Archive - MS-100: Microsoft 365 Identity and Services
Sample Questions
Question: 510
Measured Skill: Manage User Identity and Roles (35-40%)
You have a Microsoft 365 subscription.
You plan to implement Microsoft Purview Privileged Access Management.
Which Microsoft Office 365 workloads support privileged access?| A | Microsoft Teams and SharePoint Online only |
| B | Microsoft Teams, Exchange Online, and SharePoint Online |
| C | Microsoft Exchange Online and SharePoint Online only |
| D | Microsoft Exchange Online only |
| E | Microsoft Teams only |
Correct answer: DExplanation:
Microsoft Purview Privileged Access Management allows granular access control over privileged admin tasks in Office 365. It can help protect your organization from breaches that use existing privileged admin accounts with standing access to sensitive data or access to critical configuration settings. Privileged access management requires users to request just-in-time access to complete elevated and privileged tasks through a highly scoped and time-bounded approval workflow. This configuration gives users just-enough-access to perform the task at hand, without risking exposure of sensitive data or critical configuration settings. Enabling privileged access management allows your organization to operate with zero standing privileges and provide a layer of defense against standing administrative access vulnerabilities.
Microsoft Purview Privileged access management is defined and scoped at the task level, while Azure AD Privileged Identity Management applies protection at the role level with the ability to execute multiple tasks. Azure AD Privileged Identity Management primarily allows managing accesses for AD roles and role groups, while Microsoft Purview Privileged Access Management applies only at the task level.
Microsoft Purview Privileged access management is currently only available for Exchange.
References:
Learn about privileged access management
Get started with privileged access management
Question: 511
Measured Skill: Design and Implement Microsoft 365 Services (25-30%)
You have a Microsoft 365 subscription that uses Microsoft OneDrive.
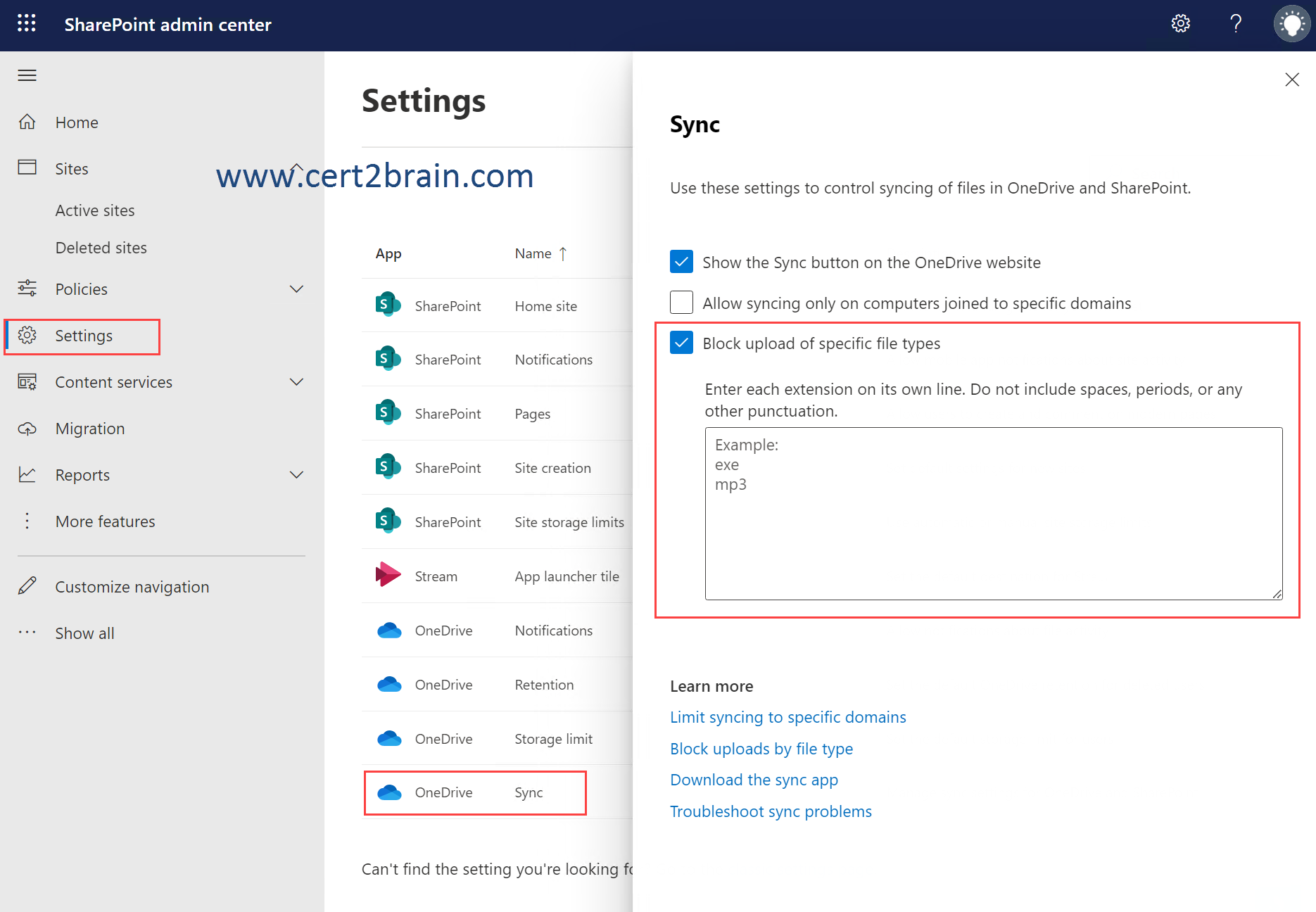
You need to prevent users from syncing .exe and .mp3 files from their local device to OneDrive.
What should you do?| A | From the Microsoft 365 admin center, configure directory synchronization. |
| B | From the SharePoint admin center, configure the Site storage limits settings. |
| C | From the Microsoft 365 Apps admin center, create a policy. |
| D | From the SharePoint admin center, configure the Sync settings. |
Correct answer: DExplanation:
We can block certain file types from being uploaded through the OneDrive sync settings in the SharePoint admin center.
Question: 512
Measured Skill: Plan Office 365 Workloads and Applications (10-15%)
You have a Microsoft 365 subscription that contains an enterprise application named App1.
App1 requires user consent to access user profile and email address information.
You need to ensure that when a user accesses App1, users are granted consent automatically without being prompted. The solution must NOT affect any other apps in the subscription.
What should you do?| A | From the Azure Active Directory admin center, configure permissions for App1. |
| B | From the Azure Active Directory admin center, configure the User consent settings. |
| C | From the Microsoft 365 admin center, disable user consent to apps. |
| D | From the Microsoft 365 admin center, enable privileged access. |
Correct answer: AExplanation:
Many applications that integrate with Azure Active Directory require permissions to various resources in order to run. When these resources are also integrated with Azure Active Directory, the permission to access them is requested using the Azure AD consent framework. These requests result in a consent prompt being shown the first time an application is used, which is often a one-time operation.
To prevent these consent prompts, we should grant App1 the User.Read permission as an admin. The User.Read permission allows users to sign-in to the app, and allows the app to read the profile of signed-in users. It also allows the app to read basic company information of signed-in users.
Reference: Unexpected consent prompt when signing in to an application
Question: 513
Measured Skill: Manage User Identity and Roles (35-40%)
You have an Azure AD tenant named contoso.com that contains an enterprise app named App1 and two users named User1 and User2.
You need to ensure that each user can perform the following action:
- User1: Create entitlement management access packages to provide external users with access to App1.
- User2: Create an access review for App1.
The solution must use the principle of least privilege.
Which role should you assign to each user?
(To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.)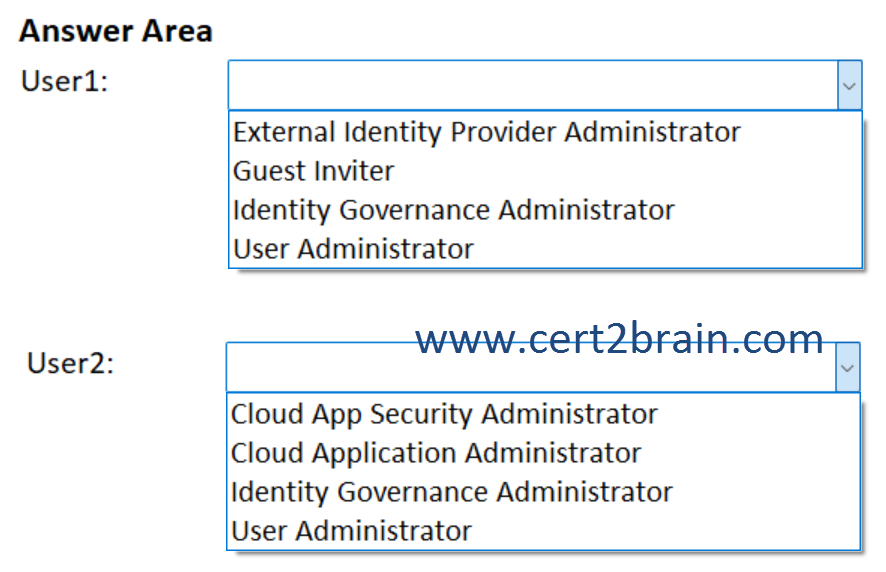
| A | User1: External Identity Provider Administrator
User2: Identity Governance Administrator |
| B | User1: Guest Inviter
User2: External Identity Provider Administrator |
| C | User1: Identity Governance Administrator
User2: User Administrator |
| D | User1: Identity Governance Administrator
User2: Guest Inviter |
| E | User1: User Administrator
User2: User Administrator |
| F | User1: User Administrator
User2: Identity Governance Administrator |
Correct answer: CExplanation:
Identity Governance Administrators can manage Azure AD identity governance configuration, including access packages, access reviews, catalogs and policies, ensuring access is approved and reviewed and guest users who no longer need access are removed.
User Administrator is the leats privileged role to create, update, or delete an access review of a group or of an app.
References:
Identity Governance Administrator
Groups
Question: 514
Measured Skill: Manage Access and Authentication (20-25%)
You have a Microsoft 365 E5 subscription.
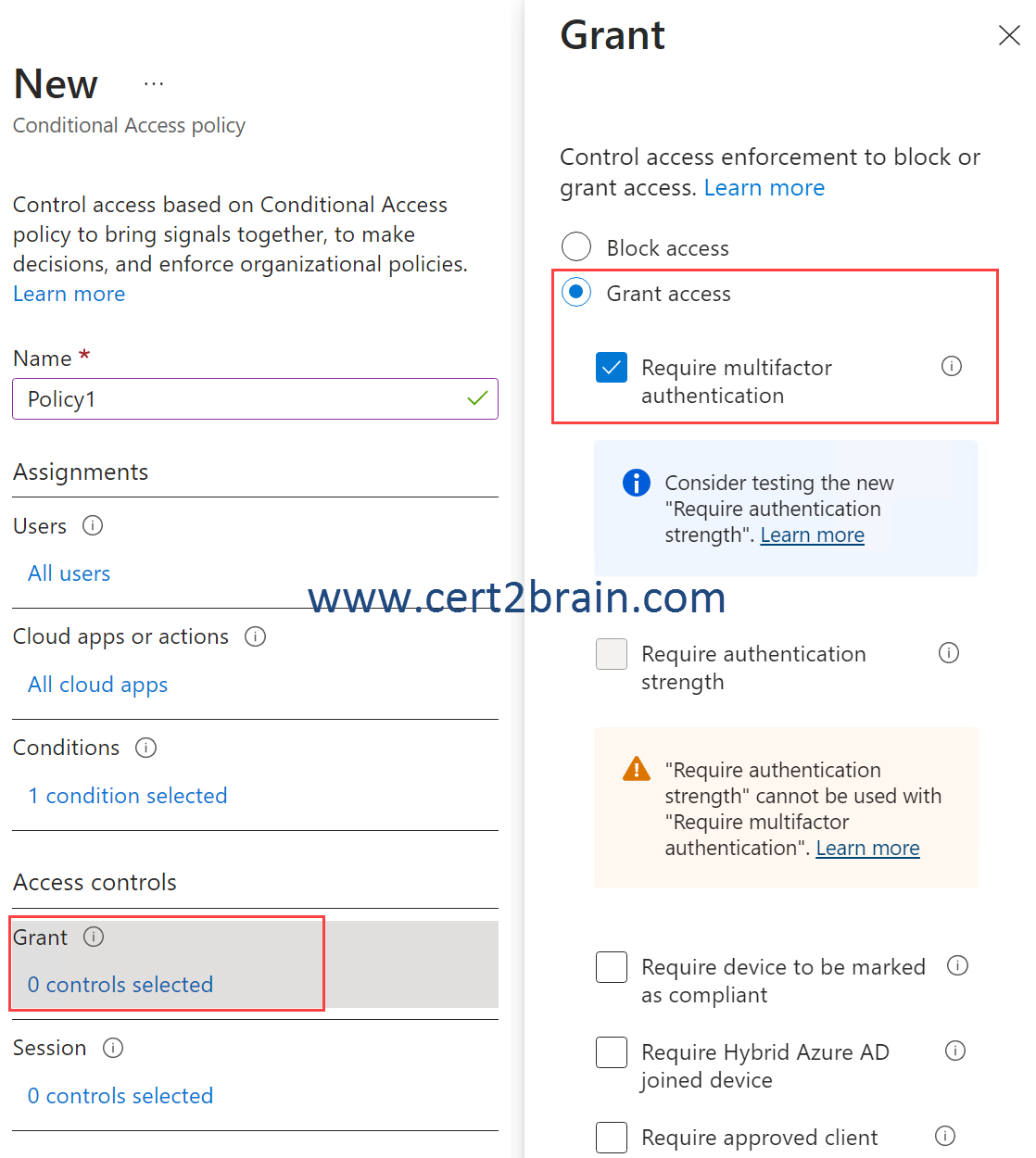
You create a Conditional Access policy named Policy1 and assign Policy1 to all users.
You need to configure Policy1 to enforce multi-factor authentication (MFA) if the user risk level is high.
Which two settings should you configure in Policy1?
(To answer, select the appropriate settings in the answer area. NOTE: Each correct selection is worth one point.)
| A | Assignments - Users |
| B | Assignments - Cloud apps or actions |
| C | Assignments - Conditions |
| D | Access controls - Grant |
| E | Access controls - Session |
Correct answer: C, DExplanation:
We need to configure Policy1 to apply only when the user risk is "High".
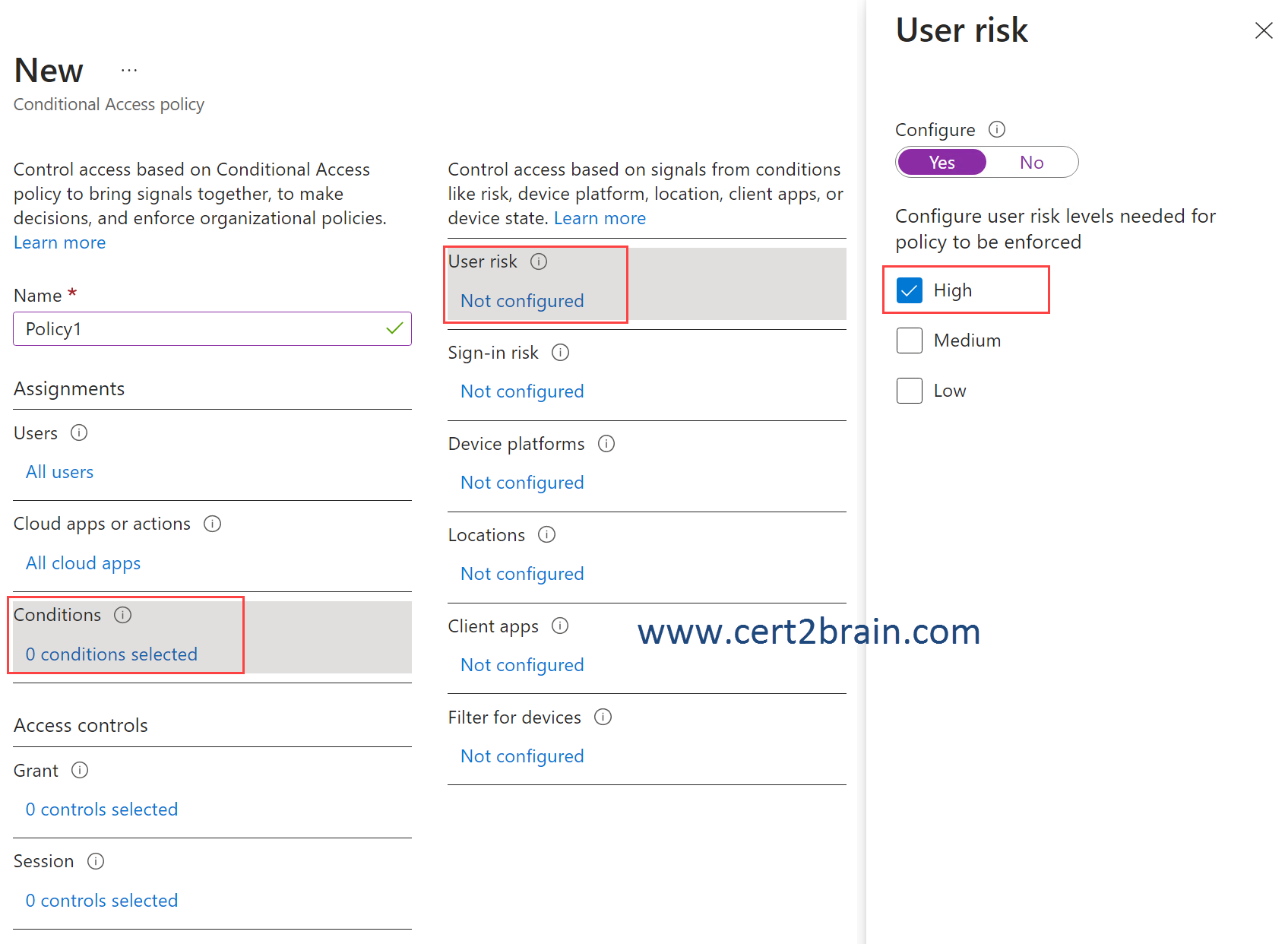
If the condition is met, multifactor authentication (MFA) must be required. For this purpose we need to configure the "Grant" access control.