question: 562
Measured Skill: Describe Azure architecture and services (35–40%)
Match the authentication method to the appropriate level of security.
(To answer, drag the appropriate authentication method from the column on the left to its level of security on the right. NOTE: Each correct match is worth one point.)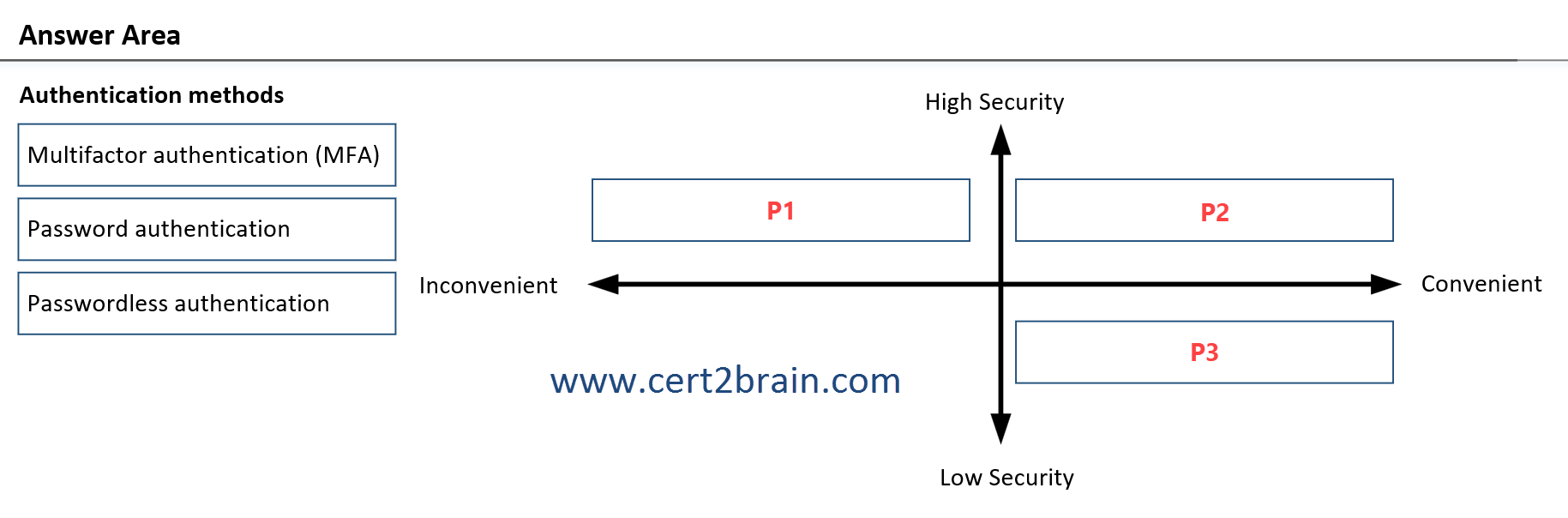
| A | P1: Multifactor authentication (MFA)
P2: Passwordless authentication
P3: Password authentication |
| B | P1: Password authentication
P2: Multifactor authentication (MFA)
P3: Passwordless authentication |
| C | P1: Passwordless authentication
P2: Password authentication
P3: Multifactor authentication (MFA) |
| D | P1: Multifactor authentication (MFA)
P2: Password authentication
P3: Passwordless authentication |
Correct answer: AExplanation:
Microsoft recommends passwordless authentication methods such as Windows Hello, Passkeys (FIDO2), and the Microsoft Authenticator app because they provide the most secure sign-in experience. Although a user can sign-in using other common methods such as a username and password, passwords should be replaced with more secure authentication methods.
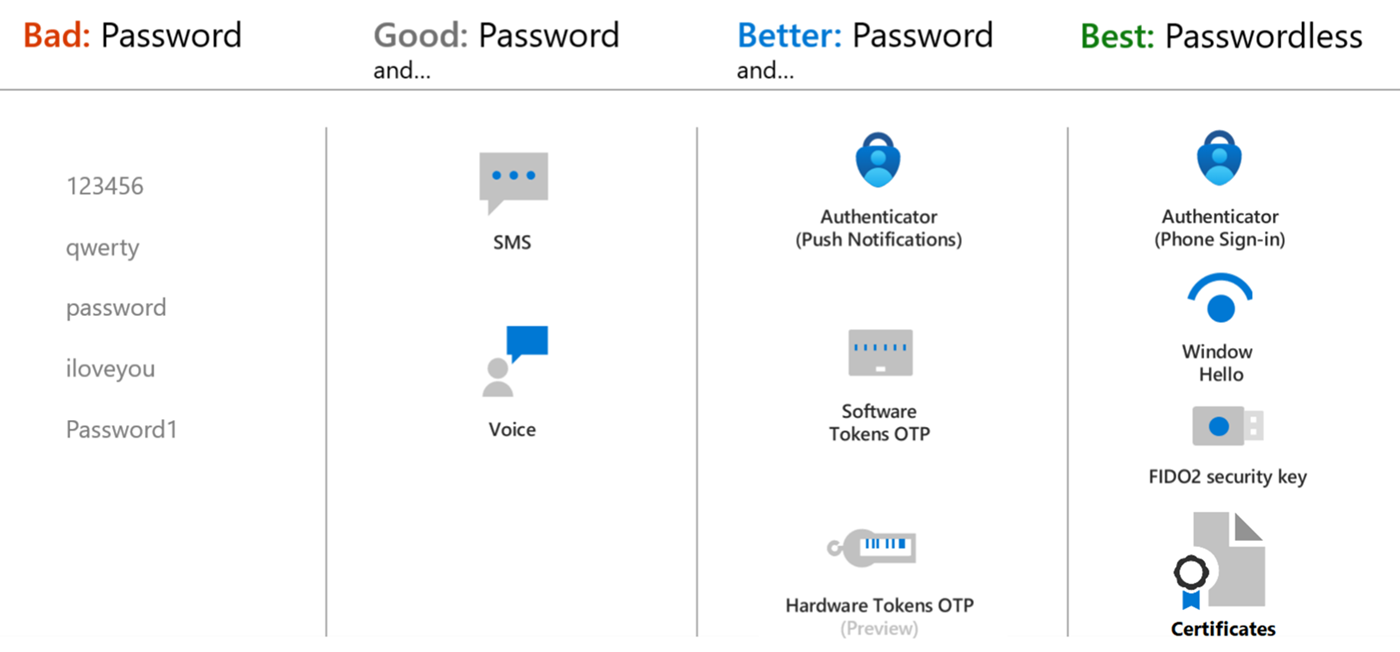
Microsoft Entra multifactor authentication adds another layer of security over only using a password when a user signs in. The user can be prompted for other forms of authentication, such as to respond to a push notification, enter a code from a software or hardware token, or respond to a text message or phone call.
Reference: What authentication and verification methods are available in Microsoft Entra ID?
Question: 563
Measured Skill: Describe cloud concepts (20-25%)
Select the answer that correctly completes the sentence.
| A | A cloud service provider's service-level agreement (SLA) expresses availability as a percentage of uptime over a given year. |
| B | A cloud service provider's service-level agreement (SLA) expresses elasticity as a percentage of uptime over a given year. |
| C | A cloud service provider's service-level agreement (SLA) expresses reliability as a percentage of uptime over a given year. |
| D | A cloud service provider's service-level agreement (SLA) expresses scalability as a percentage of uptime over a given year. |
Correct answer: AExplanation:
The Service Level Agreements (SLA) describe Microsoft’s commitments for uptime and connectivity for Microsoft Online Services. Service availability is the amount of time that a provider's service is available for use. This is sometimes measured in a time slot. For example, your SLA might specify that a provider's service will be available for a minimum of 99.5% capacity for a specific 12-hour window each day.
Reference: Service Level Agreements (SLA) for Online Services