Archive - MS-500: Microsoft 365 Security Administration
Sample Questions
Question: 358
Measured Skill: Implement and manage identity and access (30-35%)
You plan to deploy a new Microsoft 365 subscription that will contain 500 users.
You need to ensure that the following actions are performed when the users sign in to the subscription:
- Evaluate the users' risk level based on their location and travel.
- Require high-risk users to sign in by using Azure Multi-Factor Authentication (Azure MFA).
The solution must minimize cost.
Which license should you assign to each user?| A | Microsoft 365 Business Premium |
| B | Microsoft 365 E3 |
| C | Enterprise Mobility + Security E3 |
| D | Microsoft 365 E5 |
Correct answer: DExplanation:
We must ensure, that the licenses include Azure Identity Protection. Identity Protection provides organizations with three reports they can use to investigate identity risks in their environment. These reports are the risky users, risky sign-ins, and risk detections. Investigation of events is key to better understanding and identifying any weak points in your security strategy.
Identity Protection detects risks of many types, including:
- Anonymous IP address use
- Atypical travel
- Malware linked IP address
- Unfamiliar sign-in properties
- Leaked credentials
- Password spray
- and more...
The risk signals can trigger remediation efforts such as requiring: perform multifactor authentication, reset their password using self-service password reset, or block access until an administrator takes action.
User risk policy (via Identity Protection) and Sign-in risk policy (via Identity Protection or Conditional Access) require an Azure AD Premium P2 license which is included in Microsoft 365 E5.
Note: The Microsoft 365 Business Basic, Apps for business, Business Standard, and Business Premium plans each have a limit of 300 users, while the Enterprise plans are for an unlimited number of users.
References:
What is Identity Protection?
How To: Investigate risk
Question: 359
Measured Skill: Manage governance and compliance features in Microsoft 365 (25-30%)
You have a Microsoft 365 subscription that contains two groups named Group1 and Group2.
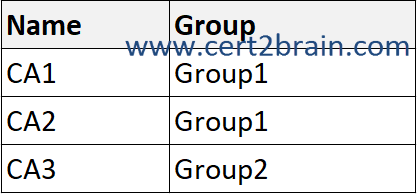
You have the compliance assessments shown in the following table.
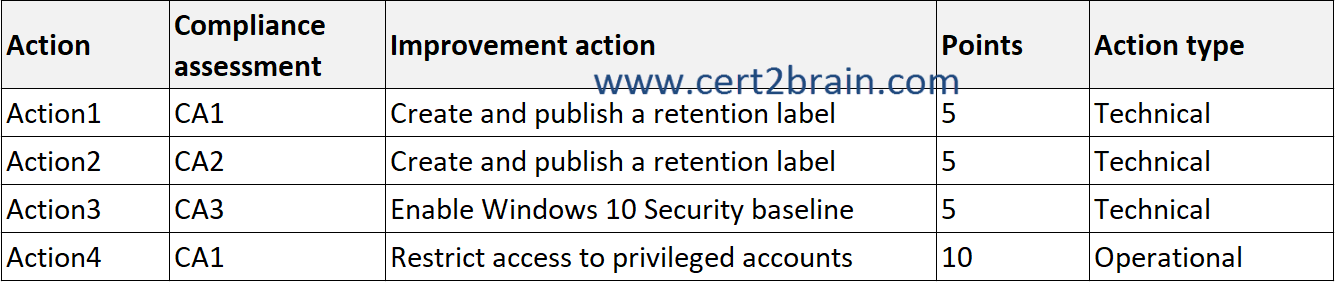
You have the improvements actions shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
( NOTE: Each correct selection is worth one point.)
| A | The compliance score for CA1 will increase by 15 points: Yes
The compliance score for CA2 will increase by 15 points: Yes
The compliance score for CA3 will increase by 10 points: Yes |
| B | The compliance score for CA1 will increase by 15 points: Yes
The compliance score for CA2 will increase by 15 points: No
The compliance score for CA3 will increase by 10 points: No |
| C | The compliance score for CA1 will increase by 15 points: Yes
The compliance score for CA2 will increase by 15 points: No
The compliance score for CA3 will increase by 10 points: Yes |
| D | The compliance score for CA1 will increase by 15 points: No
The compliance score for CA2 will increase by 15 points: Yes
The compliance score for CA3 will increase by 10 points: No |
| E | The compliance score for CA1 will increase by 15 points: No
The compliance score for CA2 will increase by 15 points: Yes
The compliance score for CA3 will increase by 10 points: Yes |
| F | The compliance score for CA1 will increase by 15 points: No
The compliance score for CA2 will increase by 15 points: No
The compliance score for CA3 will increase by 10 points: No |
Correct answer: BExplanation:
The Compliance Manager dashboard displays your overall compliance score. This score measures your progress in completing recommended improvement actions within controls. Your score can help you understand your current compliance posture. It can also help you prioritize actions based on their potential to reduce risk.
A score value is assigned at these levels:
-
Improvement action: Each action has a different impact on your score depending on the potential risk involved.
-
Assessment: This score is calculated using improvement action scores. Each Microsoft action and each improvement action managed by your organization is counted once, regardless of how often it's referenced in a control.
The overall compliance score is calculated using action scores, where each Microsoft action is counted once, each technical action you manage is counted once, and each non-technical action you manage is counted once per group. This logic is designed to provide the most accurate accounting of how actions are implemented and tested in your organization. You may notice that this can cause your overall compliance score to differ from the average of your assessment scores.
References:
Microsoft Purview Compliance Manager
Compliance score calculation
Question: 360
Measured Skill: Implement and manage identity and access (30-35%)
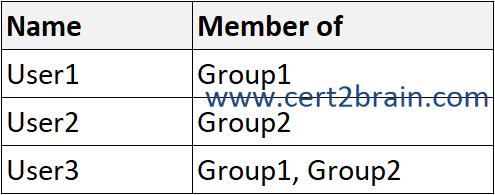
You have a Microsoft 365 E5 subscription that is linked to an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains three groups named Group1, Group2, and Group3 and the users shown in the following table.
You create a new access package as shown in the following exhibit.
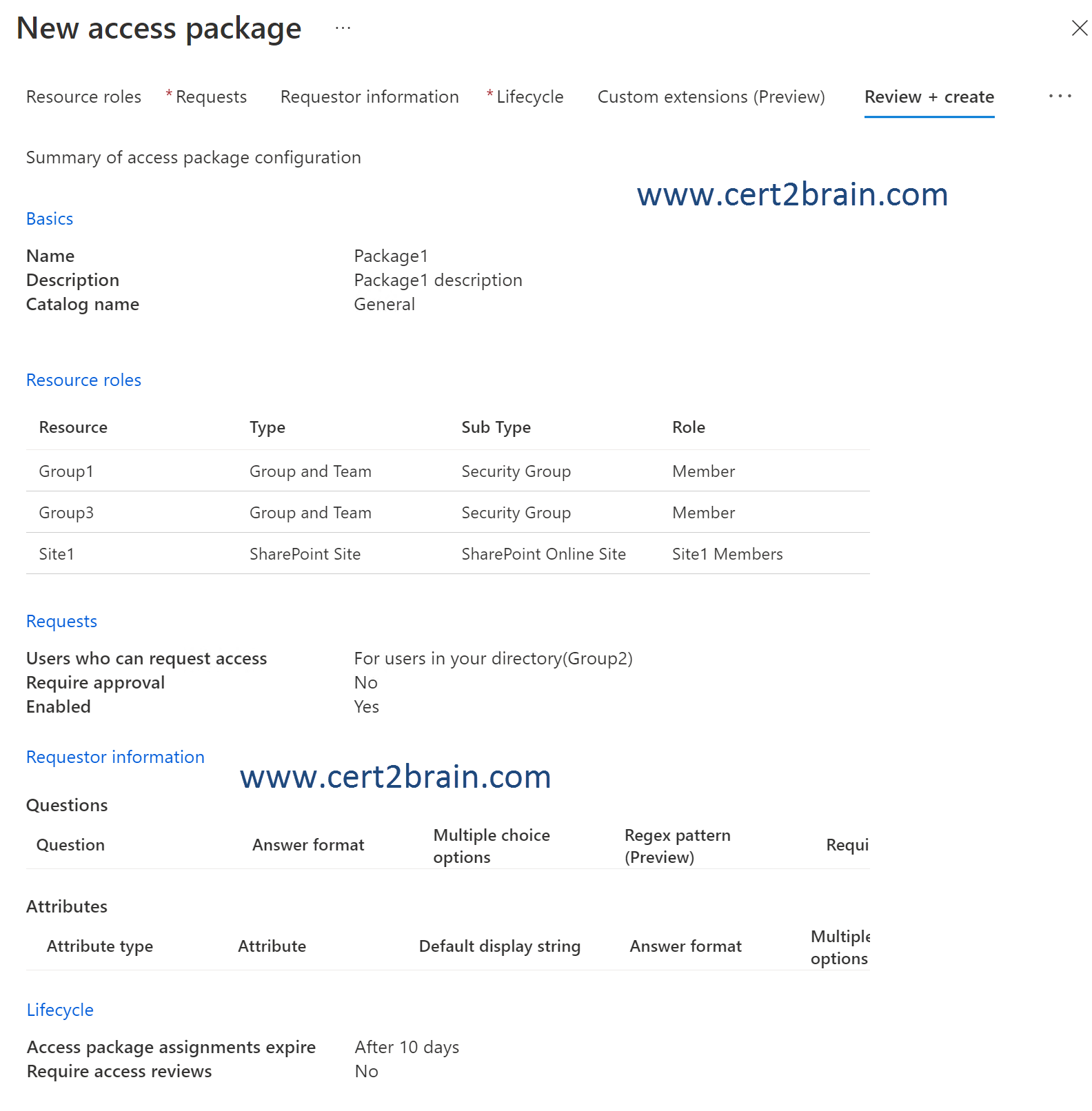
You assign Package1 on June 1, 2022, by using die following configurations:
- Select users: User1, User2, User3
- Select policy: Initial policy
- Assignment starts: June 1, 2022
- Assignment ends: July 1, 2022
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
(NOTE: Each correct selection is worth one point.)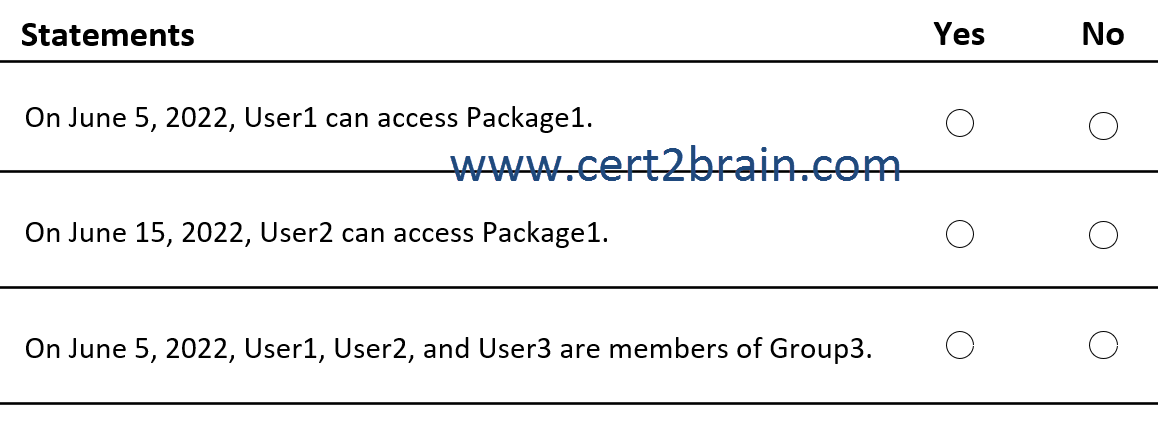
| A | On June 5, 2022, User1 can access Package1: Yes
On June 15, 2022, User2 can access Package1: Yes
On June 5, 2022, User1, User2, and User3 are members of Group3: Yes |
| B | On June 5, 2022, User1 can access Package1: Yes
On June 15, 2022, User2 can access Package1: Yes
On June 5, 2022, User1, User2, and User3 are members of Group3: No |
| C | On June 5, 2022, User1 can access Package1: Yes
On June 15, 2022, User2 can access Package1: No
On June 5, 2022, User1, User2, and User3 are members of Group3: Yes |
| D | On June 5, 2022, User1 can access Package1: No
On June 15, 2022, User2 can access Package1: Yes
On June 5, 2022, User1, User2, and User3 are members of Group3: Yes |
| E | On June 5, 2022, User1 can access Package1: No
On June 15, 2022, User2 can access Package1: No
On June 5, 2022, User1, User2, and User3 are members of Group3: Yes |
| F | On June 5, 2022, User1 can access Package1: No
On June 15, 2022, User2 can access Package1: No
On June 5, 2022, User1, User2, and User3 are members of Group3: No |
Correct answer: FExplanation:
An access package enables you to do a one-time setup of resources and policies that automatically administers access for the life of the access package.
All access packages must have at least one policy for users to be assigned to the access package. Policies specify who can request the access package and also approval and lifecycle settings.
Access to Package1 can be requested by members of Group2 only.
User1 cannot access Package1 because User1 is not a member of Group2.
User2 is a member of Group2 and can access Package1 until June 10, 2022 only because the access package assignments expire 10 days after the initial assignment on June 1, 2022.
The access package does not assign users to groups.
References:
What is entitlement management?
Create a new access package in entitlement management
Question: 361
Measured Skill: Manage governance and compliance features in Microsoft 365 (25-30%)
You have a Microsoft 365 subscription that contains 100 users.
Microsoft Secure Score for the subscription is shown in the following exhibit.
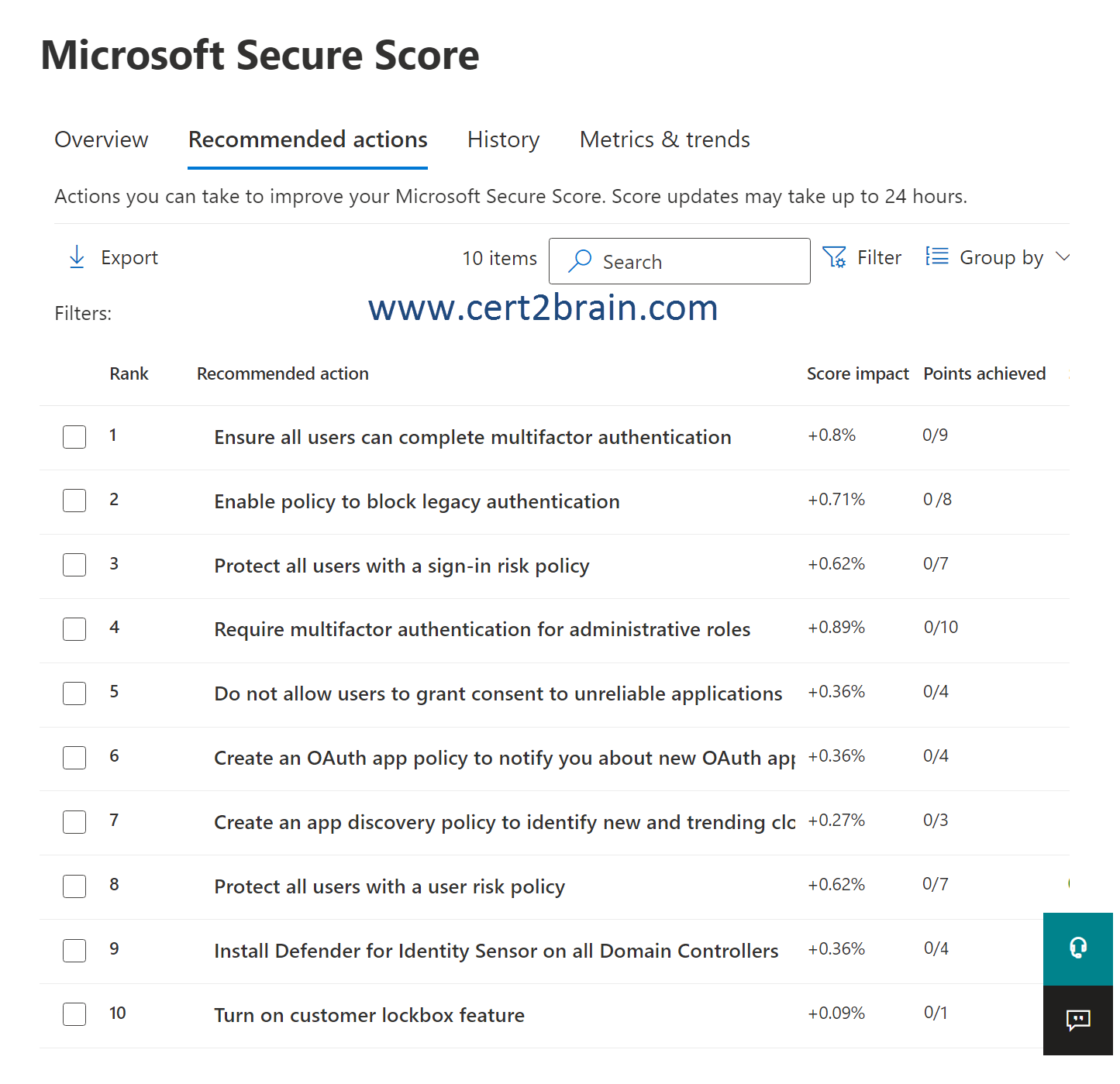
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
(NOTE: Each correct selection is worth one point.)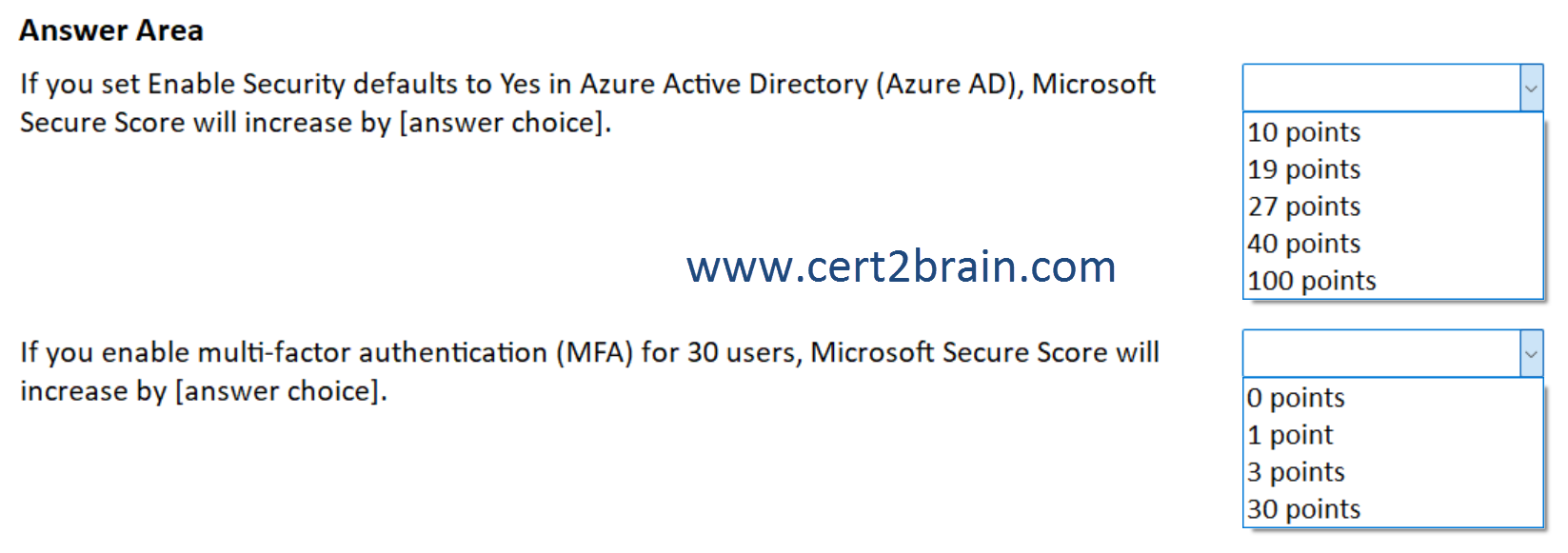
| A | If you set Enable Security defaults to Yes in Azure Active Directory (Azure AD), Microsoft Secure Score will increase by 10 points.
If you enable multi-factor authentication (MFA) for 30 users, Microsoft Secure Score will increase by 3 points. |
| B | If you set Enable Security defaults to Yes in Azure Active Directory (Azure AD), Microsoft Secure Score will increase by 19 points.
If you enable multi-factor authentication (MFA) for 30 users, Microsoft Secure Score will increase by 30 points. |
| C | If you set Enable Security defaults to Yes in Azure Active Directory (Azure AD), Microsoft Secure Score will increase by 19 points.
If you enable multi-factor authentication (MFA) for 30 users, Microsoft Secure Score will increase by 0 points. |
| D | If you set Enable Security defaults to Yes in Azure Active Directory (Azure AD), Microsoft Secure Score will increase by 27 points.
If you enable multi-factor authentication (MFA) for 30 users, Microsoft Secure Score will increase by 3 points. |
| E | If you set Enable Security defaults to Yes in Azure Active Directory (Azure AD), Microsoft Secure Score will increase by 40 points.
If you enable multi-factor authentication (MFA) for 30 users, Microsoft Secure Score will increase by 1 point. |
| F | If you set Enable Security defaults to Yes in Azure Active Directory (Azure AD), Microsoft Secure Score will increase by 100 points.
If you enable multi-factor authentication (MFA) for 30 users, Microsoft Secure Score will increase by 30 points. |
Correct answer: DExplanation:
Microsoft Secure Score has updated recommended actions to support security defaults in Azure Active Directory, which make it easier to help protect your organization with pre-configured security settings for common attacks.
If you turn on security defaults, you'll be awarded full points for the following recommended actions:
- Ensure all users can complete multi-factor authentication for secure access (9 points)
- Require MFA for administrative roles (10 points)
- Enable policy to block legacy authentication (8 points)
Some recommended actions only give points when fully completed. Some give partial points if they're completed for some devices or users. If you can't or don't want to enact one of the recommended actions, you can choose to accept the risk or remaining risk.
If we enable MFA for 30 out of 100 users, we will get 30/100 * 9 points = 2.7 points.
Reference: Microsoft Secure Score
Question: 362
Measured Skill: Implement and manage identity and access (30-35%)
You have a Microsoft 365 E5 subscription linked to an Azure Active Directory (Azure AD) tenant.
The tenant contains a user named User1 and multiple Windows10 devices. The devices are Azure AD joined and protected by using BitLocker Drive Encryption (BitLocker).
You need to ensure that User1 can perform the following actions:
- View BitLocker recovery keys.
- Configure the usage location for the users in the tenant.
The solution must use the principle of least privilege.
Which two roles should you assign to User1 in the Microsoft 365 admin center?
(To answer, select the appropriate roles in the answer area. NOTE: Each correct selection is worth one point.)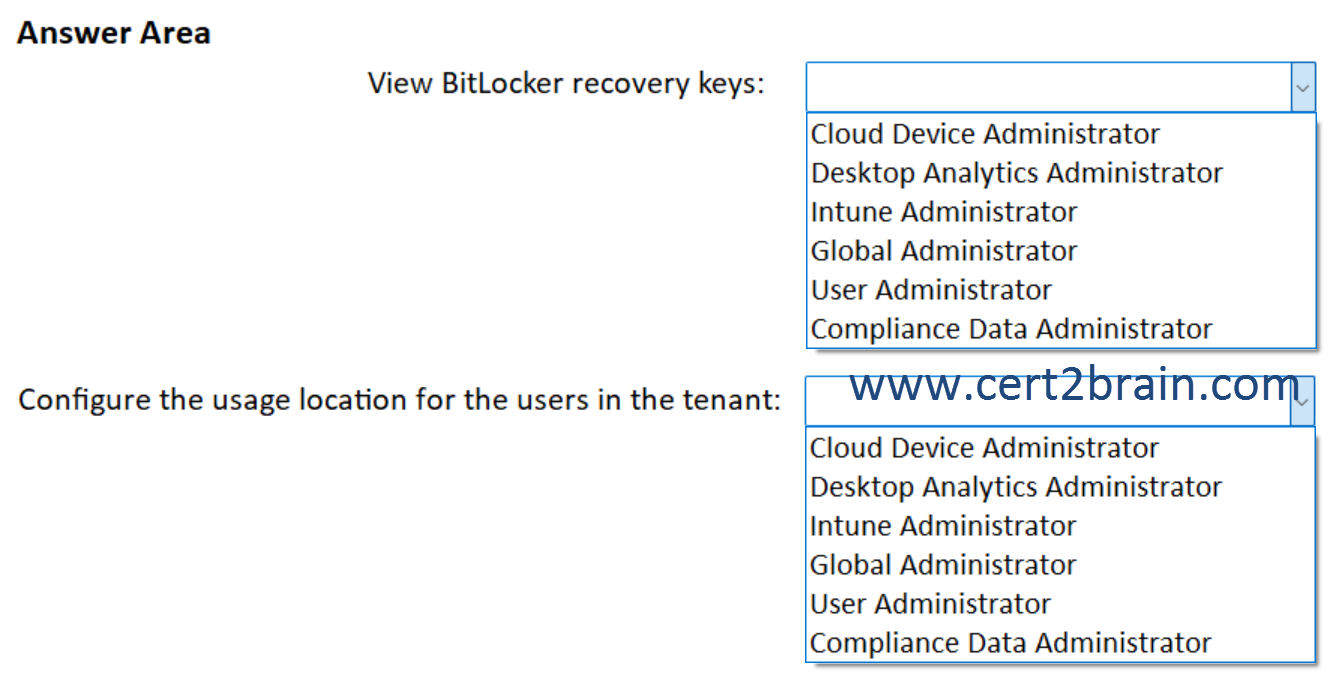
| A | View BitLocker recovery keys: Intune Administrator
Configure the usage location for the users in the tenant: Cloud Device Administrator |
| B | View BitLocker recovery keys: Cloud Device Administrator
Configure the usage location for the users in the tenant: User Administrator |
| C | View BitLocker recovery keys: Global Administrator
Configure the usage location for the users in the tenant: Global Administrator |
| D | View BitLocker recovery keys: User Administrator
Configure the usage location for the users in the tenant: Global Administrator |
| E | View BitLocker recovery keys: Compliance Data Administrator
Configure the usage location for the users in the tenant: Intune Administrator |
| F | View BitLocker recovery keys: Intune Administrator
Configure the usage location for the users in the tenant: Compliance Data Administrator |
Correct answer: BExplanation:
Cloud Device Administrators can enable, disable, and delete devices in Azure AD and read Windows 10 BitLocker keys (if present) in the Azure portal. The role does not grant permissions to manage any other properties on the device.
User Administrators can update most user properties, including the usage location, for all users, including all administrators.
References:
Cloud Device Administrator
User Administrator