Archive - SC-400: Administering Information Protection and Compliance in Microsoft 365
Sample Questions
Question: 349
Measured Skill: Manage insider and privacy risk in Microsoft 365 (15–20%)
You have a Microsoft 365 E5 subscription that contains a user named User1.
You need to ensure that User1 can perform the following tasks:
- View the Privacy risk management Data profile page and subject rights request reports.
- Add approvers for subject rights requests.
The solution must follow the principle of least privilege.
To which role group should you add User1 for each task?
(To answer, drag the appropriate role groups to the correct tasks. Each role group may be used once, more than once, or not at all. NOTE: Each correct selection is worth one point.)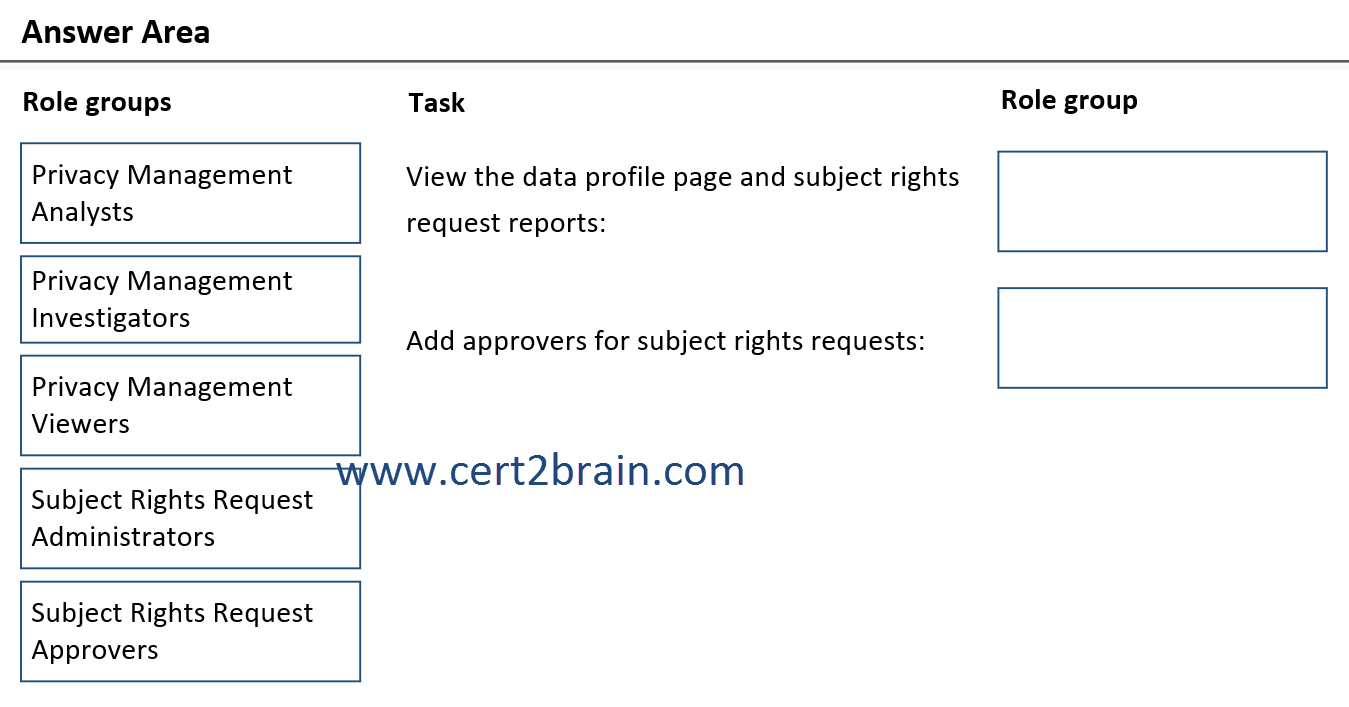
| A | View the data profile page and subject rights request reports: Privacy Management Analysts
Add approvers for subject rights requests: Subject Rights Request Administrators |
| B | View the data profile page and subject rights request reports: Privacy Management Analysts
Add approvers for subject rights requests: Subject Rights Request Approvers |
| C | View the data profile page and subject rights request reports: Privacy Management Investigators
Add approvers for subject rights requests: Subject Rights Request Administrators |
| D | View the data profile page and subject rights request reports: Privacy Management Investigators
Add approvers for subject rights requests: Subject Rights Request Approvers |
| E | View the data profile page and subject rights request reports: Privacy Management Viewer
Add approvers for subject rights requests: Subject Rights Request Administrators |
| F | View the data profile page and subject rights request reports: Privacy Management Viewer
Add approvers for subject rights requests: Subject Rights Request Approvers |
Correct answer: EExplanation:
Depending on the structure of your team, you have options to assign users to specific role groups to manage different sets of Priva features. Members should be assigned to role groups depending on what tasks they need to accomplish and what level of access is appropriate. Each role group includes one or more roles. These roles might pertain to specific Priva tasks or key functions that are enabled or restricted for that group’s members. Different users might therefore have different levels of visibility and access into certain Priva features.
Roles and role groups for GA solutions
If you're using:
- Privacy Risk Management
- Subject Rights Requests for data within Microsoft 365
Most Priva roles for Privacy Risk Management and Subject Rights Requests for data within Microsoft 365 are designated as "Privacy Management" in the Microsoft Purview solutions section in Settings --> Permissions. Roles specific to Priva don't appear in Microsoft Entra ID.
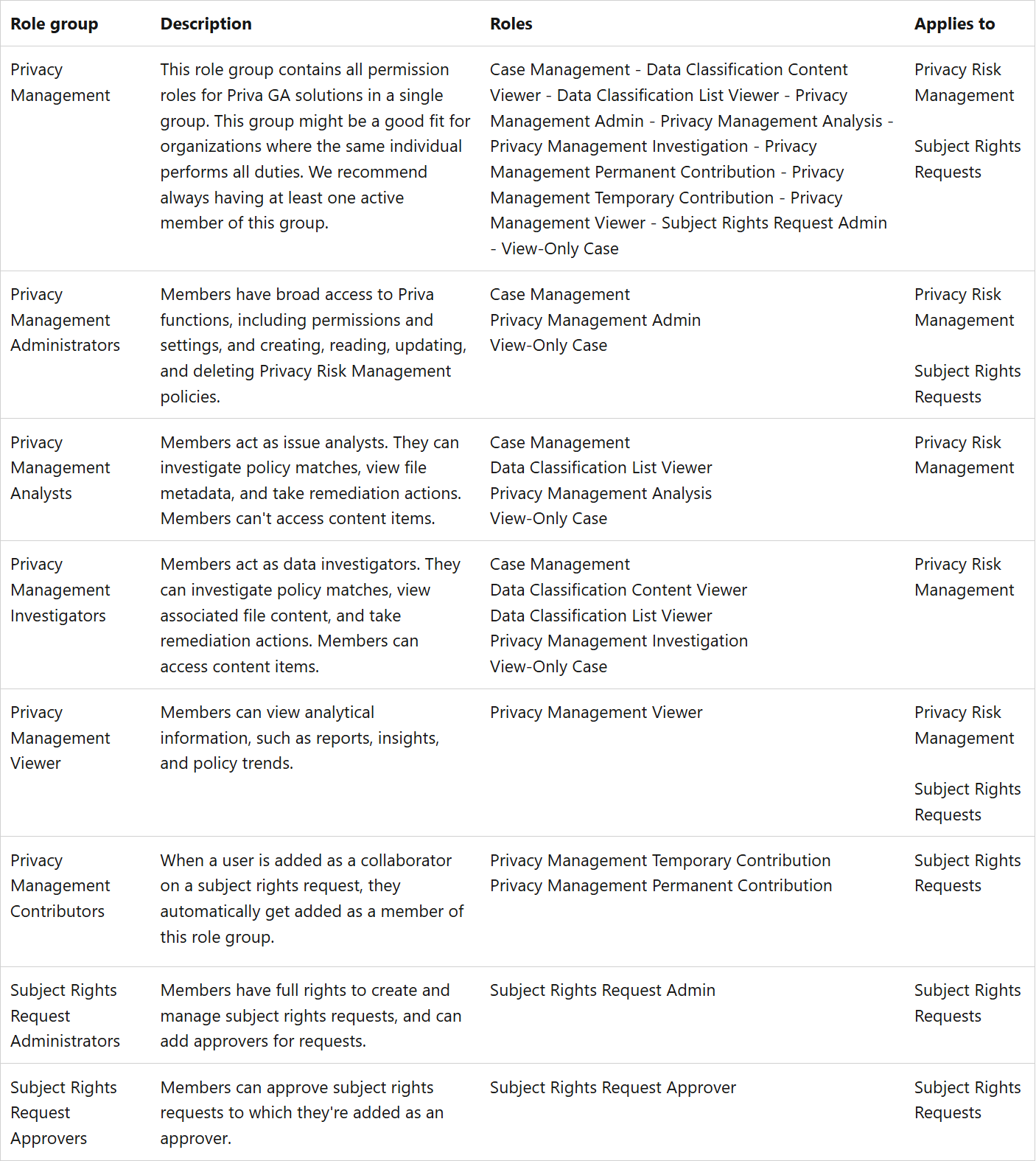
Reference: Get started with Priva
Question: 350
Measured Skill: Manage insider and privacy risk in Microsoft 365 (15–20%)
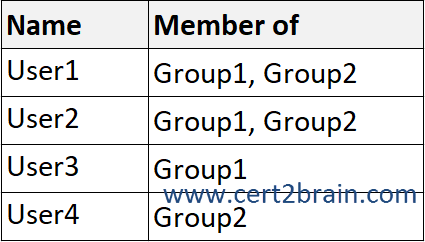
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
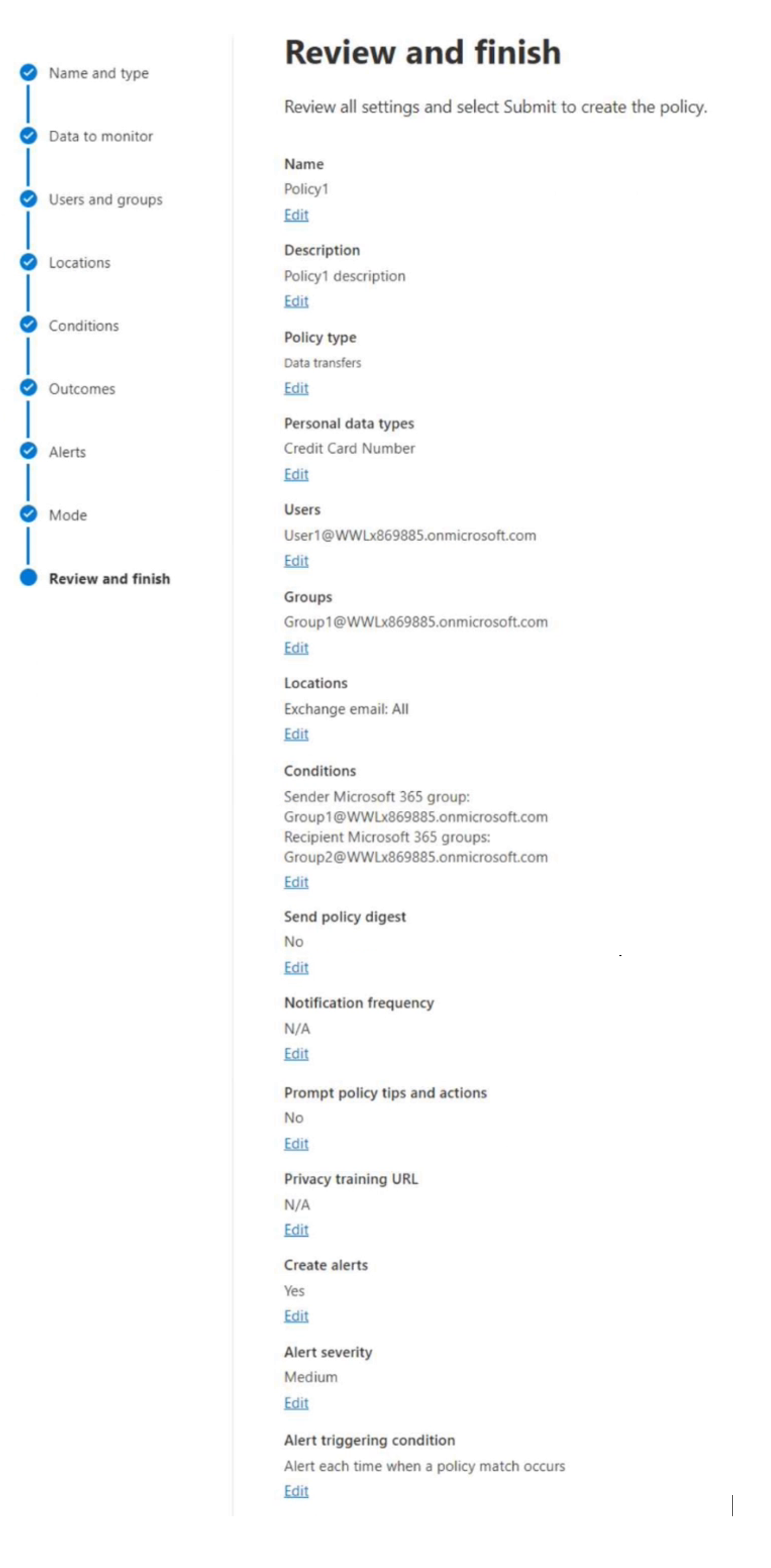
You have a Privacy Risk Management policy named Policy1 based on the Data transfers template as shown in the following exhibit.
User1 sends the following email messages that contain credit card information:
- Message1: Sent to User2.
- Message2: Sent to User3.
- Message3: Sent to User4.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
(NOTE: Each correct selection is worth one point.)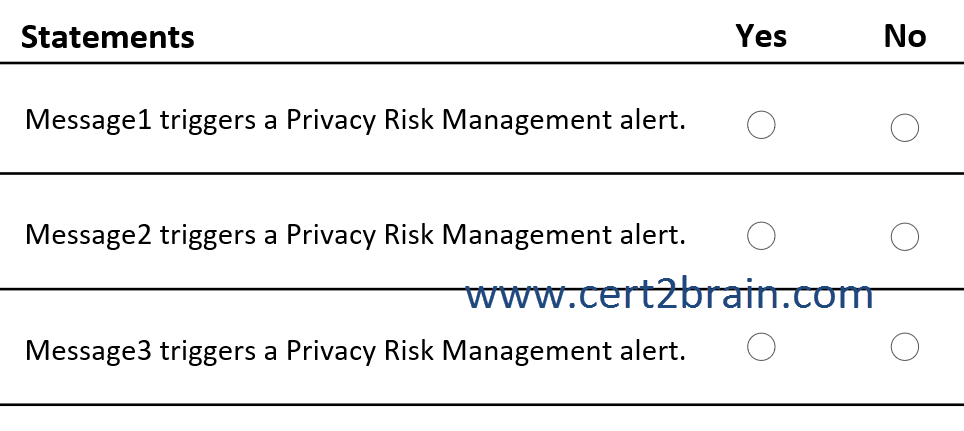
| A | Message1 triggers a Privacy Risk Management alert: Yes
Message2 triggers a Privacy Risk Management alert: Yes
Message3 triggers a Privacy Risk Management alert: Yes |
| B | Message1 triggers a Privacy Risk Management alert: Yes
Message2 triggers a Privacy Risk Management alert: Yes
Message3 triggers a Privacy Risk Management alert: No |
| C | Message1 triggers a Privacy Risk Management alert: Yes
Message2 triggers a Privacy Risk Management alert: No
Message3 triggers a Privacy Risk Management alert: Yes |
| D | Message1 triggers a Privacy Risk Management alert: No
Message2 triggers a Privacy Risk Management alert: Yes
Message3 triggers a Privacy Risk Management alert: Yes |
| E | Message1 triggers a Privacy Risk Management alert: No
Message2 triggers a Privacy Risk Management alert: No
Message3 triggers a Privacy Risk Management alert: Yes |
| F | Message1 triggers a Privacy Risk Management alert: No
Message2 triggers a Privacy Risk Management alert: No
Message3 triggers a Privacy Risk Management alert: No |
Correct answer: CExplanation:
Privacy Risk Management policies based on the Data transfer template can detect personal data transfers across boundaries that you determine, which could involve transfers outside of your organization, or internal transfers across departments or geographic regions. When matches are found, you can set up notifications encouraging senders to revoke access to the content.
Policy1 applies to User1 and Group1 and triggers alerts with medium severity for all email messages that contain credit card information and are sent from members of Group1 to members of Group2.
References:
Privacy risk management policies
Data transfer policies in privacy risk management
Question: 351
Measured Skill: Manage insider and privacy risk in Microsoft 365 (15–20%)
You have a Microsoft 365 E5 subscription that uses Microsoft Purview.
You create a sensitive information type (SIT) named SIT1.
You plan to create the communication compliance policies shown in the following table.
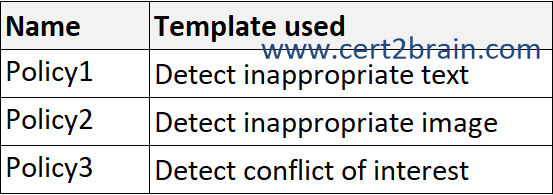
To which policies can you add SIT1 as a condition?| A | Policy1 only |
| B | Policy3 only |
| C | Policy1 and Policy2 only |
| D | Policy1 and Policy3 only |
| E | Policy1, Policy 2, and Policy3 |
Correct answer: BExplanation:
Microsoft Purview Communication Compliance is an insider risk solution that helps minimize communication risks by helping you detect, capture, and act on potentially inappropriate messages in your organization.
You can choose from the following policy templates in the Microsoft Purview compliance portal:
- Detect inappropriate text: Use this template to quickly create a policy that uses built-in classifiers to automatically detect text in messages that may be considered inappropriate, abusive, or offensive.
- Detect inappropriate images: Use this template to quickly create a policy that uses built-in classifiers to automatically detect content that contains adult and racy images that may be considered as inappropriate in your organization.
- Detect sensitive info types: Use this template to quickly create a policy to check communications containing defined sensitive information types or keywords to help make sure that important data isn't shared with people that shouldn't have access.
- Detect financial regulatory compliance: Use this template to quickly create a policy to check communications for references to standard financial terms associated with regulatory standards.
- Detect conflict of interest: Use this template to quickly create a policy to detect communications between two groups or two users to help avoid conflicts of interest.
- Custom policy: Use this template to configure specific communication channels, individual detection conditions, and the amount of content to detect and review in your organization.
- User-reported messages policy: This system policy supports user reported messages from channel, group, and private chat messages. Enabled by default in the Teams admin center.
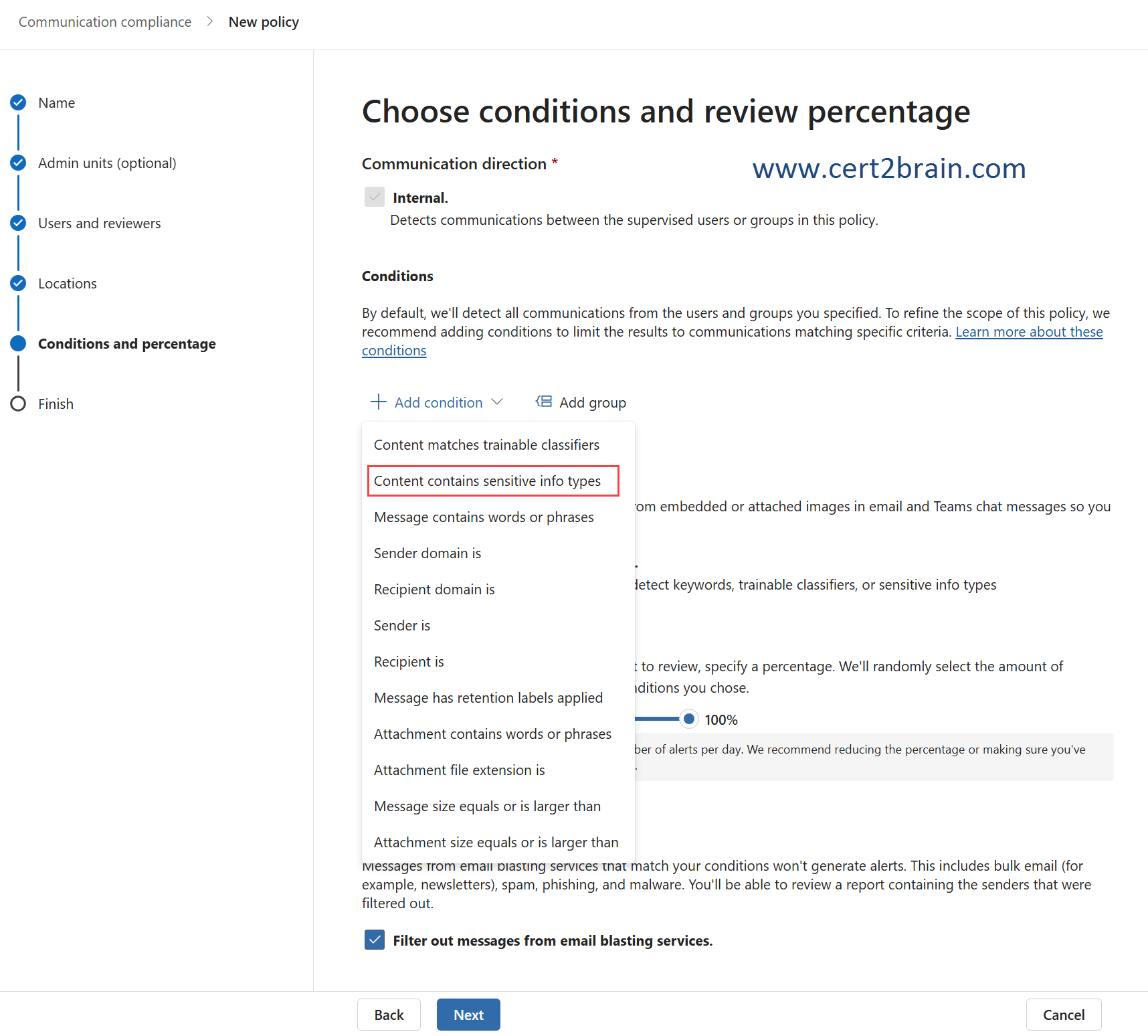
Of the three templates available, Detect conflict of interest is the only one that supports the Content contains sensitive infor types condition as shown below.
References:
Learn about communication compliance
Create and manage communication compliance policies
Question: 352
Measured Skill: Manage insider and privacy risk in Microsoft 365 (15–20%)
You have a Microsoft 365 E5 subscription.
You plan to create the Microsoft Priva Privacy Risk Management policies shown in the following table.
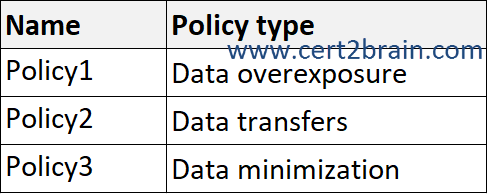
Which policies can you apply to Microsoft Exchange Online email, and which policies can you apply to Microsoft SharePoint Online sites?
(To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.)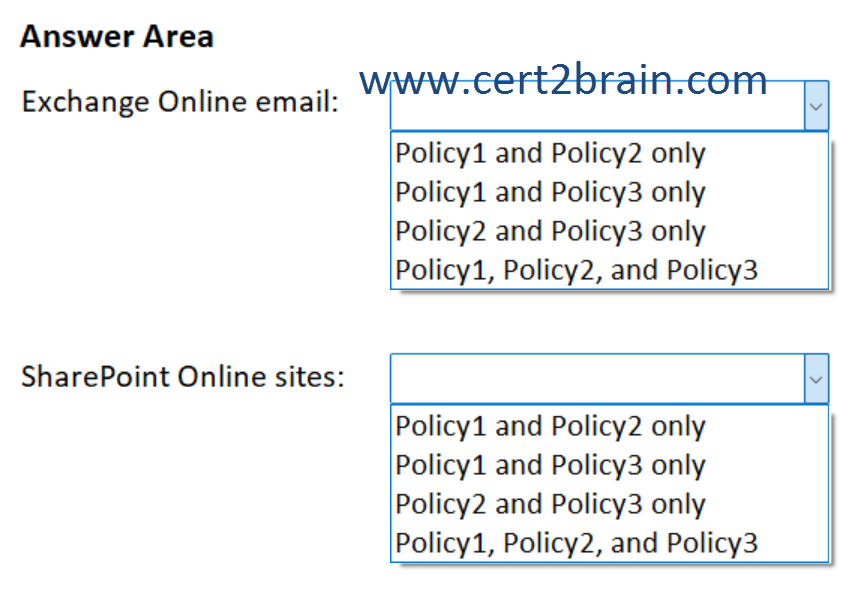
| A | Exchange Online email: Policy1 and Policy2 only
SharePoint Online sites: Policy2 and Policy3 only |
| B | Exchange Online email: Policy1 and Policy3 only
SharePoint Online sites: Policy1 and Policy2 only |
| C | Exchange Online email: Policy1 and Policy3 only
SharePoint Online sites: Policy2 and Policy3 only |
| D | Exchange Online email: Policy2 and Policy3 only
SharePoint Online sites: Policy1, Policy2, and Policy3 |
| E | Exchange Online email: Policy1, Policy2, and Policy3
SharePoint Online sites: Policy1 and Policy3 only |
| F | Exchange Online email: Policy1, Policy2, and Policy3
SharePoint Online sites: Policy1, Policy2, and Policy3 |
Correct answer: DExplanation:
Privacy Risk Management has three policy templates designed to help you address key areas of concern around protecting personal data. Each template has default settings that you can accept in the quick setup process, or customize using a guided process. When you create a new policy, your first task is to choose one of the three templates:
Data overexposure: This policy identifies content items containing personal data that could be too broadly accessible by other people. When matches are found, you can set up notifications prompting content owners to quickly apply protection. This policy provides multicloud data location settings (preview) for Azure Storage, Azure SQL, and Amazon S3.
Data transfers: This policy can detect personal data transfers across boundaries that you determine, which could involve transfers outside of your organization, or internal transfers across departments or geographic regions. When matches are found, you can set up notifications encouraging senders to revoke access to the content.
Data minimization: This policy identifies content items containing personal data that have been untouched for long periods of time. When matches are found, you can send notifications to content owners prompting them to take quick action to keep or delete the item.
Policies based on the Data overexposure template can be applied to SharePoint sites and OneDrive accounts.
Policies based on the Data transfers template or the Data minimization template can be applied to Exchange email accounts, OneDrive accounts, Teams chat and channel messages, and SharePoint sites.
References:
Privacy risk management policies
Data overexposure policies in Privacy Risk Management
Data transfer policies in privacy risk management
Data minimization policies in privacy risk management
Question: 353
Measured Skill: Manage insider and privacy risk in Microsoft 365 (15–20%)
You have a Microsoft 365 E5 subscription the uses Microsoft Priva.
You plan to create the Privacy risk management policies shown in the following table.
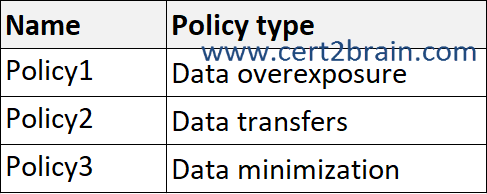
Which policies can send email notifications, and which policies can show policy tips in Microsoft Teams when a policy match is detected?
(To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.)
| A | Can send email notifications: Policy2 only
Can show policy tips in Teams: Policy1 and Policy2 only |
| B | Can send email notifications: Policy1 and Policy2 only
Can show policy tips in Teams: Policy3 only |
| C | Can send email notifications: Policy1 and Policy2 only
Can show policy tips in Teams: Policy1 only |
| D | Can send email notifications: Policy1 and Policy3 only
Can show policy tips in Teams: Policy2 and Policy3 only |
| E | Can send email notifications: Policy2 and Policy3 only
Can show policy tips in Teams: Policy1 and Policy2 only |
| F | Can send email notifications: Policy1, Policy2, and Policy3
Can show policy tips in Teams: Policy2 only |
Correct answer: FExplanation:
Privacy Risk Management has three policy templates designed to help you address key areas of concern around protecting personal data. Each template has default settings that you can accept in the quick setup process, or customize using a guided process. When you create a new policy, your first task is to choose one of the three templates:
Data overexposure: This policy identifies content items containing personal data that could be too broadly accessible by other people. When matches are found, you can set up notifications prompting content owners to quickly apply protection. This policy provides multicloud data location settings (preview) for Azure Storage, Azure SQL, and Amazon S3.
Data transfers: This policy can detect personal data transfers across boundaries that you determine, which could involve transfers outside of your organization, or internal transfers across departments or geographic regions. When matches are found, you can set up notifications encouraging senders to revoke access to the content.
Data minimization: This policy identifies content items containing personal data that have been untouched for long periods of time. When matches are found, you can send notifications to content owners prompting them to take quick action to keep or delete the item.
All three policies can send email notifications. Only policies based on the Data transfers template can show in-the-moment tips in Microsoft Teams that bring users' attention to safe data handling practices.
References:
Privacy risk management policies
Data overexposure policies in Privacy Risk Management
Data transfer policies in privacy risk management
Data minimization policies in privacy risk management