Microsoft - MD-102: Endpoint Administrator
Sample Questions
Question: 431
Measured Skill: Manage and maintain devices (30–35%)
You have a Microsoft 365 subscription and use the Microsoft Intune Suite.
You have the devices shown in the following table.
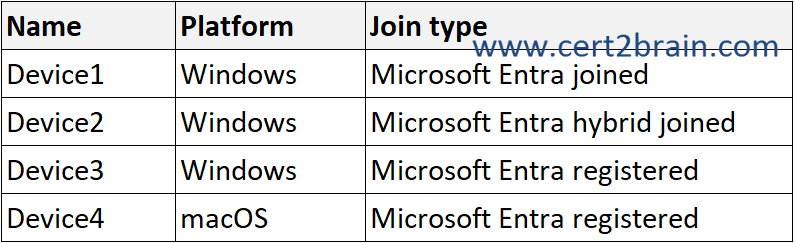
All the devices are enrolled in Intune.
Which devices can you query by using Device query?| A | Device1 only |
| B | Device1 and Device2 only |
| C | Device1, Device2, and Device3 only |
| D | Device1, Device2, and Device4 only |
| E | Device1, Device2, Device3, and Device4 |
Correct answer: BExplanation:
Device query allows you to quickly gain on-demand information about the state of your devices. When you enter a query on a selected device, Device query runs a query in real time. The data returned can then be used to respond to security threats, troubleshoot the device, or make business decisions.
Prerequisites
To use Device query in your tenant, you must have a license that includes Microsoft Intune Advanced Analytics. Advanced Analytics features are available with:
- The Intune Advanced Analytics Add-on
- Microsoft Intune Suite
To use Device query on a device, the device must be enrolled in Endpoint Analytics. Learn how to enroll a device in Endpoint Analytics.
You cannot opt out of cloud notifications (WNS)
For a user to use Device query, you must assign the Managed Devices - Query permission to them.
To use Device query, devices must be Intune managed and corporate owned.
To run remote actions, at a minimum, sign into the Intune admin center with an account that has the Help Desk Operator role. For more information on the different roles, go to Role-based access control (RBAC) with Microsoft Intune.
To receive the remote action, the device must be connected to the internet and powered on.
Supported platforms
Device query is currently only supported on devices running Windows 10 and later.
Reference: Device query
Question: 432
Measured Skill: Manage and maintain devices (30–35%)
You have a Microsoft 365 subscription that contains 500 Android devices. The devices are managed by using Microsoft Intune.
You need to ensure that you can manage software updates for the devices by using Android Firmware Over-the-Air (FOTA) .
What should you do first?| A | Create a compliance policy. |
| B | Add a compliance partner. |
| C | Configure a connector. |
| D | Add derived credentials. |
Correct answer: CExplanation:
You can use Microsoft Intune to manage software updates on the following Android Enterprise devices:
- Fully Managed
- Dedicated
- Corporate-Owned Work Profile devices
You have two ways to manage software updates on android:
Use Firmware Over-the-Air (FOTA), which works for some OEMs.
If FOTA isn't available you can use Device restrictions profiles, which work for all OEMs.
Firmware Over-the-Air (FOTA) updates allow remotely updating the firmware of devices using a wireless connection, rather than requiring the devices to be physically connected to a computer or network.
A FOTA update can include software and security patches, feature updates, and other changes to the device's firmware. This method is more efficient, convenient, and more secure than manual updates and can be performed on a scheduled or on-demand basis.
In the context of FOTA, a deployment is an update policy that includes instructions about the firmware update to be deployed to devices and other update-related settings. For example, Schedule type, and charging requirements.
In addition, Microsoft Intune supports FOTA update management for supported devices from the following manufacturers.
To enable communication between Intune and the OEM’s firmware update infrastructure, we need to configure a connector.
References:
Android FOTA Updates
Zebra LifeGuard Over-the-Air Integration with Microsoft Intune
Question: 433
Measured Skill: Manage applications (15–20%)
You have a Microsoft 365 subscription and use Microsoft Intune.
You need to implement Microsoft Tunnel for Mobile Application Management (MAM) for personal Android devices.
You perform the following actions:
- Configure Microsoft Tunnel for managed devices.
- Validate that user devices meet the prerequisites for Tunnel for MAM.
- Create app configuration policies for Microsoft Defender and Microsoft Edge.
What should you configure next?| A | An app protection policy |
| B | A custom profile for Android Enterprise devices |
| C | A Conditional Access policy |
| D | A VPN profile for Android Enterprise devices |
Correct answer: AExplanation:
When you add Microsoft Tunnel for Mobile Application Management (MAM) to your tenant, you can use Microsoft Tunnel VPN Gateway with unenrolled Android devices to support MAM scenarios. With support for MAM, your unenrolled devices can use Tunnel to securely connect to your organization allowing users and apps safe access to your organizational data.
To extend your existing Microsoft Tunnel configuration to support MAM, create and deploy three profiles that configure this support on your unenrolled devices:
App configuration policy for Microsoft Defender. This policy configures Microsoft Defender for Endpoint on a device as the VPN tunnel client app.
App configuration policy for Microsoft Edge. This policy configures Microsoft Edge to support identity-switch, which automatically connects and disconnects the VPN tunnel when switching from a Microsoft "Work or school" account to a Microsoft "personal account" in Microsoft Edge.
App protection policy to automatically start the connection to Microsoft Tunnel when the MAM enabled app on the device accesses corporate resources.
Reference: Microsoft Tunnel for Mobile Application Management for Android
Question: 434
Measured Skill: Protect devices (15–20%)
You have a Microsoft 365 E5 subscription that contains 500 Windows devices enrolled in Microsoft Intune.
You deploy Microsoft Defender for Endpoint.
You need to onboard the devices to Defender for Endpoint. The solution must minimize administrative effort.
What should you do?
(To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.)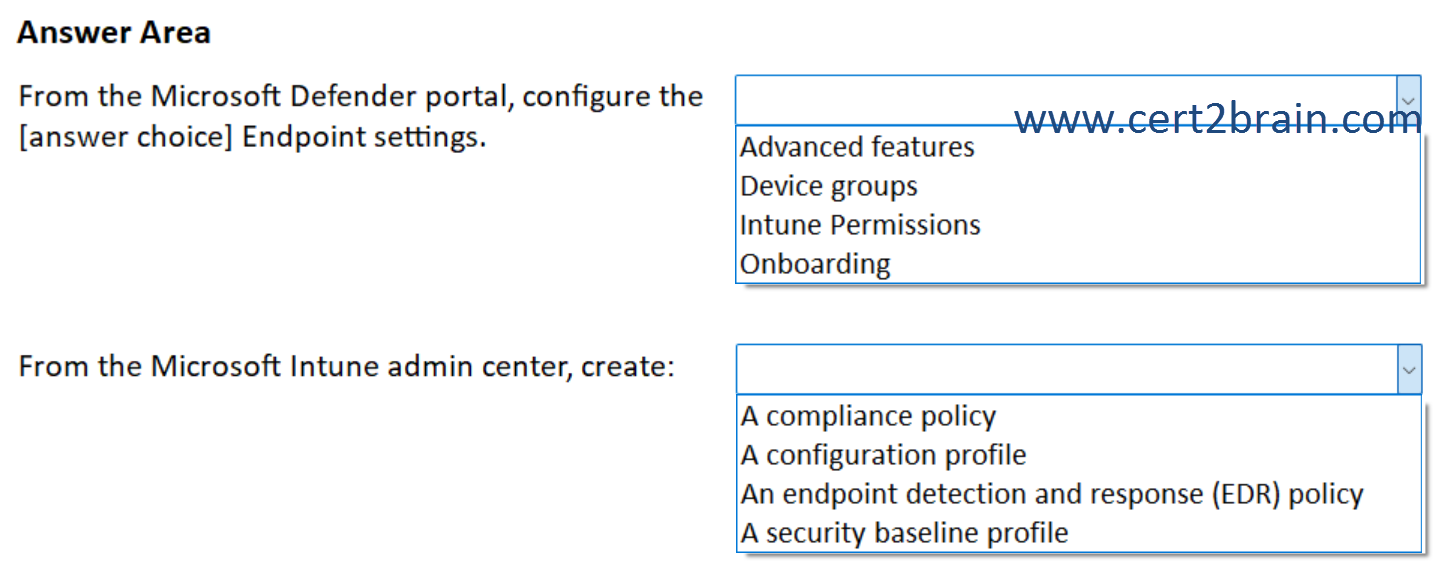
| A | From the Microsoft Defender portal, configure the Advanced features Endpoint settings.
From the Microsoft Intune admin center, create: An endpoint detection and response (EDR) policy |
| B | From the Microsoft Defender portal, configure the Advanced features Endpoint settings.
From the Microsoft Intune admin center, create: A configuration profile |
| C | From the Microsoft Defender portal, configure the Device groups Endpoint settings.
From the Microsoft Intune admin center, create: A compliance policy |
| D | From the Microsoft Defender portal, configure the Intune Permissions Endpoint settings.
From the Microsoft Intune admin center, create: A security baseline profile |
| E | From the Microsoft Defender portal, configure the Onboarding Endpoint settings.
From the Microsoft Intune admin center, create: A configuration profile |
| F | From the Microsoft Defender portal, configure the Onboarding Endpoint settings.
From the Microsoft Intune admin center, create: A security baseline profile |
Correct answer: AExplanation:
Before Intune and Defender for Endpoint can work together, you must set up the service-to-service connection between Intune and Microsoft Defender for Endpoint. This is a one-time action per tenant. Setup requires administrative access to both the Microsoft Defender Security Center and the Microsoft Intune admin center.
On the advanced features pane from the Endpoint settings in the Microsoft Defender portal, we need to locate the entry for Microsoft Intune connection and set the toggle to On.
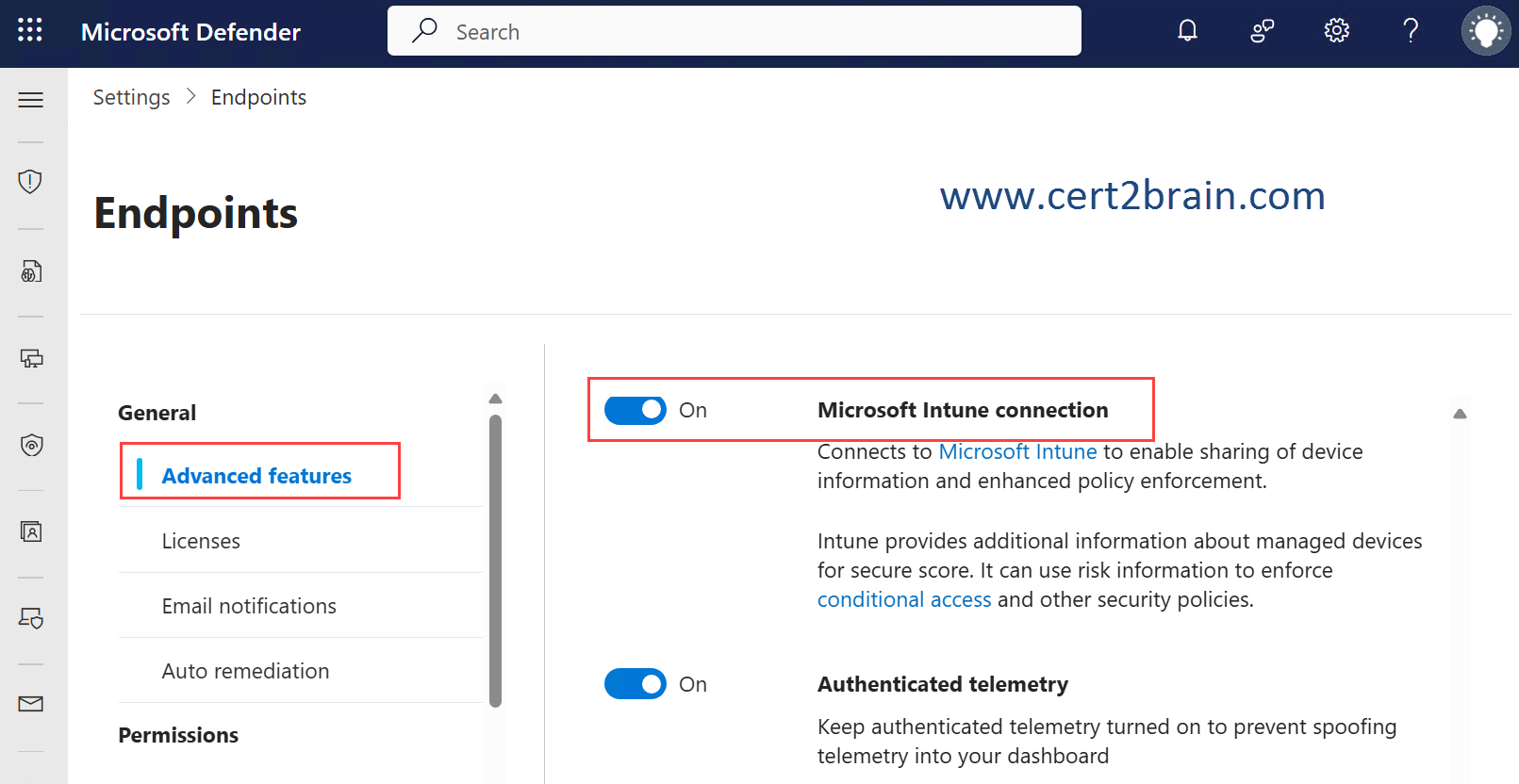
With a connection between Intune and Defender established, Intune automatically receives an onboarding configuration package from Defender that can be used by Intune to onboard Windows devices. This package is used by Intune EDR policy to configure devices to communicate with Microsoft Defender for Endpoint services and to scan files and detect threats.
Onboarding of a device using the configuration package is a one-time action.
To deploy the onboarding package for Windows devices, you can choose to use a preconfigured EDR policy option, which deploys to the All devices group to onboard all applicable Windows devices, or you can manually create the EDR Policy for more granular deployments, which requires you to complete a few additional steps.
References:
Integrate Microsoft Defender for Endpoint with Intune and Onboard Devices
Onboard Windows devices to Defender for Endpoint using Intune
Question: 435
Measured Skill: Manage applications (15–20%)
You have a Microsoft 365 E5 subscription that contains 500 Windows devices and the resources shown in the following table.
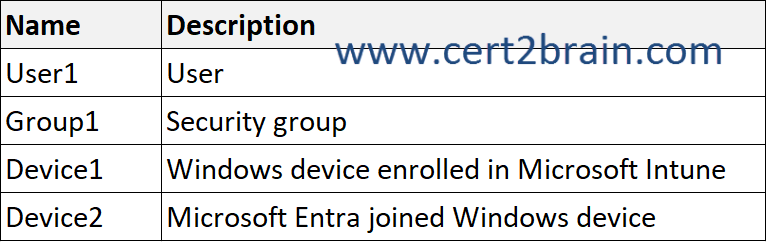
Both devices have Microsoft 365 apps installed.
You need to create and assign a policy for Office Apps that will block macros from running in Office files from the internet.
Which portal should you use, and what can you configure as the scope of the policy?
(To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.)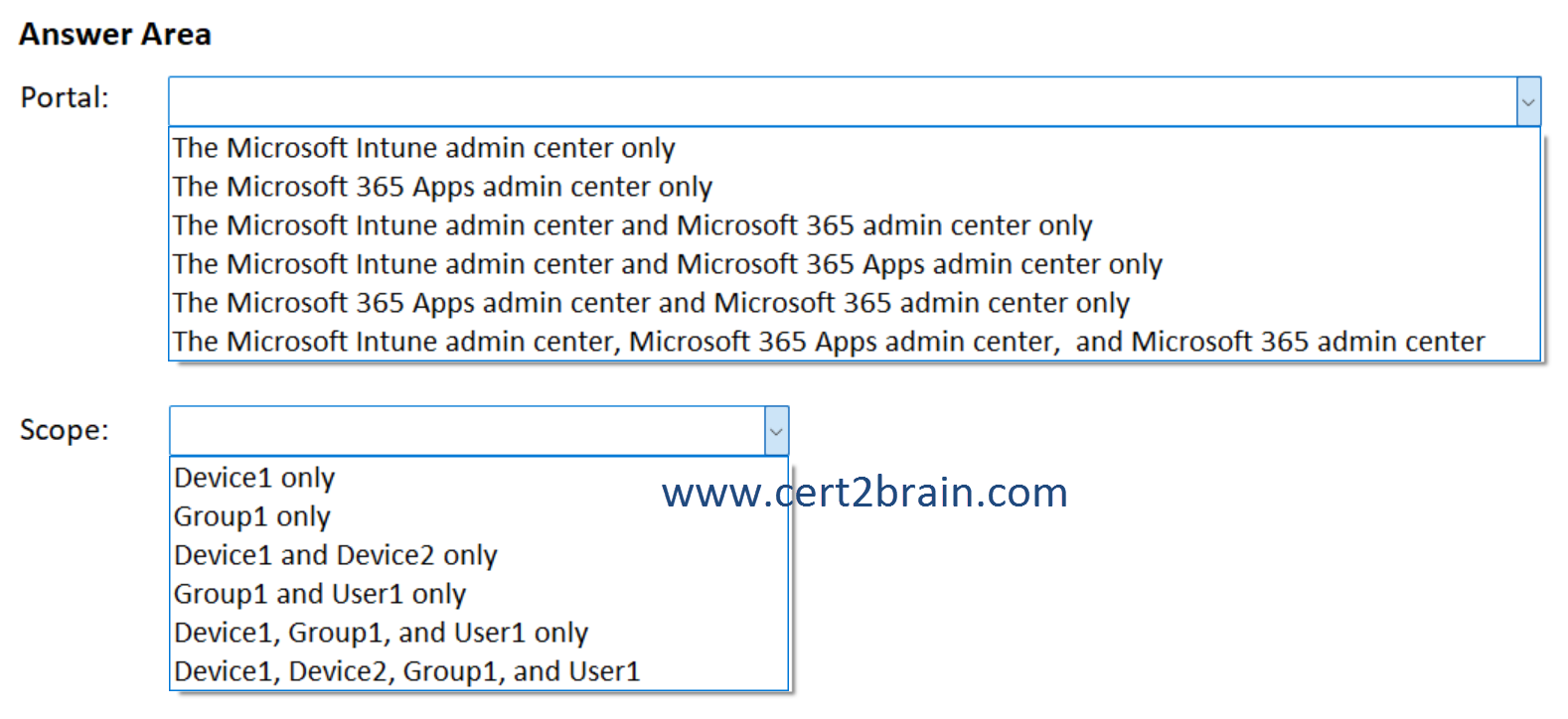
| A | Portal: The Microsoft Intune admin center only
Scope: Device1 and Device2 only |
| B | Portal: The Microsoft 365 Apps admin center only
Scope: Device1, Device2, Group1, and User1 |
| C | Portal: The Microsoft Intune admin center and Microsoft 365 admin center only
Scope: Group1 and User1 only |
| D | Portal: The Microsoft Intune admin center and Microsoft 365 Apps admin center only
Scope: Group1 only |
| E | Portal: The Microsoft 365 Apps admin center and Microsoft 365 admin center only
Scope: Device1 only |
| F | Portal: The Microsoft Intune admin center, Microsoft 365 Apps admin center, and Microsoft 365 admin center
Scope: Device1, Group1, and User1 only |
Correct answer: DExplanation:
We should create a Policy for Microsoft 365 apps either from the Microsoft 365 Apps admin center or from Microsoft Intune ans set the "Block macros from running in Office files from the INternet" setting to "Enabled".
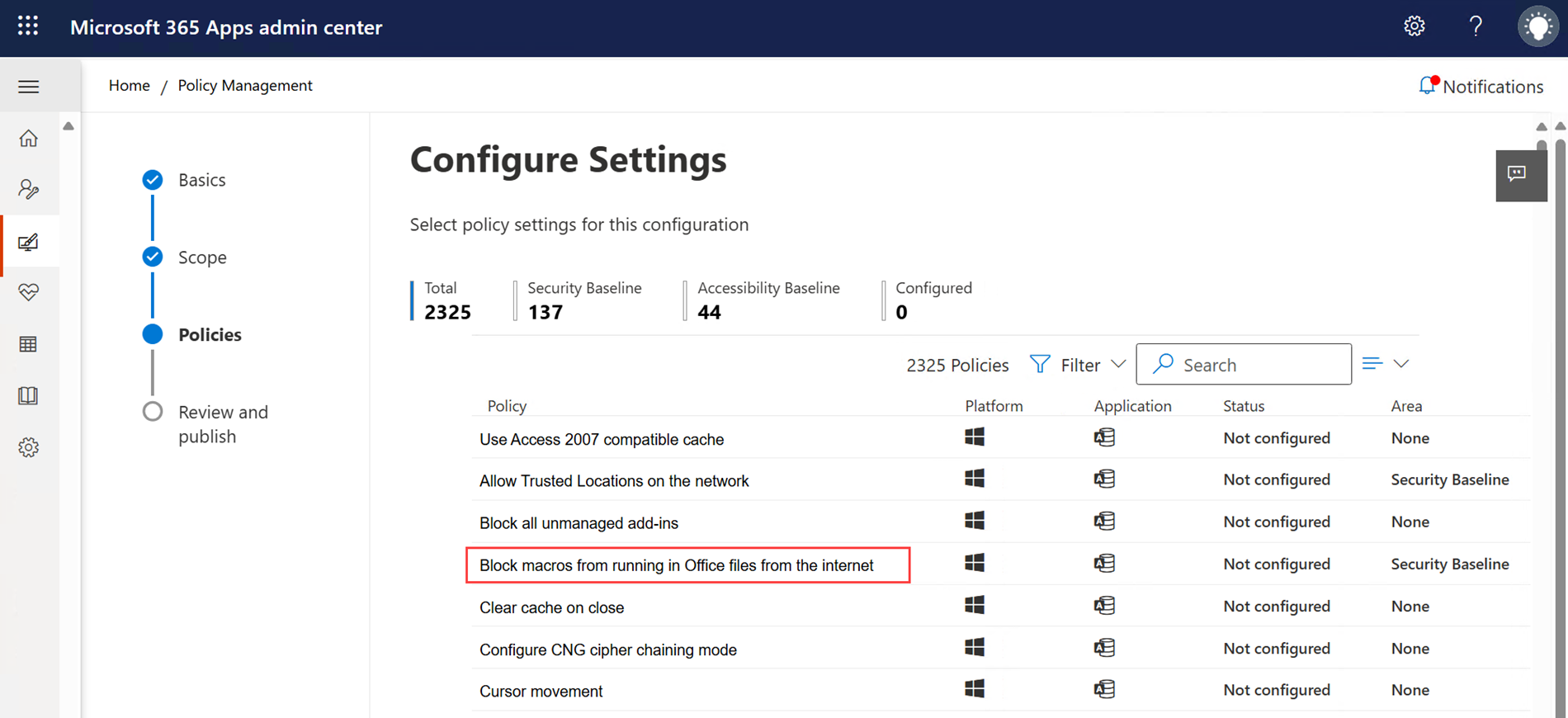
The policy scope can be configured to all users or to users in a specified group.
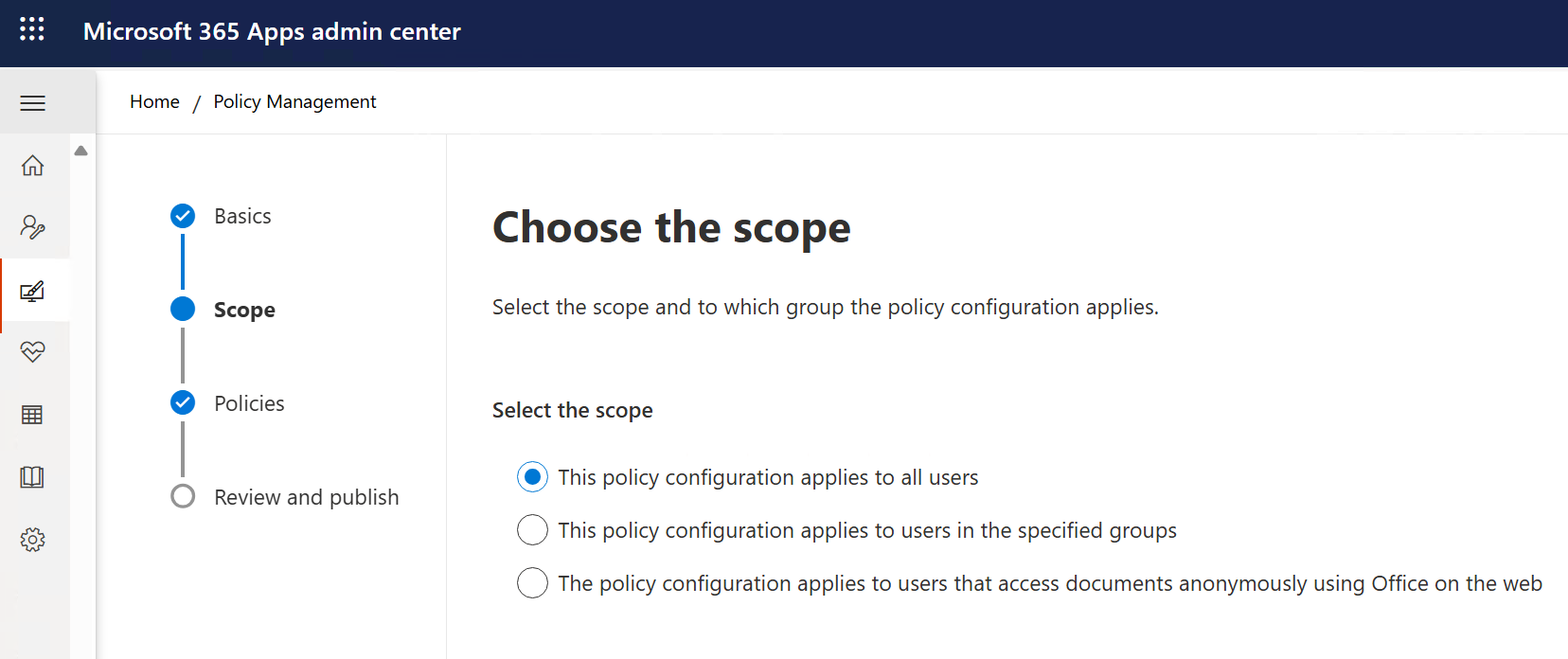
References:
Policies for Microsoft 365 apps
Overview of the Microsoft 365 Apps admin center