Archive - MS-220: Troubleshooting Microsoft Exchange Online
Sample Questions
Question: 89
Measured Skill: Troubleshoot compliance and retention issues (25–30%)
A company uses Exchange Online and the Unified Messaging (UM) service. The company enables journaling for all users.
You discover voice mail and missed call notifications in the journaling mailbox.
You need to exclude voicemail and missed call notifications from the journaling mailbox.
Which cmdlet should you run?| A | Set-TransportConfig |
| B | Set-TransportRule |
| C | Set-JournalRule |
| D | Set-MessageClassification |
Correct answer: AExplanation:
In Exchange Online, when you create a journal rule to journal email messages sent to or from recipients or senders in an Exchange organization, voice mail and missed call notifications generated by the Unified Messaging (UM) service are included.
Use PowerShell to disable or enable journaling of voice mail and missed call notifications.
The following command disables journaling of voice mail and missed call notifications by setting the VoicemailJournalingEnabled parameter to $false.
Set-TransportConfig -VoicemailJournalingEnabled $false
Reference: Enable or disable journaling of voice mail and missed call notifications in Exchange Online
Question: 90
Measured Skill: Troubleshoot compliance and retention issues (25–30%)
A company uses Exchange Online and implements Office 365 Message Encryption (OME).
Users report that they are unable to encrypt emails by using the Outlook on the web Protect button. Users are able to view encrypted emails that they receive.
You need to ensure that users can encrypt emails by using Outlook on the web.
How should you complete the command?
(To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.)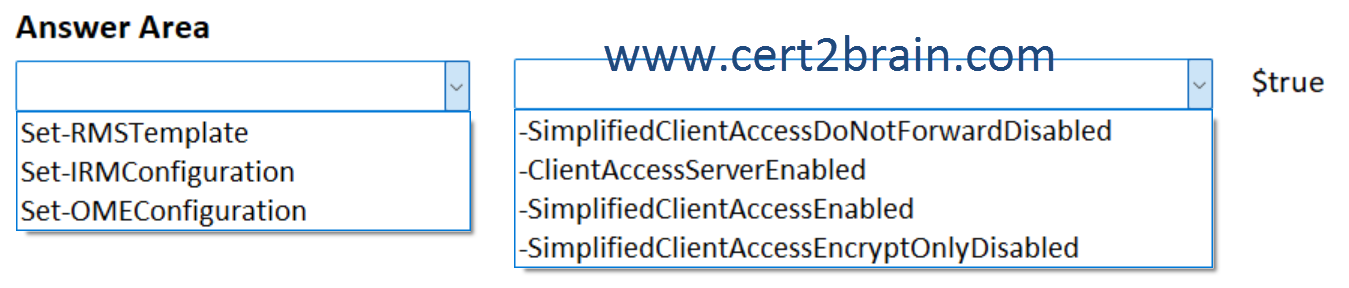
| A | Set-RMSTemplate -ClientAccessServerEnabled $true |
| B | Set-RMSTemplate -SimplifiedClientAccessDoNotForwardDisabled $true |
| C | Set-IRMConfiguration -SimplifiedClientAccessEnabled $true |
| D | Set-IRMConfiguration -ClientAccessServerEnabled $true |
| E | Set-OMEConfiguration -SimplifiedClientAccessEnabled $true |
| F | Set-OMEConfiguration -SimplifiedClientAccessEncryptOnlyDisabled $true |
Correct answer: CExplanation:
We should use the Set-IRMConfiguration cmdlet to configure the Information Rights Management (IRM) features and specify the SimplifiedClientAccessEnabled parameter to enable the Encrypt/Protect button.
The SimplifiedClientAccessEnabled parameter specifies whether to enable the Protect button in Outlook on the web. Valid values are:
- $true: The Protect button is enabled in Outlook on the web.
- $false: The Protect button is disabled in Outlook on the web. This is the default value.
References:
Encrypt button disappearing from Outlook
Set-IRMConfiguration
Question: 91
Measured Skill: Troubleshoot hybrid and migration issues (10–15%)
A company uses a Microsoft Exchange Server 2019 hybrid environment. The company is migrating mailboxes to Exchange Online.
You notice that the migration activity for larger mailboxes is slow. You review the migration logs and observe multiple instances of the following message:
StalledDueToTarget_MdbAvailability
You need to troubleshoot the issue.
What is the reason for the slow migrations?| A | There is a temporary interruption in the content indexing operations. |
| B | The disk latency on the Exchange Server is too high. |
| C | The replay queue of the transactions logs is too large. |
| D | The CPU utilization on the Exchange Server is too high. |
Correct answer: CExplanation:
Migration jobs to Exchange Online (which is a shared multi-tenancy environment) have a lower priority on Microsoft's servers and are sometimes throttled to protect the health of the datacenter resources (server performance, disks, databases). Workloads like client connectivity and mail flow have a higher priority as they have direct impact on user functionality. Mailbox migration is not considered as vital because things like mailbox moves are online moves (functionality is not impacted and access to mailboxes is mostly uninterrupted).
Knowing all that, it is perfectly normal to sometimes see stalls on the Office 365 side during migrations.
The migration side that stalls could be called ‘stall side’ and it can be different for onboarding vs. offboarding migration. Quick refresher on this:
- Onboarding: migrate from Exchange on-premises (source) to Exchange Online (target)
- Offboarding: migrate from Exchange Online (source) to Exchange on-premises (target)
Here are some most frequent stalls is Office 365 with their explanations; the examples are for an onboarding move, where target is Exchange Online environment.
- StalledDueToTarget_MdbAvailability: the move monitors replay queue of transactions logs into remote copies of databases. Migration stalls when the queue gets too big and will last until it drains.
- StalledDueToTarget_MdbReplication: the move monitors the copy queue of transactions logs to other DAG member servers.
- StalledDueToTarget_DiskLatency: happens when the disk latency is at a level where adding additional I/O might impact user experience on the disk where the target mailbox database (MDB) is located. Because of this, writes to the MDB are affected.
- StalledDueToTarget_Processor: happens when CPU utilization gets too high on target MRS servers involved in the move.
- StalledDueToTarget_BigFunnel: when content indexing operations experience a temporary interruption and are actively recovering.
Reference: Troubleshooting Slow Migrations
Question: 92
Measured Skill: Troubleshoot compliance and retention issues (25–30%)
A company uses Exchange Online. A user named User1 reports that emails are missing from their mailbox.
You perform an audit log search and are unable to locate any logs for User1.
You need to identify the cause of the missing audit logs.
Which two commands can you use?
(Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.)| A | Get-MsolUser –SearchString User1 | Format-List Licenses |
| B | Get-MailboxAuditBypassAssociation –Identity User1 | Format-List AuditByPassEnabled |
| C | Get-AdminAuditLogConfig | Format-List UnifiedAuditLogIngestionEnabled |
| D | Get-OrganizationConfig | Format-List AuditDisabled |
Correct answer: B, CExplanation:
Audit logging will be turned on by default for Microsoft 365 and Office 365 enterprise organizations. However, when setting up a new Microsoft 365 or Office 365 organization, you should verify the auditing status for your organization.
When auditing in the Microsoft Purview compliance portal is turned on, user and admin activity from your organization is recorded in the audit log and retained for 90 days, and up to one year depending on the license assigned to users. However, your organization may have reasons for not wanting to record and retain audit log data. In those cases, a global admin may decide to turn off auditing in Microsoft 365.
To verify that auditing is turned on for your organization, you can run the following command in Exchange Online PowerShell:
Get-AdminAuditLogConfig | FL UnifiedAuditLogIngestionEnabled
A value of True for the UnifiedAuditLogIngestionEnabled property indicates that auditing is turned on. A value of False indicates that auditing isn't turned on.
You can configure a user or computer account to bypass mailbox audit logging, so actions taken by that user or account for any mailbox aren't logged. By bypassing trusted user or computer accounts that need frequent access to mailboxes, you can reduce the noise in mailbox audit logs.
To verify if there is an audit bypass configured for User1, we should use the Get-MailboxAuditBypassAssociation cmdlet.
References:
Turn auditing on or off
Bypass a user account from mailbox audit logging
Question: 93
Measured Skill: Troubleshoot compliance and retention issues (25–30%)
A company uses Microsoft Exchange Server 2019. The company enabled journaling for all users.
Some emails are not being journaled because the journaling mailbox is not available.
You need to resolve the issue.
Which cmdlets should you run?
(To answer, drag the appropriate cmdlets to the correct configurations. Each cmdlet may be used once, more than once, or not at all. NOTE: Each correct selection is worth one point.)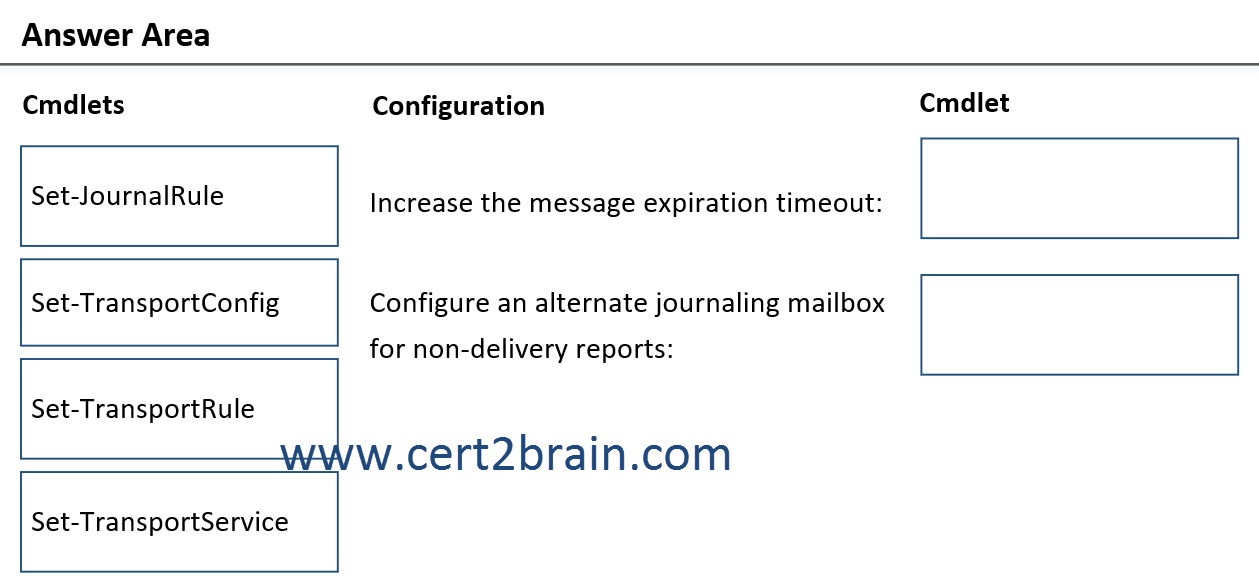
| A | Increase the message expiration timeout: Set-JournalRule
Configure an alternate journaling mailbox for non-delivery reports: Set-TransportRule |
| B | Increase the message expiration timeout: Set-TransportConfig
Configure an alternate journaling mailbox for non-delivery reports: Set-TransportService |
| C | Increase the message expiration timeout: Set-TransportConfig
Configure an alternate journaling mailbox for non-delivery reports: Set-JournalRule |
| D | Increase the message expiration timeout: Set-TransportRule
Configure an alternate journaling mailbox for non-delivery reports: Set-TransportService |
| E | Increase the message expiration timeout: Set-TransportRule
Configure an alternate journaling mailbox for non-delivery reports: Set-TransportConfig |
| F | Increase the message expiration timeout: Set-TransportService
Configure an alternate journaling mailbox for non-delivery reports: Set-TransportConfig |
Correct answer: FExplanation:
The MessageExpirationTimeout parameter of the Set-TransportService cmdlet specifies the maximum time that a particular message can remain in a queue. If a message remains in the queue for longer than this period of time, the message is returned to the sender as a permanent failure. The default value is 2 days.
The JournalingReportNdrTo parameter of the Set-TransportConfig cmdlet specifies the email address to which journal reports are sent if the journaling mailbox is unavailable. By default, if this parameter is left empty, Exchange continues to try to deliver the journal report to the journaling mailbox. Microsoft recommends that you use a dedicated (non-user) mailbox as the value for this parameter. Like the journaling mailbox, the alternate journaling mailbox can't be an Exchange Online mailbox.
References:
Journaling in Exchange Online
Set-TransportService
Set-TransportConfig