Microsoft - MS-203: Microsoft 365 Messaging
Sample Questions
Question: 457
Measured Skill: Secure the messaging environment (25–30%)
You have a Microsoft Exchange Online tenant that contains a user named User1.
You need to ensure that User1 can import and export content from mailboxes. The solution must follow the principle of least privilege and minimize administrative effort.
What should you do?| A | Create and configure a custom role group and add User1. |
| B | Grant User1 Full Access permissions for the mailboxes. |
| C | Add User1 to Help Desk role group. |
| D | Add User1 to the Recipient Management role group. |
Correct answer: AExplanation:
Importing and exporting content from mailboxes requires the Mailbox Import Export role. The Mailbox Import Export role enables Administrators to import and export mailbox content and to purge unwanted content from a mailbox. By default the rol isn#T assigned to any role group.
Reference: Mailbox Import Export role
Question: 458
Measured Skill: Secure the messaging environment (25–30%)
You have a Microsoft Exchange Online tenant that contains two users named User1 and User2.
You need to ensure that the users can perform the tasks shown in the following table.
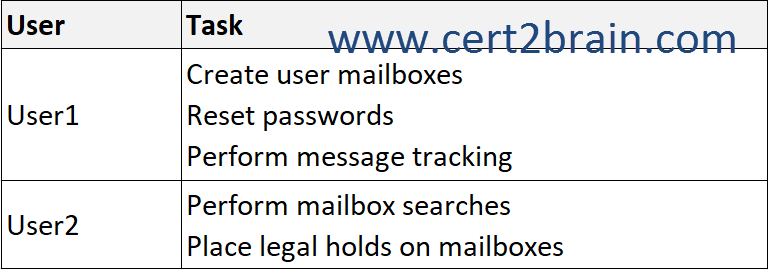
The solution must follow the principle of least privilege.
To which role group should you add each user?
(To answer, drag the appropriate role groups to the correct users. Each role group may be used once, more than once, or not at all. NOTE: Each correct selection is worth one point.)
| A | User1: Help Desk
User2: Recipient Management |
| B | User1: Discovery Management
User2: Help Desk |
| C | User1: Security Administrator
User2: Discovery Management |
| D | User1: Organization Management
User2: Security Administrator |
| E | User1: Recipient Management
User2: Discovery Management |
| F | User1: Help Desk
User2: Organization Management |
Correct answer: EExplanation:
Every administrator who manages Exchange Online must be assigned at least one or more roles. Administrators might have more than one role because they may perform job functions that span multiple areas in Exchange Online.
Discovery Management
Members can perform searches of mailboxes in the Exchange Online organization for data that meets specific criteria and can also configure legal holds on mailboxes.
Help Desk
Members can view and manage the configuration for individual recipients and view recipients in an Exchange organization. Members of this role group can only manage the configuration each user can manage on their own mailbox.
Organization Management
Members have administrative access to the entire Exchange Online organization and can perform almost any task in Exchange Online.
By default, the following management roles are not assigned to any role group, including Organization Management:
- Address Lists
- Mailbox Import Export
Recipient Management
Members have administrative access to create or modify Exchange Online recipients within the Exchange Online organization.
Security Administrator
Membership in this role group is synchronized across services and is managed centrally. You can't manage this role group in Exchange Online.
You can add members to this role group by adding users to the Microsoft Entra Security admin role in the Microsoft 365 admin center.
For a full list of the roles assigned to the role groups, see the article referenced below.
Reference: Permissions in Exchange Online
Question: 459
Measured Skill: Secure the messaging environment (25–30%)
You have a Microsoft Exchange Online tenant.
You create a custom role group named Role1.
You need to ensure that the members of Role1 can perform the following tasks:
- Retain the content of mailboxes for an indefinite amount of time.
- Find mailbox content based on a specific key word.
- Remove unwanted content from mailboxes.
Which three roles should you add to Role1?
(To answer, select the appropriate roles in the answer area. NOTE: Each correct selection is worth one point.)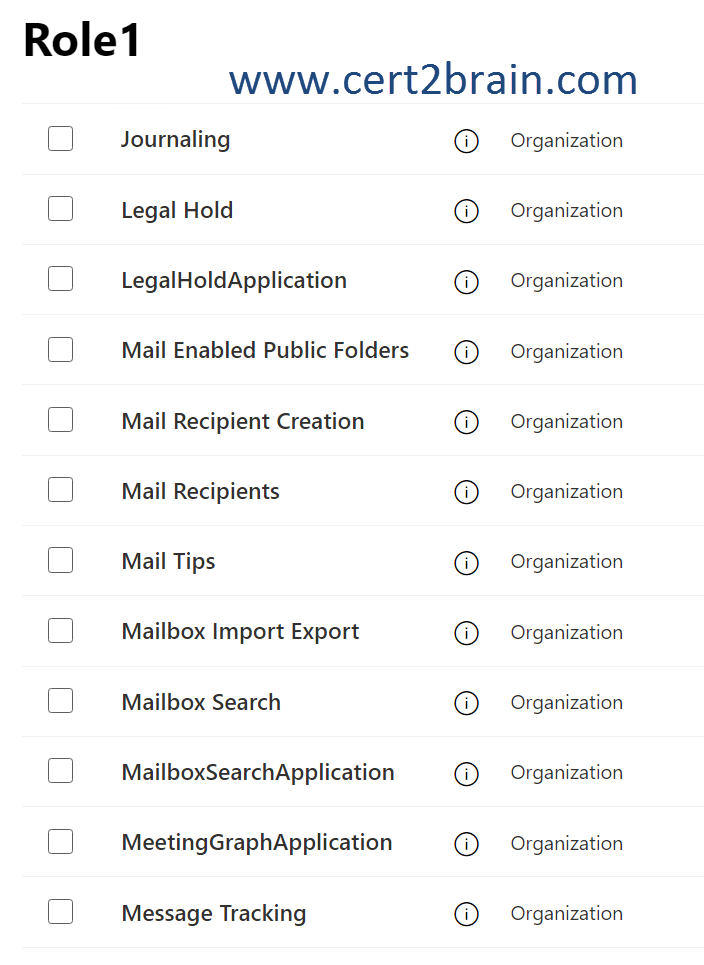
| A | Legal Hold |
| B | Mail Recipients |
| C | Mailbox Import Export |
| D | Mailbox Search |
| E | MailboxSearchApplication |
| F | Message Tracking |
Correct answer: A, C, DExplanation:
The Legal Hold role enables administrators to configure whether data within a mailbox should be retained for litigation purposes in an organization.
The Mailbox Search role enables administrators to search content of one or more mailboxes in an organization.
The Mailbox Import Export role enables administrators to import and export mailbox content and to purge unwanted content from a mailbox.
Question: 460
Measured Skill: Secure the messaging environment (25–30%)
You have a Micro soft Exchange Online tenant that contains a user named User1.
You need to find email messages that meet the following requirements:
- Contain the word ProjectX.
- Are located in the mailbox of User1.
The solution must retain all the messages that meet the requirements.
Which three actions should you perform in sequence?
(To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
| A | Sequence: 3, 5, 4 |
| B | Sequence: 6, 1, 2 |
| C | Sequence: 6, 2, 1 |
| D | Sequence: 3, 5, 2 |
Correct answer: CExplanation:
You can use a Microsoft Purview eDiscovery (Standard) case to create holds to preserve content that might be relevant to the case. You can place a hold on the Exchange mailboxes and OneDrive for Business accounts of people you're investigating in the case. You can also place a hold on the mailboxes and sites that are associated with Microsoft Teams, Microsoft 365 groups, and Viva Engage Groups. When you place content locations on hold, content is preserved until you remove the content location from the hold or until you delete the hold.
After you create an eDiscovery hold, it may take up to 24 hours for the hold to take effect.
When you create a hold, you have the following options to scope the content that's preserved in the specified content locations:
- Create an infinite hold where all content in the specified locations is placed on hold. Alternatively, you can create a query-based hold where only the content in the specified locations that matches a search query is placed on hold.
- Specify a date range to preserve only the content that was sent, received, or created within that date range. Alternatively, you can hold all content in specified locations regardless of when sent, received, or created.
Reference: Create eDiscovery holds in a eDiscovery (Standard) case
Question: 461
Measured Skill: Secure the messaging environment (25–30%)
You have a Microsoft Exchange Online tenant that uses Microsoft Defender XDR. You have a security group named Developers.
You need to configure threat policies for the Developers group. The solution must meet the following requirements:
- The Developers group must be able to receive email messages that have an ISO file attached.
- The Developers group must be able to identify and block spoof email.
Which type of policy should you configure for each requirement?
(To answer, drag the appropriate policy types to the correct requirements. Each policy type may be used once, more than once, or not at all. NOTE: Each correct selection is worth one point.)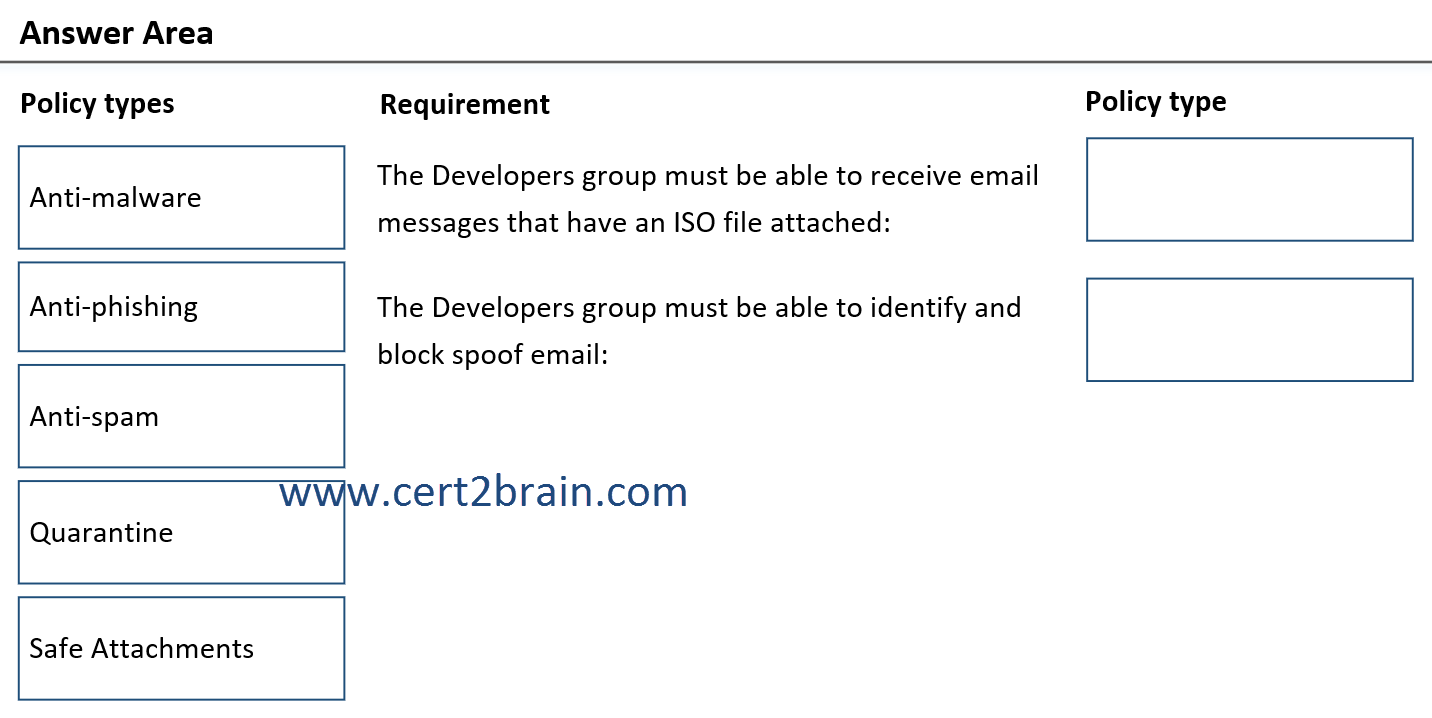
| A | The Developers group must be able to receive email messages that have an ISO file attached: Anti-malware
The Developers group must be able to identify and block spoof email: Anti-phishing |
| B | The Developers group must be able to receive email messages that have an ISO file attached: Anti-phishing
The Developers group must be able to identify and block spoof email: Anti-spam |
| C | The Developers group must be able to receive email messages that have an ISO file attached: Anti-spam
The Developers group must be able to identify and block spoof email: Anti-malware |
| D | The Developers group must be able to receive email messages that have an ISO file attached: Quarantine
The Developers group must be able to identify and block spoof email: Safe Attachments |
| E | The Developers group must be able to receive email messages that have an ISO file attached: Safe Attachments
The Developers group must be able to identify and block spoof email: Anti-spam |
| F | The Developers group must be able to receive email messages that have an ISO file attached: Safe Attachments
The Developers group must be able to identify and block spoof email: Quarantine |
Correct answer: AExplanation:
The protection settings of the Default (default) anti-malware policy has the common attachment filter set to block .iso files. We need to modify the policy or to create a new policy that allows .iso files to be received and apply the policy to the developers.
The spoof intelligence insight integrated in anti-phishing policies allows to review detected spoofed senders in messages from external and internal domains, and manually allow or block those detected senders.
References:
Common attachments filter in anti-malware policies
Anti-phishing protection in EOP