Microsoft - MS-900: Microsoft 365 Fundamentals
Sample Questions
Question: 475
Measured Skill: Describe Microsoft 365 apps and services (45–50%)
A company uses Teams for meetings and Microsoft Stream to store training videos.
The company requires that users be able to perform the following actions:
- Retrieve a quick summary of a video.
- Retrieve outcomes and key points about a video by using open-ended questions.
You need to recommend a solution.
Select the answer that correctly completes the sentence.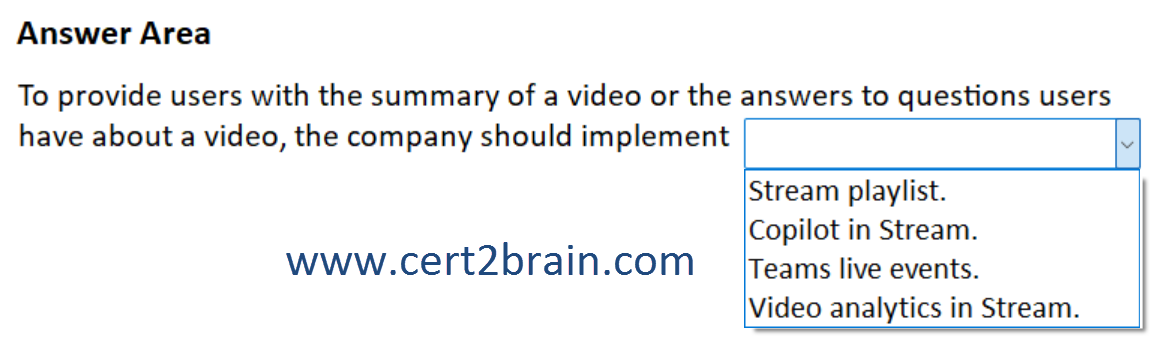
| A | To provide users with the summary of a video or the answers to questions users have about a video, the company should implement Stream playlist. |
| B | To provide users with the summary of a video or the answers to questions users have about a video, the company should implement Copilot in Stream. |
| C | To provide users with the summary of a video or the answers to questions users have about a video, the company should implement Teams live events. |
| D | To provide users with the summary of a video or the answers to questions users have about a video, the company should implement Video analytics in Stream. |
Correct answer: BExplanation:
Copilot in Microsoft Stream helps you to quickly and effectively catch up to videos in your organization.?Whether you missed a meeting or are watching the latest town hall, product demo, or how-to video, Copilot can quickly summarize and answer questions for any video with a transcript.
Reference: Ask questions & get summaries of any video with Microsoft Copilot in Stream
Question: 476
Measured Skill: Describe security, compliance, privacy, and trust in Microsoft 365 (25–30%)
A company is evaluating Microsoft 365 and Microsoft Entra solutions.
You need to describe the External Identities features in Microsoft Entra,
Match each External identity to its capability.
(To answer, move the appropriate External Identity from the column on the left to its capability on the right. You may use each External Identity once, more than once, or not at all. NOTE: Each correct match is worth one point.)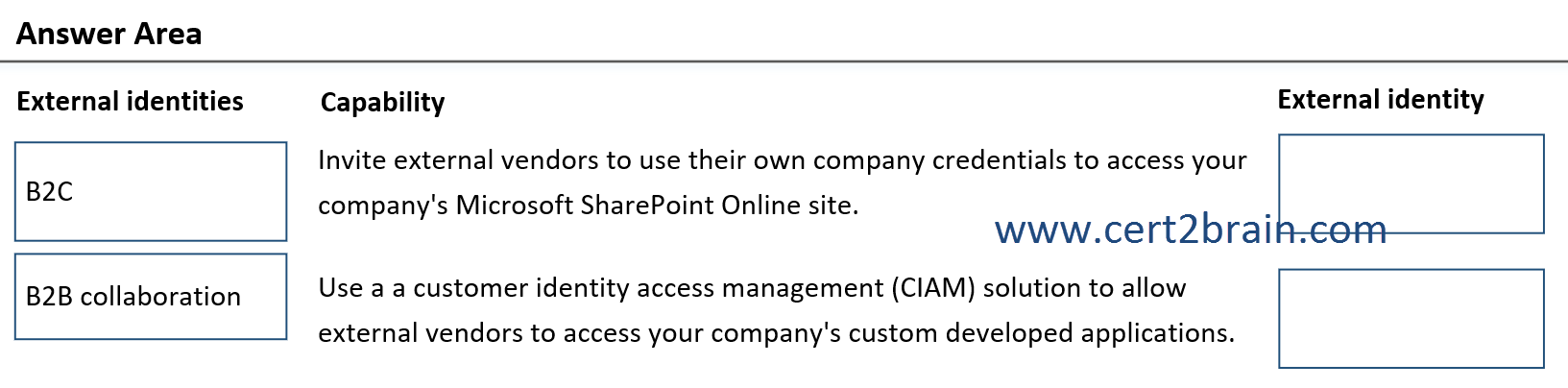
| A | P1: B2C
P2: B2B collaboration |
| B | P1: B2C
P2: B2C |
| C | P1: B2B collaboration
P2: B2C |
| D | P1: B2B collaboration
P2: B2B collaboration |
Correct answer: CExplanation:
Microsoft Entra External ID includes collaboration capabilities that allow your workforce to work securely with business partners and guests. In your workforce tenant, you can use B2B collaboration to share your company's applications and services with guests, while maintaining control over your own corporate data. Work securely with external partners, even if they don't have Microsoft Entra ID or an IT department.
A simple invitation and redemption process lets partners use their own credentials to access your company's resources. You can also enable self-service sign-up user flows to let guests sign up for apps or resources themselves. Once the guest redeems their invitation or completes sign-up, they're represented in your directory as a user object. The user type for these B2B collaboration users is typically set to "guest" and their user principal name contains the #EXT# identifier.
Azure Active Directory B2C provides business-to-customer identity as a service. Your customers can use their preferred social, enterprise, or local account identities to get single sign-on access to your applications and APIs.
Azure AD B2C is a customer identity access management (CIAM) solution capable of supporting millions of users and billions of authentications per day. It takes care of the scaling and safety of the authentication platform, monitoring, and automatically handling threats like denial-of-service, password spray, or brute force attacks.
Azure AD B2C is built on the same technology as Microsoft Entra ID but for a different purpose and is a separate service. It allows businesses to build customer facing applications, and then allow anyone to sign up and sign in to those applications with no restrictions on user account.
References:
Overview: B2B collaboration with external guests for your workforce
What is Azure Active Directory B2C?
Question: 477
Measured Skill: Describe Microsoft 365 pricing, licensing, and support (10–15%)
You are using Microsoft 365 services with a Cloud Services Provider (CSP).
The CSP informs you that the monthly uptime of your Microsoft 365 services for the previous month was 97%.
You need to determine the service credit that you should receive from Microsoft.
Which service credit percentage should you receive?Correct answer: CExplanation:
If Microsoft does not achieve and maintain the Service Levels for each Service as described in the Service Level Agreement (SLA), then you may be eligible for a credit towards a portion of your monthly service fees.
Service Credit is the percentage of the Applicable Service Fees credited to you following Microsoft’s claim approval. Credit requests are accepted only from CSP direct and indirect providers.
Downtime is any period of time when end users are unable to login to their instance.
Uptime Percentage: The Uptime Percentage is calculated using the following formula:
(User Minutes - Downtime) / (User Minutes) x 100
Microsoft 365 SLA for Uptime and Service Credits:
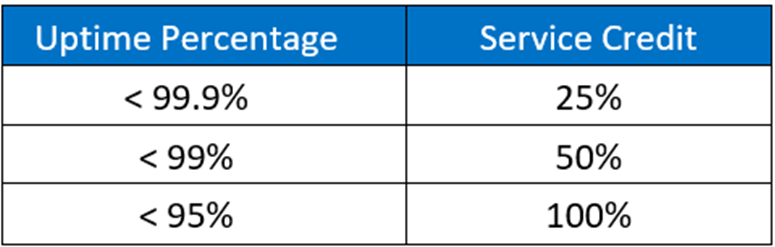
References:
How and when to request a credit from Microsoft
Service Level Agreements (SLA) for Online Services
Question: 478
Measured Skill: Describe Microsoft 365 apps and services (45–50%)
A company is using Microsoft 365.
The company plans to build custom apps and requires a low code development environment.
You need to recommend a solution.
Which tool should you use?| A | Microsoft Sentinel |
| B | Microsoft Power Apps |
| C | Microsoft Power BI |
| D | Microsoft Power Automate |
| E | Microsoft Viva |
Correct answer: BExplanation:
Power Apps is a suite of apps, services, and connectors, as well as a data platform, that provides a rapid development environment to build custom apps for your business needs. Using Power Apps, you can quickly build custom business apps that connect to your data stored either in the underlying data platform (Microsoft Dataverse) or in many online and on-premises data sources (such as SharePoint, Microsoft 365, Dynamics 365, SQL Server, and so on).
Apps built using Power Apps provide rich business logic and workflow capabilities to transform your manual business operations into digital, automated processes. What's more, apps built using Power Apps have a responsive design and can run seamlessly in browser and on mobile devices (phone or tablet). Power Apps "democratizes" the business-app-building experience by enabling users to create feature-rich, custom business apps without writing code.
Power Apps also provides an extensible platform that lets pro developers programmatically interact with data and metadata, apply business logic, create custom connectors, and integrate with external data.
Power Apps and Microsoft Copilot let you describe the app you want and AI designs it. Make edits, add automation, and write code—all with Copilot in Power Apps.
Reference: What is Power Apps?
Question: 479
Measured Skill: Describe Microsoft 365 apps and services (45–50%)
A company is using Microsoft 365.
The company has several reporting requirements, including that it must be able to view:
- Information about security trends and track the protection status of identities, data, devices, apps, and infrastructure.
- Status and trends for the compliance of Microsoft 365 devices, data, identities, apps, and infrastructure.
- Activity reports that include device registration and usage, and user sign-in activity.
You need to recommend the correct admin center for the company to use based on its reporting requirements.
Which admin center should you use?
(To answer, move the appropriate admin center to the correct reporting requirement. You may use each admin center once, more than once, or not at all. NOTE: Each correct selection is worth one point.)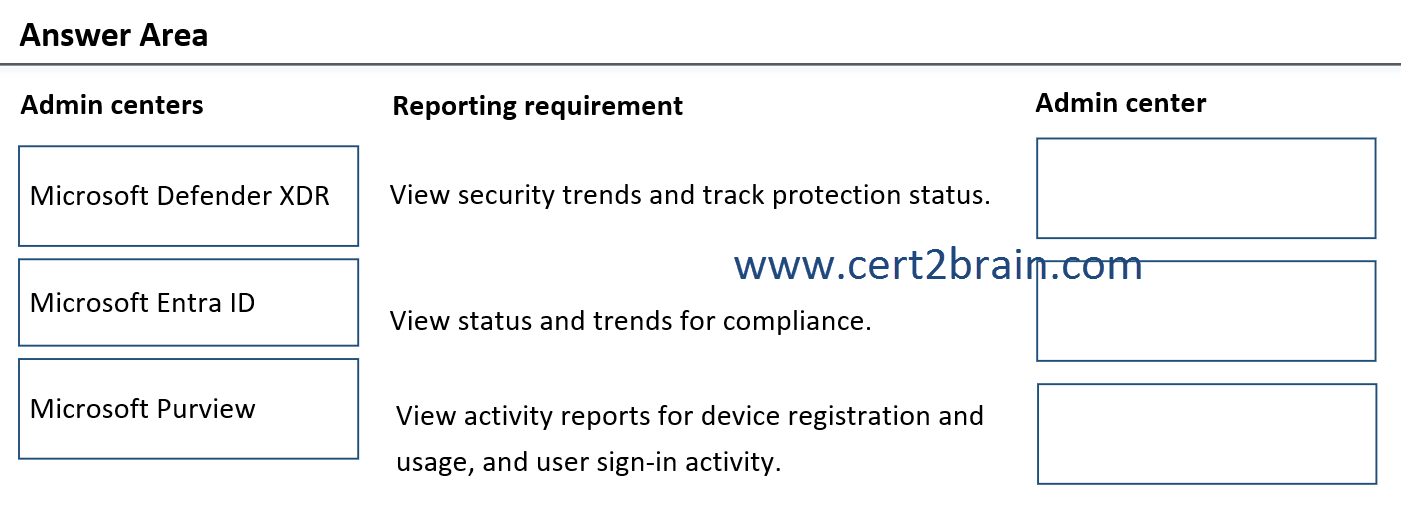
| A | View security trends and track protection status: Microsoft Defender XDR
View status and trends for compliance: Microsoft Entra ID
View activity reports for device registration and usage, and user sign-in activity: Microsoft Purview |
| B | View security trends and track protection status: Microsoft Defender XDR
View status and trends for compliance: Microsoft Purview
View activity reports for device registration and usage, and user sign-in activity: Microsoft Entra ID |
| C | View security trends and track protection status: Microsoft Entra ID
View status and trends for compliance: Microsoft Purview
View activity reports for device registration and usage, and user sign-in activity: Microsoft Defender XDR |
| D | View security trends and track protection status: Microsoft Entra ID
View status and trends for compliance: Microsoft Defender XDR
View activity reports for device registration and usage, and user sign-in activity: Microsoft Purview |
| E | View security trends and track protection status: Microsoft Purview
View status and trends for compliance: Microsoft Entra ID
View activity reports for device registration and usage, and user sign-in activity: Microsoft Defender XDR |
| F | View security trends and track protection status: Microsoft Purview
View status and trends for compliance: Microsoft Defender XDR
View activity reports for device registration and usage, and user sign-in activity: Microsoft Entra ID |
Correct answer: BExplanation:
Microsoft Defender XDR is a unified pre- and post-breach enterprise defense suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks. Microsoft Defender XDR correlates signals from various Microsoft security solutions in the Microsoft Defender portal to help security teams investigate and respond to attacks.
Microsoft Purview is a comprehensive set of solutions that can help you govern, protect, and manage data in your organization. The Microsoft Purview portal has a streamlined design and unified experience that helps you discover and access data security, data governance, and risk and compliance solutions for all your data, wherever it lives across your data estate. The unified experience streamlines navigation for all Purview solutions and provides a single-entry point for settings, search, and roles and permissions management.
With the Microsoft Entra Usage and insights reports, you can get an application-centric view of your sign-in data. Usage & insights includes a report on authentication methods, service principal sign-ins, and application credential activity.
References:
What is Microsoft Defender XDR?
Learn about the new Microsoft Purview portal
What is the Usage and insights report in Microsoft Entra ID?